It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
Caled I have another weird book cover and Gates is involved again. Since I am still locked out could you put it up for me if you get a chance?
Thanks.
HAIL MARY by Andy Weir.
Houston we have a problem...
H [triangle] IL
M [triangle] ry
Billy recommends this book on his gates notes blog, as if we care what books he reads.
He is still sooo fixated with dimming the sun. I know crazy when I see it. I have experience. According to "said daughter" Florida is still in Japan. She knows. She's there.
The book is $17.32 on Amazon.
Inversion of Gates plans: " A lone astronaut must save the Earth from disaster and if he fails humanity and the Earth will perish." His mission is to reverse a stellar dimming.
No ordinary crusader Ryland Grave is a former microbiologist who was placed in an induced coma. Sounds a bit like the Corona punishment in the hospitals. Seems we have a theme going here.
He is just so desperate to exterminate us.
Round two of the extinction level threat to our species.
The book is a Hugo Award finalist.
Fun Fact >Gematria? Bush dies, midterm election, Ronald W. Regan, rand paul, steeling, Act of War, undersea, a skyfall, War Games, pneumonia, A NEW HOPE, God's gift.
Billy must be worried. Definition of Hail Mary "A long, typically unsuccessful pass made in a desperate attempt to score late in the game."
His other top recommendation: Klara and the Sun. Robots become companions for isolated humans.
www.gematrinaor.com>calculator
www.gatesnotes.com>Books>Project-Hail-Mary
www.amazon.com>Project-Hail-Mary-Andy-W...
HAIL MARY by Andy Weir.
Houston we have a problem...
H [triangle] IL
M [triangle] ry
Billy recommends this book on his gates notes blog, as if we care what books he reads.
He is still sooo fixated with dimming the sun. I know crazy when I see it. I have experience. According to "said daughter" Florida is still in Japan. She knows. She's there.
The book is $17.32 on Amazon.
Inversion of Gates plans: " A lone astronaut must save the Earth from disaster and if he fails humanity and the Earth will perish." His mission is to reverse a stellar dimming.
No ordinary crusader Ryland Grave is a former microbiologist who was placed in an induced coma. Sounds a bit like the Corona punishment in the hospitals. Seems we have a theme going here.
He is just so desperate to exterminate us.
Round two of the extinction level threat to our species.
The book is a Hugo Award finalist.
Fun Fact >Gematria? Bush dies, midterm election, Ronald W. Regan, rand paul, steeling, Act of War, undersea, a skyfall, War Games, pneumonia, A NEW HOPE, God's gift.
Billy must be worried. Definition of Hail Mary "A long, typically unsuccessful pass made in a desperate attempt to score late in the game."
His other top recommendation: Klara and the Sun. Robots become companions for isolated humans.
www.gematrinaor.com>calculator
www.gatesnotes.com>Books>Project-Hail-Mary
www.amazon.com>Project-Hail-Mary-Andy-W...
twitter.com...
On Wednesday, the Department of Energy, the Cybersecurity and Infrastructure Security Agency, the NSA, and the FBI jointly released an advisory about a new hacker toolset potentially capable of meddling with a wide range of industrial control system equipment.
More recently, the Russian hackers known as Sandworm, part of the Kremlin's GRU military intelligence agency, deployed a tool called Industroyer or Crash Override to trigger a blackout in the Ukrainian capital of Kyiv in late 2016.
The next year, Kremlin-linked hackers infected systems at the Saudi Arabian oil refinery Petro Rabigh with a piece of malware known as Triton or Trisis, which was designed to target its safety systems—with potentially catastrophic physical consequences—but instead triggered two shutdowns of the plant's operations.
