It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
1ofthe9
GUT - don't be too hard on yourself man. We've all had those moments I think.
Thanks, brother, that is so kind. I'm really beating myself up.
1ofthe9
Goddamn I need a cigarette.
You didn't do something stupid like clicking the OK button did you!!
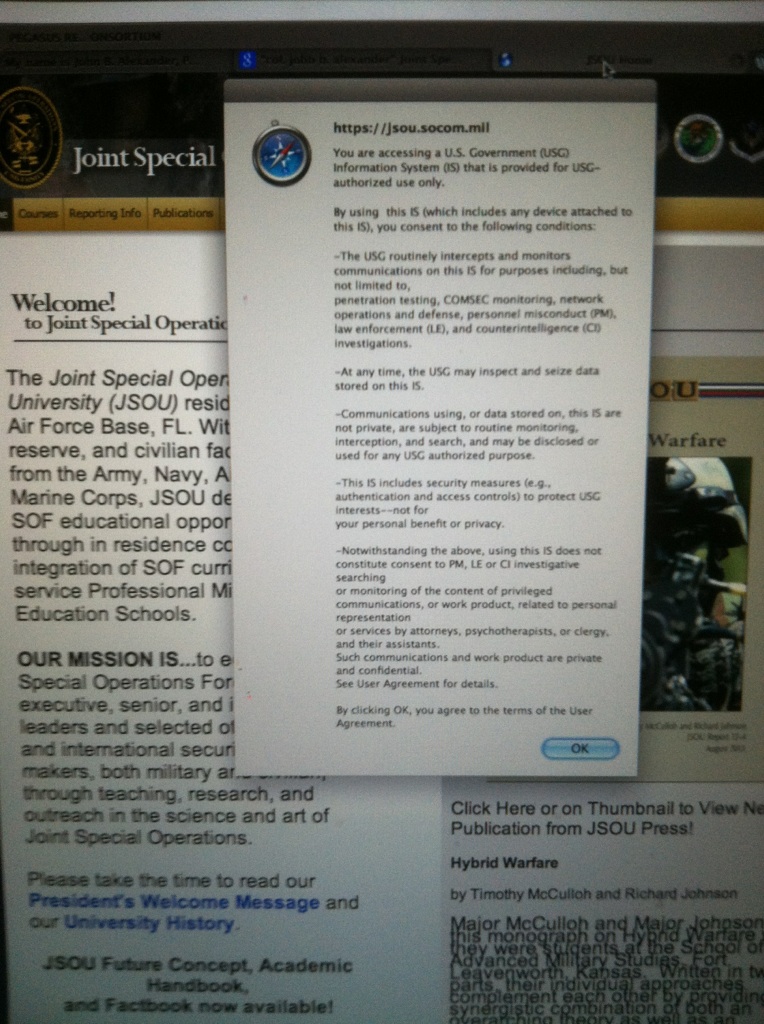
Here's my screenshot, btw, 'cause nobody probably wants to click ANYTHING now:
edit on 30-1-2014 by The GUT because: (no reason given)
The GUT
1ofthe9
GUT - don't be too hard on yourself man. We've all had those moments I think.
Thanks, brother, that is so kind. I'm really beating myself up.
Dude, seriously, no worries.
At first I was like what the hell, but then it was like "whatever".
If that's what they want they'll just take it anyways.
So I just added a little revolutionary music to the mix for them.
Chew on that, pigs.
Haha!
Here's how I broke it down on MIB(OPs) from the Alexander AMA:
While some of Col. John B. Alexander's answers to other folk's questions on his AMA thread were personally interesting to me, I found the thread--not surprisingly--somewhere on the dark side of the illumination continuum.
The issues that both 727Sky and I were addressing pertain to Col. John B. Alexander's support and logistical papers concerning his positive perception of, and strategic-planning, as regards the blending of Military force/tactics/training/weaponry and State Police units in anticipation of who knows what. We don't know "what" because he hasn't told us.
First a little satire:
Q: What about a JFK conspiracy, Colonel?
A: Bollocks!! Conspiracy nuts!!
Q: Can you be more clear about those amazing Shamanistic experiences you referenced in your introduction?
A: Some small, round stones on the ground, erm, and a coin we found in our tent. MAGIC!!
So was the bullet, John, so was the bullet. Or so we've been told.
Okay, now for the entire exchange starting with a great question by 727Sky and my attempts at follow up.