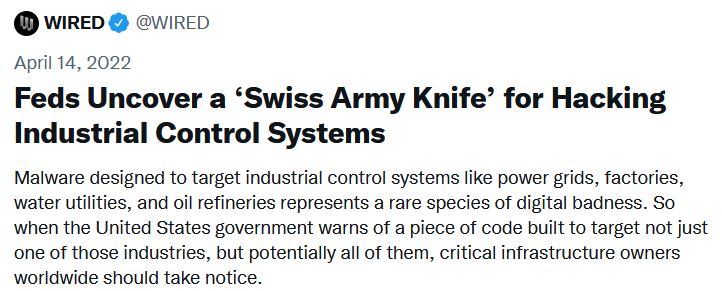
PIPEDREAM (WIRED article)
Stuxnet 2.0?
CHERNOVITE’s PIPEDREAM Malware Targeting Industrial Control Systems (ICS)
PIPEDREAM is the seventh known industrial control system (ICS)-specific malware. The CHERNOVITE Activity Group (AG) developed PIPEDREAM. PIPEDREAM is a modular ICS attack framework that an adversary could leverage to cause disruption, degradation, and possibly even destruction depending on targets and the environment.
Dragos identified and analyzed PIPEDREAM’s capabilities through our normal business, independent research, and collaboration with various partners in early 2022. Dragos assesses with high confidence that PIPEDREAM has not yet been employed in the wild for destructive effects.
CHERNOVITE’s PIPEDREAM can execute 38 percent of known ICS attack techniques and 83 percent of known ICS attack tactics.1
PIPEDREAM accomplishes this far-reaching impact through a series of five components that Dragos labels:
✅ EVILSCHOLAR
✅ BADOMEN
✅ DUSTTUNNEL
✅ MOUSEHOLE
✅ LAZYCARGO

Hmmm, PIPEDREAM? And now a word from our sponsor...




originally posted by: Thoughtful1
Caled I have another weird book cover and Gates is involved again. Since I am still locked out could you put it up for me if you get a chance? Thanks.
HAIL MARY by Andy Weir.
ya reply to: Caled
Thank you. Caleb call me crazy but HILLARY??? See the Capital H leave out the triangle. Next letter is I. Then L
Next line m=miss, triangle, a. Then r and y. >Hilary.
Why am I not surprised. Gates and Hillary fan club.
#1. Falling in a pit of fire/hell. Since they are satanists that is the inversion of heaven.
#2. The triangles.
#3. Ring of Fire. Think The Ring of Fire by Johnny Cash. "And it burns, burns burns, the ring of fire."
The patch. Gold circle device I was dealing with much earlier. That is no coincidence. But there must be something more important about that patch. Do you know what it means?
Thank you. Caleb call me crazy but HILLARY??? See the Capital H leave out the triangle. Next letter is I. Then L
Next line m=miss, triangle, a. Then r and y. >Hilary.
Why am I not surprised. Gates and Hillary fan club.
#1. Falling in a pit of fire/hell. Since they are satanists that is the inversion of heaven.
#2. The triangles.
#3. Ring of Fire. Think The Ring of Fire by Johnny Cash. "And it burns, burns burns, the ring of fire."
The patch. Gold circle device I was dealing with much earlier. That is no coincidence. But there must be something more important about that patch. Do you know what it means?
Just sooo many.
What was Biden up to on World Health Day???
April 7, 2022 [4+7+2+4=you know]
"We are doubling down on our commitment to meet our 2030 goals to end the AIDS plandemic"
Heading to the Fact Sheet Statement and Releases.
The Biden administration only wants $17 billion.
Lots of really strange funding but this one is fun>
1. $2.47 billion in mandatory funding for CDC enhanced DOMESTIC SURVEILLANCE programs.
2.The Bill Gates favorite expansion of domestic and global waste water surveillance. After all through the Bill and Melinda Gates Foundation he did fund research in this area and now it's payback time. He is full of a waste water special.
Are we having fun yet?
***Investments in genomic surveillance. !!! Why? Anything to do with some genetic mutations caused by the jabs???
The CDC is to transition what they developed during the Covid wars and enhance their techniques and devices.
Another fun area after all Biden himself telegraphed the food shortages. Just for them but not for we $1.7 billion in Emergency Food Aid via FOOD FOR PEACE TITLE II.
The war of the 17's continues.
www.whitehouse.gov>2022/04/07>statement Go to the bottom for the Fact Sheet Statement and Releases for the 2023 budget
What was Biden up to on World Health Day???
April 7, 2022 [4+7+2+4=you know]
"We are doubling down on our commitment to meet our 2030 goals to end the AIDS plandemic"
Heading to the Fact Sheet Statement and Releases.
The Biden administration only wants $17 billion.
Lots of really strange funding but this one is fun>
1. $2.47 billion in mandatory funding for CDC enhanced DOMESTIC SURVEILLANCE programs.
2.The Bill Gates favorite expansion of domestic and global waste water surveillance. After all through the Bill and Melinda Gates Foundation he did fund research in this area and now it's payback time. He is full of a waste water special.
Are we having fun yet?
***Investments in genomic surveillance. !!! Why? Anything to do with some genetic mutations caused by the jabs???
The CDC is to transition what they developed during the Covid wars and enhance their techniques and devices.
Another fun area after all Biden himself telegraphed the food shortages. Just for them but not for we $1.7 billion in Emergency Food Aid via FOOD FOR PEACE TITLE II.
The war of the 17's continues.
www.whitehouse.gov>2022/04/07>statement Go to the bottom for the Fact Sheet Statement and Releases for the 2023 budget
arstechnica.com...
The Project Hail Mary mission patch, depicting Sol, Earth, Tau Ceti, and the names of the ship's crew.
Chinese surname Yao
en.wikipedia.org...(surname)
Russian surname Ilyukhina
en.wikipedia.org...
The Project Hail Mary mission patch, depicting Sol, Earth, Tau Ceti, and the names of the ship's crew.
Chinese surname Yao
en.wikipedia.org...(surname)
Russian surname Ilyukhina
en.wikipedia.org...
originally posted by: Thoughtful1
ya reply to: Caled
Thank you. Caleb call me crazy but HILLARY??? See the Capital H leave out the triangle. Next letter is I. Then L
Next line m=miss, triangle, a. Then r and y. >Hilary.
Why am I not surprised. Gates and Hillary fan club.
#1. Falling in a pit of fire/hell. Since they are satanists that is the inversion of heaven.
#2. The triangles.
#3. Ring of Fire. Think The Ring of Fire by Johnny Cash. "And it burns, burns burns, the ring of fire."
The patch. Gold circle device I was dealing with much earlier. That is no coincidence. But there must be something more important about that patch. Do you know what it means?
They made me stop playing. I was winning, and I wasn't supposed to.
That game isn't what anyone thinks it is.
That game isn't what anyone thinks it is.
originally posted by: XtheMadnessNow
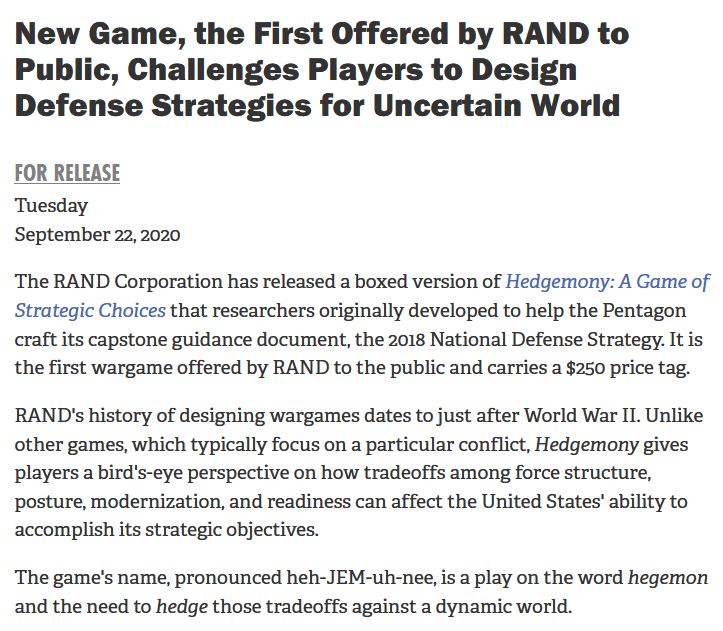
Shall we play a game? How about a nice game of heh-JEM-uh-nee.