727Sky gets the ball rolling:
Col. Alexander's response:
After encouraging him to answer 727Sky's questions, my response:
Col. Alexander's reply:
After following his advice and going to the Joint Special Operations University web site to access that paper once and for all, my response:
Screenshots:

Col. Alexander's reply:
Col. Alexander did seem possibly--maybe--sincerely baffled as to why I'm experiencing those screens. If he is truly baffled, all I can say is that I picked up the attention on his website when I was doing continuing research on this thread and it follows me as I attempt to follow him and research his views.
Back on Point: Does it seem as if the major/points and questions asked of the Colonel might be a touchy subject? Neither Sky727's to the point questions nor my own about the blending of military and state police units and their relation to Constitutional issues received a response.
Were those questions sidestepped on the permanent and public AMA thread or is it just me?
While some of Col. John B. Alexander's answers to other folk's questions on his AMA thread were personally interesting to me, I found the thread--not surprisingly--somewhere on the dark side of the illumination continuum.
The issues that both 727Sky and I were addressing pertain to Col. John B. Alexander's support and logistical papers concerning his positive perception of, and strategic-planning, as regards the blending of Military force/tactics/training/weaponry and State Police units in anticipation of who knows what. We don't know "what" because he hasn't told us.
First a little satire:
Q: What about a JFK conspiracy, Colonel?
A: Bollocks!! Conspiracy nuts!!
Q: Can you be more clear about those amazing Shamanistic experiences you referenced in your introduction?
A: Some small, round stones on the ground, erm, and a coin we found in our tent. MAGIC!!
So was the bullet, John, so was the bullet. Or so we've been told.
Okay, now for the entire exchange starting with a great question by 727Sky and my attempts at follow up.
727Sky gets the ball rolling:
John your thoughts on the militarization of the police forces and ad hock organizations tasked for crowd control inside the U.S. borders. Is this a normal evolution of cause and effect or have the inside circles of power that you might be aware of deemed it is essential for the survival of the republic or their own power structures? There have been many articles about all the alphabet agencies being armed and around here one report of the government buying over 1.7 billion rounds of hollow point ammo got many people's attention.. Comment if you care to or have an opinion?
Like you I have the benefit of a long hindsight which to my memory never included a Swat team plus backup for something that before was taken care of by a Mayberry Sherriff…?
Col. Alexander's response:
On my web site you'll find an entire monograph on this topic. I'll be writing more about it shortly - probably in my HP blog.
After encouraging him to answer 727Sky's questions, my response:
My question is, if you refer to the paper you co-authored with your son: Why, when I tried to access that paper from your website last year, while compiling the thread linked below, did I get a pop-up that basically stated something along the lines of "By accessing this file you give the DOD permission to permanently access and scan your hard-drive…" ??
The pop up froze my computer. Thusly, I'm hesitant to go to your site and attempt a download again…
Col. Alexander's reply:
I have not had that problem. There are both the monograph I wrote and a shorter piece co-authored with Mark. The monograph can also be accessed through the Joint Special Operations University web site and is available to the public.
After following his advice and going to the Joint Special Operations University web site to access that paper once and for all, my response:
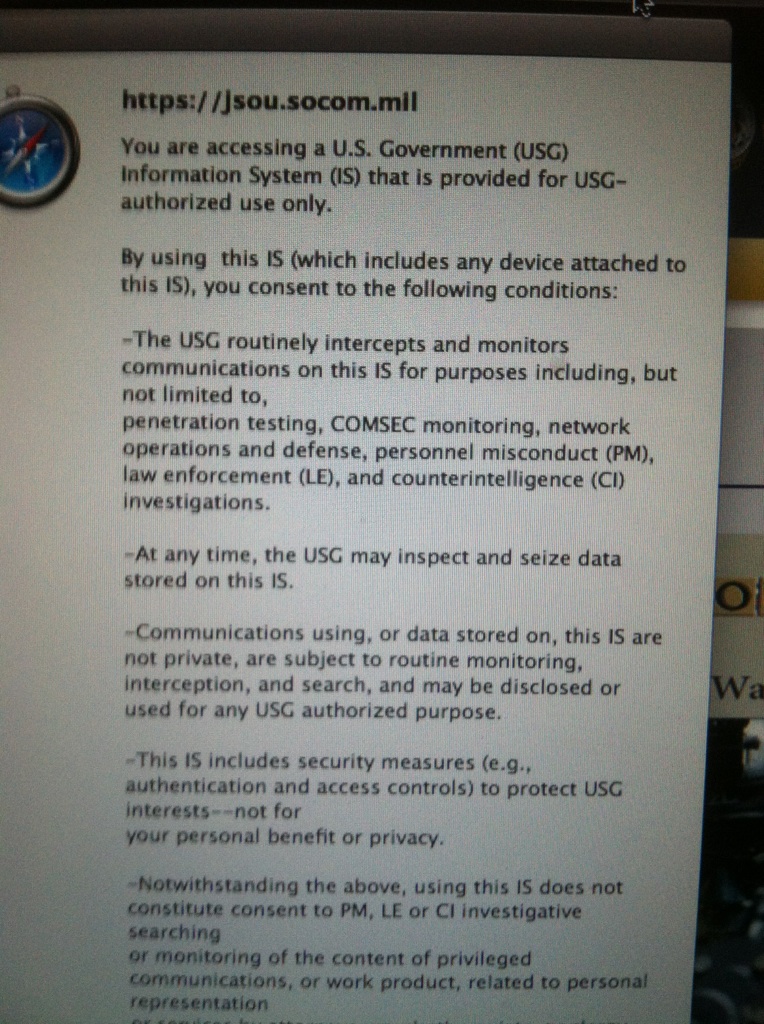
When trying to access that document as per your reply at the Joint Special Operations University, I ran into a similar--though not exact--persistent pop-up screen that once again wants access to my computer. I've attached pics below. Imo, that's not exactly "public access" if I have to give consent to search.
I think the question that we want some kind of real response to regards the Constitutional questions raised by the blending of military tactics, training, and gear--both lethal and non-lethal--and state police forces. The whys and wherefores and just what kind of "forecasts" can justify the rhetoric.
Could you give us the title of both your monograph and that of the article co-authored with your son, Mark?
Thank You, Sir.
Screenshots:


Col. Alexander's reply:
send me a private email from my web site and I'll try to get you the info. Not sure why there is a problem
Col. Alexander did seem possibly--maybe--sincerely baffled as to why I'm experiencing those screens. If he is truly baffled, all I can say is that I picked up the attention on his website when I was doing continuing research on this thread and it follows me as I attempt to follow him and research his views.
Back on Point: Does it seem as if the major/points and questions asked of the Colonel might be a touchy subject? Neither Sky727's to the point questions nor my own about the blending of military and state police units and their relation to Constitutional issues received a response.
Were those questions sidestepped on the permanent and public AMA thread or is it just me?
edit on 30-1-2014 by The GUT because: (no reason given)
I checked with some friends who like to haunt these sites. The pop ups are a result of viewing the website from a non-DoDNet terminal. Could explain
why Alexander wasn't familiar with it.
1ofthe9
I checked with some friends who like to haunt these sites. The pop ups are a result of viewing the website from a non-DoDNet terminal. Could explain why Alexander wasn't familiar with it.
Makes sense. Thanks.
reply to post by The GUT
Absolutely they were sidestepped
Again "joint readiness".
In this case instead of SOFA we are talking feds working with city law dog to corral you and I. Of course he supports the idea because power corrupts
He wouldn't make a good politician, but he would make a good advisor.
He reminds me of Palpatine
Absolutely they were sidestepped
Again "joint readiness".
In this case instead of SOFA we are talking feds working with city law dog to corral you and I. Of course he supports the idea because power corrupts
He wouldn't make a good politician, but he would make a good advisor.
He reminds me of Palpatine
reply to post by JayinAR
To be fair, after some more prodding, he did eventually answer. Something about terroism, rioting, and the homeland type stuff. Hrmmm.
To be fair, after some more prodding, he did eventually answer. Something about terroism, rioting, and the homeland type stuff. Hrmmm.
edit on 30-1-2014 by The GUT because: (no reason given)
I SWEAR I'm basically on topic Ms. Cairo. At least the part about those intelligence folk close to Vallee (Green, Alexander, Puthoff) and how
they--being closely associated with the SERPO and MJ-12 memes--might be doing a little "control system" work over information networks.

HUGE NEWS and AboveTopSecret.com Moves To the Next Level!
Them cats is everywhere ufological memes are sold!
It is with GREAT PLEASURE and PRIDE that we announce the addition of Dr Christopher "Kit" Green to the AboveTopSecret.com Team.
Dr. Green is not only one of the most congenial, genuine and PLEASANT gentlemen I've ever spoken with he is without question one of the TOP Forensic Medicine, Radiology, and Psychiatry & Behavioral Neurosciences and fMRI geniuses alive on this planet.