edit on 4/15/2022 by Caled because: (no reason given)
a reply to: Caled
Whatever a player chooses, their goal is to gain more influence—within a certain region or throughout the world—than their competitors. The game requires 5 facilitators.

Hedgemony was on RAND's list of top 10 most popular research projects for 2020. The #1 most poppular RAND research of 2020...“Quarantine,” “social distancing,” and “flatten the curve.” Shocking but not surprised.
Funding to produce the game in a format useful for a broader policy making audience was provided by gifts from RAND supporters and income from operations.
Hedgemony is a pedagogical wargame designed for U.S. defense strategy and policy professionals, as well as graduate school faculty and students in related fields of study.
In a separate PDF downoad they offer a listing of (real world) acronyms & abbreviations for the game. From a quick scan of interest:
Whatever a player chooses, their goal is to gain more influence—within a certain region or throughout the world—than their competitors. The game requires 5 facilitators.

Hedgemony was on RAND's list of top 10 most popular research projects for 2020. The #1 most poppular RAND research of 2020...“Quarantine,” “social distancing,” and “flatten the curve.” Shocking but not surprised.
Funding to produce the game in a format useful for a broader policy making audience was provided by gifts from RAND supporters and income from operations.
Hedgemony is a pedagogical wargame designed for U.S. defense strategy and policy professionals, as well as graduate school faculty and students in related fields of study.
In a separate PDF downoad they offer a listing of (real world) acronyms & abbreviations for the game. From a quick scan of interest:
DIME (Diplomatic, Information, Military, and Economic)
DIME is a framework that emerged from U.S. military academia for characterizing powers that a state may use to influence outcomes in the world.
The term "gray zone" might be new, but the phenomenon is not. Although many of the techniques used now are based on modern technology, notably cyber and networked communication, many are as old as history. What are now being called gray zone methods have been conducted in the past under such names as “political warfare,” “covert operations,” “irregular warfare,” “guerrilla warfare,” “active measures,” and the like.
The "White Cell" is the team of people administering and facilitating the game on behalf of the players.
Christian
Relic on Sunken Russian Ship
For those of you interested in any spiritual bends as they relate to world events. I found this noteworthy.
For those of you interested in any spiritual bends as they relate to world events. I found this noteworthy.
edit on 15-4-2022 by
SideEyeEverything because: (no reason given)
Durham writes of ‘spoofed’ data, Clinton
‘conspiracy’
Interesting timing.... ...
Q last post date - π- Biden transition team started to perform a deep clean .... Too little too late
We also see that these high-tech spies were able to penetrate one of Mr. Trump’s Wi-Fi routers. In all, the group assembled by tech executive Rodney Joffe snatched proprietary internet traffic from Trump Tower, Mr. Trump’s Central Park West apartment building and the Trump White House in early 2017.
What is impressive is the sheer effort by Clinton devotees in 2016 to take a mass of inconclusive data and try to convince themselves and the FBI that Mr. Trump was a Russian agent.
Mr. Durham branded the entire group under the heading of “co-conspirators” — a tag he did not apply in the original September 2021 indictment.
Interesting timing.... ...
Q last post date - π- Biden transition team started to perform a deep clean .... Too little too late
edit on 4152022 by MetalThunder because: TIME is what you make of IT
originally posted by: SideEyeEverything
For those of you interested in any spiritual bends as they relate to world events. I found this noteworthy.
Lets add this to that list
TGIGF
edit on 4152022 by MetalThunder because: TIME is what you make of IT
a reply to: MetalThunder
So, that's why Notre Dame burned.