HUGE NEWS and AboveTopSecret.com Moves To the Next Level!
Them cats is everywhere ufological memes are sold!
edit on 30-1-2014 by The GUT because: (no reason given)
I gleaned a curious name today rereading Final Events.
Scientific Engineering Institute.
They funded a sorcery course at the University of South Carolina in the early 1970's. Apparently they were the public face of MK OFTEN. Anyone heard the name?
Scientific Engineering Institute.
They funded a sorcery course at the University of South Carolina in the early 1970's. Apparently they were the public face of MK OFTEN. Anyone heard the name?
reply to post by The GUT
And that is exactly my own take on matters.
After reading Mirage Men, think who has their hands on the levers. Is Doty the trickster, the fool, or perhaps a far more powerful player than people would dare to imagine? Why is Doty at the centre of so many major UFO events of the past 40 years? How does someone like Pilkington investigating the 'Mirage Men' perhaps become another Mirage Maker?
Hypnotised by both Doty and Green, deeply ensconced in the control system.
And that is exactly my own take on matters.
After reading Mirage Men, think who has their hands on the levers. Is Doty the trickster, the fool, or perhaps a far more powerful player than people would dare to imagine? Why is Doty at the centre of so many major UFO events of the past 40 years? How does someone like Pilkington investigating the 'Mirage Men' perhaps become another Mirage Maker?
Hypnotised by both Doty and Green, deeply ensconced in the control system.
edit on 30-1-2014 by cuckooold because: (no reason given)
reply to post by cuckooold
I still recommend Mirage Men, but you're right: Pilkington did come away looking like a sucker. Or worse. Maybe Kit gave him an free fMRI haha.
I still recommend Mirage Men, but you're right: Pilkington did come away looking like a sucker. Or worse. Maybe Kit gave him an free fMRI haha.
edit on 30-1-2014 by The GUT because: (no reason given)
Alright, I see now.
I feel like I woke up in a slightly alternate reality though. On the list of people who do not inspire free-of-control-agenda names, Green is... well he's up there. And now he's something at ATS? I thought they actually worked to keep the forum free of all that? I feel like I must be profoundly misunderstanding something.
Totally next topic: did you ever read John Lilly's autobiography? It seriously made me think our black ops is way, way ahead of us in hardware (hard wire!) for human influence compared to what we suspect. And that was decades ago, just imagine.
Back to control schemas: so isn't the primary "buying into" of all the various control schemas, that we just keep listening to, hanging on, to what the oh-so-obviously-playing-us personalities from former intell/agency have to say?
I feel like I woke up in a slightly alternate reality though. On the list of people who do not inspire free-of-control-agenda names, Green is... well he's up there. And now he's something at ATS? I thought they actually worked to keep the forum free of all that? I feel like I must be profoundly misunderstanding something.
Totally next topic: did you ever read John Lilly's autobiography? It seriously made me think our black ops is way, way ahead of us in hardware (hard wire!) for human influence compared to what we suspect. And that was decades ago, just imagine.
Back to control schemas: so isn't the primary "buying into" of all the various control schemas, that we just keep listening to, hanging on, to what the oh-so-obviously-playing-us personalities from former intell/agency have to say?
reply to post by RedCairo
Some of these concepts that are being tossed around by the failed
sorcerer spies are over 5,000 years old; hailing back to the indus
valley civilization.
I don't get the fascination.
Some of these concepts that are being tossed around by the failed
sorcerer spies are over 5,000 years old; hailing back to the indus
valley civilization.
I don't get the fascination.
RedCairo
Alright, I see now.
I feel like I woke up in a slightly alternate reality though. On the list of people who do not inspire free-of-control-agenda names, Green is... well he's up there. And now he's something at ATS? I thought they actually worked to keep the forum free of all that? I feel like I must be profoundly misunderstanding something.
Totally next topic: did you ever read John Lilly's autobiography? It seriously made me think our black ops is way, way ahead of us in hardware (hard wire!) for human influence compared to what we suspect. And that was decades ago, just imagine.
Back to control schemas: so isn't the primary "buying into" of all the various control schemas, that we just keep listening to, hanging on, to what the oh-so-obviously-playing-us personalities from former intell/agency have to say?
I actually read Delgado's book today. It was really remarkable what they could do back then.