In other digging news...
twitter.com...
Why would Putin force Joseph Robinette Biden to stutter and say these things?
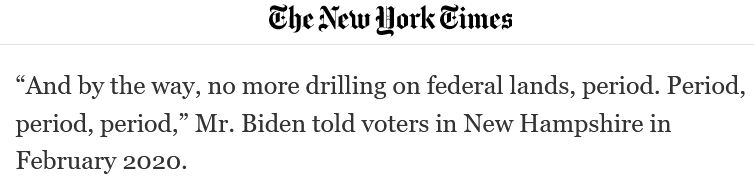
Biden Plans to Open More Public Land to Drilling (from same article as in the tweet)
So, that's why Notre Dame burned.
In other digging news...

twitter.com...
Why would Putin force Joseph Robinette Biden to stutter and say these things?

Biden Plans to Open More Public Land to Drilling (from same article as in the tweet)
a reply to: RelSciHistItSufi
Hi rel.
“Mirroring” seems to have become an integral part of the decodes.
I’m not sure of its full significance, but it has given me something to think about.
When I look in a mirror I get an objective reflection, flaws and all. It can be quite different from how I think of myself. The image itself is reversed, so there is even an element of opposition.
It reminds me that most of the things I have learned about life I have learned from people different from myself. When people totally agree with me, I learn nothing. But when they disagree, there is an interaction, a questioning, a debate. It exposes me to a different perspective and forces me to consider its validity. They don’t follow me blindly, and they don’t force me to submit to their opinion, but I am exposed to ideas that come from outside of myself, and my consideration of those ideas becomes a part of me.
This is similar to the Socratic Method:
“The Socratic method (also known as Socratic debate) is a form of cooperative argumentative dialogue between individuals, based on asking and answering questions to stimulate critical thinking and to draw out ideas and underlying presuppositions.”
The method starts with division and works with it.
On the other hand, Q has said a lot about unity. But society is more divided than ever. The achieving of unity seems impossible.
But maybe unity does not mean complete agreement in every detail. Not at all. Perhaps unity is the result of a process, without submission or coercion, with all the information out in the open, whereby pros and cons are considered and a workable solution is arrived at that includes room for reasonable differences in opinion.
With respect to the Great Awakening, perhaps an issue is not completely processed until it is mirrored and its contrary is considered and evaluated.
There is no way everyone can be brought into complete agreement. But I am reminded that children argue, while mature adults work things through (ideally).
Could this be a positive variation of "order out of chaos," as in "growth out of division?" If we can all get focused, motivated by adversity, on the importance of getting along, our differences may become less contentious.
Perhaps waking up is just the prelude to growing up.
.
Hi rel.
“Mirroring” seems to have become an integral part of the decodes.
I’m not sure of its full significance, but it has given me something to think about.
When I look in a mirror I get an objective reflection, flaws and all. It can be quite different from how I think of myself. The image itself is reversed, so there is even an element of opposition.
It reminds me that most of the things I have learned about life I have learned from people different from myself. When people totally agree with me, I learn nothing. But when they disagree, there is an interaction, a questioning, a debate. It exposes me to a different perspective and forces me to consider its validity. They don’t follow me blindly, and they don’t force me to submit to their opinion, but I am exposed to ideas that come from outside of myself, and my consideration of those ideas becomes a part of me.
This is similar to the Socratic Method:
“The Socratic method (also known as Socratic debate) is a form of cooperative argumentative dialogue between individuals, based on asking and answering questions to stimulate critical thinking and to draw out ideas and underlying presuppositions.”
The method starts with division and works with it.
On the other hand, Q has said a lot about unity. But society is more divided than ever. The achieving of unity seems impossible.
But maybe unity does not mean complete agreement in every detail. Not at all. Perhaps unity is the result of a process, without submission or coercion, with all the information out in the open, whereby pros and cons are considered and a workable solution is arrived at that includes room for reasonable differences in opinion.