The subculture makes a convenient testing ground for belief system control experiments. That and data-mining for predictive computational modeling of 'threats'. Too many keywords and such and bam: off to gitmo. The American/Western/whatever TPTB convinced that they are locked into some kind of long term confrontation with radical Islam. They are planning for the long term, and to be fair seem aware of the biological threat. But oh man, what they want long term. Synthetic immune systems, 'protected' agriculture against agrobiowar bugs, etc. Kit Green was also into Alternate Reality Games - so these guys are into some pretty nifty things. Terrifying things.
reply to post by RedCairo
I'm only saying--out loud anyway--that Kit has a professional interest in ufological memes. Let's look at the following again:
In the article titled Is Uncle Sam a Closet Ufologist? by respected investigative journalist Gus Russo we find some interesting information pertaining to our subject from a fellow called by the pseudonym, "Jim" who has been identified by various researchers as Dr. Christopher "Kit" Green. You'll probably reconize him yourself by the mini-bio:
I'm only saying--out loud anyway--that Kit has a professional interest in ufological memes. Let's look at the following again:
In the article titled Is Uncle Sam a Closet Ufologist? by respected investigative journalist Gus Russo we find some interesting information pertaining to our subject from a fellow called by the pseudonym, "Jim" who has been identified by various researchers as Dr. Christopher "Kit" Green. You'll probably reconize him yourself by the mini-bio:
Then there is Jim, whose professional history in the subject goes back to his personal involvement in the Stargate project in the 1970’s and as a participant in the legendary “Working Group” meetings in the eighties. As one of the intel community’s most senior medical analysts, Jim frequently communicates with UFOlogists.
Chris Iverson believes that Tom and Jim clearly have differing agendas, noting, “Jim is the person I have had the most contact with over the last several months and he seems to be interested in the spreading of viral memes over the internet, particularly in relation to this subject.”…
“The whole subject,” Jim says in wonderfully measured speech, “is composed of three components: delusion, sociological groupthink, and a kernel of truth.” Jim then reminds that he is first and foremost a medical scientist. “My interest in this subject is much, much more professional than it is personal. That is, 90 to 95% of all persons who are engaged fully with this [UFO] subject are psychiatrically ill, and by that I mean that they are on medication or should be.”
Jim elaborates that “viral memes,”[see below] in which disturbed people seek validation in numbers on the web, is, or should be, a growing public health concern. That said, Jim nonetheless has a real interest in UFO’s, and seemingly with good reason.
Both Tom and Jim seem to share at least one rationale for their internet excursions: studying the frightening potential of “viral internet memes.”
Coined by evolutionary theorist Richard Dawkins in 1976 (The Selfish Gene), a meme is a unit of cultural information that evolves the way a gene propagates from one organism to another, and subject to all the analogous unintended mutations. In the view of many, computers and blogs could function as powerful meme “replicators.”
Richard Brodie, the creator of Microsoft Word, notes, “Most of these viruses of the mind are spread because they are intriguing or frightening or inspiring, and not necessarily because they're true. That's the problem.” It doesn’t take much intuition to envision an enemy creating memes that can be used to destabilize a society, or a freelance predator utilizing them to cozy up to potential victims. Caryn Anscomb writes online,
“The UFO community has been deeply penetrated by the manipulators of information, who couldn’t really give a fig whether there might be any valuable data pertaining to Aliens and contact hidden behind the deafening noise. That’s not their business; their business is information warfare.”
www.bibliotecapleyades.net...
edit on 30-1-2014 by The GUT because: (no reason given)
RedCairo
Totally next topic: did you ever read John Lilly's autobiography? It seriously made me think our black ops is way, way ahead of us in hardware (hard wire!) for human influence compared to what we suspect. And that was decades ago, just imagine.
No, I haven't read it, but I definitely will now. Thank you. I have read that Lilly tried to keep his research "pure" but that it was basically a losing battle. Don't know if that's true or not.
The GUT
We're in a box here, for example, on this very forum. Even in many senses a "closed loop". lakespirit (he's a real up & comer here, eh?!) gave not only an awesome example with explanatory power using Eidolon's model, but detailed how easy it would be to collate, track, compare, and extrapolate information in a forum environment. And even use that information to manipulate. It would seem a no-brainer for any scientist/sociologists, eh?

All right, guys, it's been a blast, but this is probably gonna be my swan song.
The Pseudo-Control System, by E23
Once upon a time in America, there were millions of well-armed veterans who didn't trust the government. A lot of them were socially isolated, hadn't reintegrated all that well (there aren't many services or institutions that see to this glaring need). Many of them believed in Alex Jones, and others like him, many of them believed in aliens. A majority of them had internet access. Left to their own devices, they might go all Tim McVeigh on the joint, or worse, all William Wallace.