With respect to the Great Awakening, perhaps an issue is not completely processed until it is mirrored and its contrary is considered and evaluated.
There is no way everyone can be brought into complete agreement. But I am reminded that children argue, while mature adults work things through (ideally).
Could this be a positive variation of "order out of chaos," as in "growth out of division?" If we can all get focused, motivated by adversity, on the importance of getting along, our differences may become less contentious.
Perhaps waking up is just the prelude to growing up.
.
Official McAfee....teedotme.....
AS WITHIN SO WITHOUT
THROUGH THE STARS
TO THE FATHERS HOUSE WE GO;
***I CALL IT ---SAVING GRACE***
***NEWS FLASH***
::::THE ENTIRE WORLD IS COMPROMISED:::
::::VVE GAVE YOU A CHANCE W/ THE AUDITS TO
DO THE RIGHT THING:::
::::THE FLOOD IS COMING:::
****31TB OF DATA****
::::NOTHING STOPS THIS:::
::::WE SEE AND HEAR ALL:::
HOW????
WE ARE THE BEST!!!
THE ETERNITY & FOREVER GROUP;
*******PANIC*******
:::REPARE FOR 12 YEARS OF *TRUMP:::
*****PANIC IS GOOD*****
***WITCH HUNT***
***WITCH HUNT***
****WITCH HUNT***
WATCH FAKE NEWS FOX NEXT 48 HOURS:
FLIP FLIP FLIP
“THE ALIENS AR3 AMONG US”
FLIP FLIP FLIP
‘THEYVE B3EN HERE THE ENTIRE TIME—-RUN!!!”
FLIP FLIP FLIP
*****PANIC INCREASE RAT POPULATION*****
LISTEN:
WE R THE #ING BEST EVER!!!
RUN RUPERT (twitter.com...) RUN!!! RUN QUICK!!
DONT LOOK BACK BECAUSE
IAM COMING QUICKLY
MY BRIDE IS W/ ME;
4LPHA AND OM3GA;
LIGHT & D4RKNESS;
THE SUN & THE MOON;
THE FIRST & LAST
KEY 2 THE STARZZZ;
IAM THE ROOT OF OSIRIS;
THE EYE OF HORUS;
THE LIVING ONE;
THE PARADISE GROUP;
TREAD LIGHTLY. . .
FOLLOW ME & YOU
WILL LIVE FOR3V3R IN THE LAND
OF FOR3V3R.
ONLY IF YOU TRULY BELI3V3…
LIFE IS GOOD;;;
JUST CHILL JUST CHILL JUST CHILL
RELAX YQUR TIME HAS CQME.
JUST CHILL[z];;;
DONT EVER FORGET THE WORDS;
MyRRH MYrRH MRyRH
MRYrH MYRRh MYRRh.
JUST CHILLLLLLL.. . . .…. … LIFe IS GOOd;
DONT EVER FORGET WHERE U COME FROM!!!!
& DONT EVER GIVE UP!!!
7YRR4PTUR37YRS4LV4TION
0-100 REAL QUICK
ALL IN THE *BLINK* OF AN EYE
*TRUMP *TRUMP *TRUMP
*TRUMP *TRUMP *TRUMP
FLIP FLIP FLIP
FILP FLIP FILP FILP FLIP FLIPYDHKSK!!
WE ARE THE #ING BESTttt OK!!!11
we’re the best,
N.C.S.VV.I.C,,
TseB EHE eR’eW,,,
AgAIN AgAIN,,,,
We’Re ThE BeSt,,,,,
Just Chill;…………. . .. . . . ….. …
THOSE WHO KNOW CANT SL33P;
ONE MORE THING > I FORGIVE YOU JOHN (twitter.com...);
YOU DID THE RIGHT THING. . .
VVE HAVE IT ALL;
LAST KEYS 2 THE VAULT;
TICK TOCK;
WWG1VVGA;
A 6000 YR LOVE STORY;
TOGETHER AGAIN AT LAST;
TOGETHER FOREVER AGAIN;
TOGETHER WE R
Q
AS WITHIN SO WITHOUT
THROUGH THE STARS
TO THE FATHERS HOUSE WE GO;
***I CALL IT ---SAVING GRACE***
***NEWS FLASH***
::::THE ENTIRE WORLD IS COMPROMISED:::
::::VVE GAVE YOU A CHANCE W/ THE AUDITS TO
DO THE RIGHT THING:::
::::THE FLOOD IS COMING:::
****31TB OF DATA****
::::NOTHING STOPS THIS:::
::::WE SEE AND HEAR ALL:::
HOW????
WE ARE THE BEST!!!
THE ETERNITY & FOREVER GROUP;
*******PANIC*******
:::REPARE FOR 12 YEARS OF *TRUMP:::
*****PANIC IS GOOD*****
***WITCH HUNT***
***WITCH HUNT***
****WITCH HUNT***
WATCH FAKE NEWS FOX NEXT 48 HOURS:
FLIP FLIP FLIP
“THE ALIENS AR3 AMONG US”
FLIP FLIP FLIP
‘THEYVE B3EN HERE THE ENTIRE TIME—-RUN!!!”
FLIP FLIP FLIP
*****PANIC INCREASE RAT POPULATION*****
LISTEN:
WE R THE #ING BEST EVER!!!
RUN RUPERT (twitter.com...) RUN!!! RUN QUICK!!
DONT LOOK BACK BECAUSE
IAM COMING QUICKLY
MY BRIDE IS W/ ME;
4LPHA AND OM3GA;
LIGHT & D4RKNESS;
THE SUN & THE MOON;
THE FIRST & LAST
KEY 2 THE STARZZZ;
IAM THE ROOT OF OSIRIS;
THE EYE OF HORUS;
THE LIVING ONE;
THE PARADISE GROUP;
TREAD LIGHTLY. . .
FOLLOW ME & YOU
WILL LIVE FOR3V3R IN THE LAND
OF FOR3V3R.
ONLY IF YOU TRULY BELI3V3…
LIFE IS GOOD;;;
JUST CHILL JUST CHILL JUST CHILL
RELAX YQUR TIME HAS CQME.
JUST CHILL[z];;;
DONT EVER FORGET THE WORDS;
MyRRH MYrRH MRyRH
MRYrH MYRRh MYRRh.
JUST CHILLLLLLL.. . . .…. … LIFe IS GOOd;
DONT EVER FORGET WHERE U COME FROM!!!!
& DONT EVER GIVE UP!!!
7YRR4PTUR37YRS4LV4TION
0-100 REAL QUICK
ALL IN THE *BLINK* OF AN EYE
*TRUMP *TRUMP *TRUMP
*TRUMP *TRUMP *TRUMP
FLIP FLIP FLIP
FILP FLIP FILP FILP FLIP FLIPYDHKSK!!
WE ARE THE #ING BESTttt OK!!!11
we’re the best,
N.C.S.VV.I.C,,
TseB EHE eR’eW,,,
AgAIN AgAIN,,,,
We’Re ThE BeSt,,,,,
Just Chill;…………. . .. . . . ….. …
THOSE WHO KNOW CANT SL33P;
ONE MORE THING > I FORGIVE YOU JOHN (twitter.com...);
YOU DID THE RIGHT THING. . .
VVE HAVE IT ALL;
LAST KEYS 2 THE VAULT;
TICK TOCK;
WWG1VVGA;
A 6000 YR LOVE STORY;
TOGETHER AGAIN AT LAST;
TOGETHER FOREVER AGAIN;
TOGETHER WE R
Q
originally posted by: Thoughtful1
a reply to: cimmerius
I am thinking that the Keystone is shipping container fleets/companies in general. Obviously we have the Evergreen connection.