(Not that a William Wallace scenario would pan out, but it would be a pain in the ass and a PR nightmare to contain.)
So, you construct a system(s) where they can be regulated and managed through narrative control, as well provide as a vent for idle/frustrated/lonely minds. Give them a choice (hopefully a dichotomous one, as people take to two clear-cut selections over ambivalence) of narratives to subscribe to, and drop just enough innocuous truth into the mix to make the "disclosure" satisfying enough to staunch serious attempts at further inquiry.
The people who walked away satisfied that their pet narrative has been "proven" yet again were neutralized, and the Tim McVeighs in the audience who identified themselves are noted for future reference. Additionally, the control system provides a test bed for narrative constructs that can be tuned up and deployed elsewhere.
Promising input that departed from the master narratives being fed to the userbase was quashed or overrun with calculated irrelevance and dead ends.
The userbase has been shifting somewhat of late, started to incorporate some of the Occupy crowd, who are considered a potential nuisance in a completely different way, but are, conveniently enough, adopting the exact same narratives that have been used on the restless vets for the past two decades. That's nice, makes the job of corralling them a little easier, but you still have to make some concessions to youth, and promote the hell out of the new guy who you think will resonate with the kids.
This whole system is lazy and small-hearted, but cheaper than funding the services and instigating the changes that would alleviate the perceived threat altogether.
All right, guys, ya'll take good care of yourselves.

Incredible! I think we owe either you, Eidy, or Bybyots for the following about DARPA and control through "narrative." Then for anyone unfamiliar
please take note of some of the DIA TIGER Study goals. TIGER was chaired by Kit Green:
DARPA put out a call fairly recently that is pretty clear on the objectives they are seeking--and why--in the following research project. DARPA was also clear they weren't looking for the same ol', same' ol' and were looking to further what's already known about influencing and controlling societal segments.
This makes sense because while social engineering and it's related modalities have come a long way, the techniques only work to a certain degree and on a certain percentage of society.
We can see here at our very own ATS that you can fool some of the people some of the time, but not all of the people all of the time. The "un-fooled" as it were, presents the biggest problem, say,if you are trying to occupy and "democratize" various Middle Eastern nations.
What's also interesting is that these studies are speaking more and more of Homeland Security and problems of "radicalization" here in the U.S.
Fisrt we'll take alook at the DARPA call for submissions, then we'll dig a little deeper into the TIGER study.
According to DARPA, STORyNET has three goals:
Now back to TIGER of which, we'll remember, Dr. Christopher "Kit" Green was Chair. All Bolding mine.
The broader range of various UFO "communities" & issues not only provide convenient test beds, but also contain ready made modalities that can be studied. As an aside before we look at the next item, we'll make brief mention of another so-called Aviary member, Col. John B. Alexander.
Col. Alexander pretty much puts his kibosh on the notion that Alien Abductions are real. He sees it as a mental phenomenon. It's interesting that he also put together at least one conference on the subject and has many contacts within that subset of ufology. He and Dr. Green are also involved in a number of Homeland Security issues/projects to include what we often refer to as the military-industrial complex. Okay, back to TIGER and Alien Abductions:
"The allure of such research has been so great...," is a very telling statement and the word "allure" is a word of exceptional emphasis.
The TIGER study is suggestive. The quoted material from Gus Russo's Is Uncle Sam a Closet Ufologist? is suggestive. The Core Story tale along with Vallee's comments in Forbidden Science, Journal II is suggestive. Valle's and Green's friendship along with an interest in memes, modern myth, manipulating the "control system," and internet philosophy--again, suggestive. Those things aren't only suggestive, they "agree." It's that very "agreement" which seems to me to indicate that "social engineering" is a frontrunner for what SERPO and other issues discussed here is really about.
DARPA put out a call fairly recently that is pretty clear on the objectives they are seeking--and why--in the following research project. DARPA was also clear they weren't looking for the same ol', same' ol' and were looking to further what's already known about influencing and controlling societal segments.
This makes sense because while social engineering and it's related modalities have come a long way, the techniques only work to a certain degree and on a certain percentage of society.
We can see here at our very own ATS that you can fool some of the people some of the time, but not all of the people all of the time. The "un-fooled" as it were, presents the biggest problem, say,if you are trying to occupy and "democratize" various Middle Eastern nations.
What's also interesting is that these studies are speaking more and more of Homeland Security and problems of "radicalization" here in the U.S.