Around July 3rd last year I made a brief post about the odd names of ships in the Maersk shipping line.
I should expand on this. Just a few names but to me it sounds like an army of ships.
#17 Searcher #98 Ocean Trader [human trafficking]
Here are some of the names so you can tell me what you think: Handler, Seeker, Supplier, Server, Attender, Chancellor, Beater, Battler, Helper, Dispatcher, Detector, Tracer, Tracker, LAUNCHER, Detector, Installer, Involver, Implementer, Mobilizer, Mover, Minder.
In what is a name game this sounds to me like a military operation. Ships named for specific functions hidden within the fleet of 708 container ships.
As you pointed out, those seem like some unusual names. I wonder how they compare with the names of ships from other lines.
They do sound like roles or functions, rather than being named after people, things, or places.
My first association was that they sound like the names of mind control alters. (fragmented personality functions) Or not.
It seems unlikely that they would be the names of each ship’s specific function. It’s hard to see how ships could do all those different things. Ships are also very trackable. But we are learning that much of the corruption does take place at an industrial scale larger than imagined.
It is possible that the names represent aspects of the shipping business or the various involvements of the shipping line’s overall operations. Some of those operations could be nefarious. The people who do these things seem to love subtly bragging about it in the open.
.
Whiplash347 on teedotme....
I knew long ago..
The INCREDIBLE drop is not IRAN but ISRAEL
HITLER was a ROTHSCHILD PAWN
ISRAEL IS LAST - BALFOUR DECLARATION.
Death to ZION/NAZI Collaboration.
#OperationZ
MOSSAD did 9/11 Sanctioned by QUEEN OF ENGLAND.
Queen owns Saudi Intel as well.
Saudi was flipped in 2017 but it started in 2012.
I knew long ago..
The INCREDIBLE drop is not IRAN but ISRAEL
HITLER was a ROTHSCHILD PAWN
ISRAEL IS LAST - BALFOUR DECLARATION.
Death to ZION/NAZI Collaboration.
#OperationZ
MOSSAD did 9/11 Sanctioned by QUEEN OF ENGLAND.
Queen owns Saudi Intel as well.
Saudi was flipped in 2017 but it started in 2012.
new topics
-
Is this really what is going on?
General Conspiracies: 21 minutes ago -
Russias War Against Religion in Ukraine
World War Three: 1 hours ago -
iPhone Microphone Being Accessed by Unknown App
The Gray Area: 3 hours ago -
Democrats send letter to Biden urging him to ratify Equal Rights Amendment
US Political Madness: 9 hours ago
top topics
-
iPhone Microphone Being Accessed by Unknown App
The Gray Area: 3 hours ago, 9 flags -
Democrats send letter to Biden urging him to ratify Equal Rights Amendment
US Political Madness: 9 hours ago, 3 flags -
Russias War Against Religion in Ukraine
World War Three: 1 hours ago, 2 flags -
Is this really what is going on?
General Conspiracies: 21 minutes ago, 2 flags
active topics
-
Drones everywhere in New Jersey ---and Elsewhere Master Thread
Aliens and UFOs • 179 • : Ravenwatcher -
Is this really what is going on?
General Conspiracies • 4 • : Nickn4 -
Only two Navy destroyers currently operational as fleet size hits record low
Military Projects • 30 • : Oldcarpy2 -
Russias War Against Religion in Ukraine
World War Three • 4 • : berbofthegreen -
iPhone Microphone Being Accessed by Unknown App
The Gray Area • 1 • : mysterioustranger -
Democrats send letter to Biden urging him to ratify Equal Rights Amendment
US Political Madness • 6 • : Cvastar -
music for the apocalypse
Music • 25 • : Hellmutt -
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 7915 • : underpass61 -
George Stephanopoulos and ABC agree to pay $15 million to settle Trump defamation suit
Mainstream News • 26 • : Lazy88 -
Mood Music Part VI
Music • 3736 • : Hellmutt