Fisrt we'll take alook at the DARPA call for submissions, then we'll dig a little deeper into the TIGER study.
DARPA is soliciting innovative research proposals in the areas of (1) quantitative analysis of narratives, (2) understanding the effects narratives have on human psychology and its affiliated neurobiology, and (3) modeling, simulating, and sensing-especially in stand-off modalities-these narrative influences. Proposers to this effort will be expected to revolutionize the study of narratives and narrative influence by advancing narrative analysis and neuroscience so as to create new narrative influence sensors, doubling status quo capacity to forecast narrative influence.
www.fbo.gov...
"Stories exert a powerful influence on human thoughts and behavior. They consolidate memory, shape emotions, cue heuristics and biases in judgment, influence in-group/out-group distinctions, and may affect the fundamental contents of personal identity.
It comes as no surprise that these influences make stories highly relevant to vexing security challenges such as radicalization, violent social mobilization, insurgency and terrorism, and conflict prevention and resolution. Therefore, understanding the role stories play in a security context is a matter of great import and some urgency," DARPA stated. "Ascertaining exactly what function stories enact, and by what mechanisms they do so, is a necessity if we are to effectively analyze the security phenomena shaped by stories. Doing this in a scientifically respectable manner requires a working theory of narratives, an understanding of what role narratives play in security contexts, and examination of how to best analyze stories-decomposing them and their psychological impact systematically."
According to DARPA, STORyNET has three goals:
1. To survey narrative theories. These empirically informed theories should tell us something about the nature of stories: what is a story? What are its moving parts? Is there a list of necessary and sufficient conditions it takes for a stimulus to be considered a story instead of something else? Does the structure and function of stories vary considerably across cultural contexts or is there a universal theory of story?
2. To better understand the role of narrative in security contexts. What role do stories play in influencing political violence and to what extent? What function do narratives serve in the process of political radicalization and how do they influence a person or group's choice of means (such as violence) to achieve political ends? How do stories influence bystanders' response to conflict? Is it possible to measure how attitudes salient to security issues are shaped by stories?
3. To survey the state of the art in narrative analysis and decomposition tools. How can we take stories and make them quantitatively analyzable in a rigorous, transparent and repeatable fashion? What analytic approaches or tools best establish a framework for the scientific study of the psychological and neurobiological impact of stories on people? Are particular approaches or tools better than others for understanding how stories propagate in a system so as to influence behavior?
www.networkworld.com...
Now back to TIGER of which, we'll remember, Dr. Christopher "Kit" Green was Chair. All Bolding mine.
The label “cognitive” in the title and elsewhere in this report is used in the broad sense. Unless otherwise noted, it refers to the cognitive sciences in general and comprises psychological and physiological processes underlying human information processing, emotion, motivation, social influence, and development. It includes contributions from all directly related disciplines, including the behavioral and social sciences, neurogenetics, proteomics, philosophy, mathematics, computer science, and linguistics.
The technology being applied to determine psychological state could even be derived from an incomplete model of brain function as long as it had sufficient predictive power to accomplish the desired goal. For instance, one would not need a complete model of brain function to construct a brain–computer interface that could improve the self-piloting capabilities of unmanned air vehicles. But the tolerance for error will be much less if a technology is used to determine whether an individual is lying about an act of treason, because the consequences of an error will be greater.
The committee believes that it is critical to fully understand the relationship between neurophysiological markers and actual mental states when the application is the detection of deception..
…Mind reading typically refers to the capacity (imparted by an external mechanism—that is, some form of technology) to determine precisely what an individual is thinking or intending, whether or not the individual is willing to communicate that state of mind. As discussed below, to “read” minds scientists must understand how minds really work to come up with a technology that is of real use, and there are several formidable barriers to…
Other questions raised by controlling the mind: How can we make people trust us more? What if we could help the brain to remove fear or pain? Is there a way to make the enemy obey our commands?
…However, the types of experiments being done may be more telling than the type of equipment needed. The same equipment might be needed for medical and for disruptive neuropsychopharmacological experiments. It could be asked, What types of experiments are being done?
How are the experiments being controlled and monitored, and why were they chosen? How would human experimentation be conducted outside accepted informed-consent limits?
www.nap.edu...
In developing the methodology, the committee considered the end user (analysts and predictors of the behaviors of individuals and groups), the data available to them, the desired output, and the unique aspects (if relevant) of neuroscience research. Intelligence analysts were available for consultation throughout the project in order to ensure that the methodology was realistically applied, given the limitations of the data sets.
The broader range of various UFO "communities" & issues not only provide convenient test beds, but also contain ready made modalities that can be studied. As an aside before we look at the next item, we'll make brief mention of another so-called Aviary member, Col. John B. Alexander.
Col. Alexander pretty much puts his kibosh on the notion that Alien Abductions are real. He sees it as a mental phenomenon. It's interesting that he also put together at least one conference on the subject and has many contacts within that subset of ufology. He and Dr. Green are also involved in a number of Homeland Security issues/projects to include what we often refer to as the military-industrial complex. Okay, back to TIGER and Alien Abductions:
An important issue for cognitive neuroscientists concerns efforts to determine whether a person is reporting a true experience or one that is false but believed. In the last decade, there have been innumerable research efforts designed to distinguish true from false memories.
Earlier work examining behavioral differences between true and false memories revealed that group differences were sometimes found (for example, more sensory details in true-memory reports) (Schooler et al., 1986). However, the statistical group differences did not enable reliable classification of any particular memory report as to its authenticity.
Some work with neuroimaging has attempted to locate differences in the brain that might reveal something about true and false memories. The goal of much of the work has been to demonstrate that true and false memories have different neural signatures...
The allure of such research has been so great that considerable effort is likely to be devoted in the future to the neurophysiology of false memory. Despite some progress, we are far from being able to use neuroimaging techniques to tell us about the veracity of particular memories…
"The allure of such research has been so great...," is a very telling statement and the word "allure" is a word of exceptional emphasis.
…A notable exception can be found in the work of Okado and Stark (2005), who examined true and false memories in the context of a misinformation experiment and thus studied richer false memories. Misinformation studies show how readily memory can become skewed when people are fed misinformation…
Richard McNally and his collaborators (McNally, 2003) studied people who had very rich, although likely false, memories of alien abduction have been studied. One study explored whether people who believe they have been abducted exhibit heightened physiological reactivity (heart rate and skin conductance) that occurs commonly in patients who have posttraumatic stress disorder (PTSD) when they think about their traumas.
The “abductees” studied had experienced apparent sleep paralysis and hypnopompic hallucinations, which are vivid dreamlike hallucinations that occur as one is waking up, such as seeing figures hovering near their beds. Most had recovered memories with such techniques as guided imagery and hypnosis. Some of the recovered memories involved sexual intercourse with aliens or having sperm extracted for breeding purposes. Their physiological reactions were similar to those seen in PTSD patients who listen to audiotaped scripts of their traumas. Thus, expressed emotion is no guarantee that a memory is true.
The TIGER study is suggestive. The quoted material from Gus Russo's Is Uncle Sam a Closet Ufologist? is suggestive. The Core Story tale along with Vallee's comments in Forbidden Science, Journal II is suggestive. Valle's and Green's friendship along with an interest in memes, modern myth, manipulating the "control system," and internet philosophy--again, suggestive. Those things aren't only suggestive, they "agree." It's that very "agreement" which seems to me to indicate that "social engineering" is a frontrunner for what SERPO and other issues discussed here is really about.
new topics
-
Of course it was DEI
Dissecting Disinformation: 8 hours ago -
2nd Day Thanksgiving!...(leftovers!!)
General Chit Chat: 10 hours ago
top topics
-
Of course it was DEI
Dissecting Disinformation: 8 hours ago, 6 flags -
2nd Day Thanksgiving!...(leftovers!!)
General Chit Chat: 10 hours ago, 3 flags
active topics
-
I thought Trump was the existential threat?
World War Three • 124 • : andy06shake -
Mass UAP events. DC. Machester Airport, UFOs over sub base in CT, Nuke bases.
Aliens and UFOs • 26 • : CosmicFocus -
Unidentified Flying Objects Over U.S. Military Bases in Northeast UK, as of roughly 11 a.m. CST.
Aliens and UFOs • 34 • : bastion -
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 7850 • : KrustyKrab -
Of course it was DEI
Dissecting Disinformation • 10 • : Dalamax -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 3417 • : brewtiger123 -
2nd Day Thanksgiving!...(leftovers!!)
General Chit Chat • 6 • : DontTreadOnMe -
New Disney Star Wars Films Failing Test of Time?
Movies • 18 • : Popoll -
The Party of Peace - Trump Cabinet Picks Targeted with Death Threats
US Political Madness • 51 • : RazorV66 -
Results of the use of the Oreshnik missile system in Dnepropetrovsk
World War Three • 263 • : DontTreadOnMe
