It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
a reply to: AndyFromMichigan
Hm
It’s depressingly common for members of Congress to serve while facing criminal charges - Vox, May 25, 2017
Elsewhere:
The trouble with prosecuting treason - NY Post Opinion, May 5, 2010.
Treason is a pretty high bar that hasn't been hurdled in quite a while and one tat people are apparently reluctant to attempt.
Hm
Democrats may be up in arms over the idea that Gianforte can serve in the nation’s lower chamber amid criminal charges. But it would actually be a break from precedent if the criminal charge blocked his path to the House.
For instance, Sen. Bob Menendez (D-NJ) was indicted more than two years ago on multiple felony corruption charges. Prosecutors said he took more than $1 million in donations in order to help a Florida ophthalmologist get visas for three of the ophthalmologist’s girlfriends.
...
Rep. Chaka Fattah (D-PA) was indicted on federal racketeering charges in July 2015 and continued to serve for more than a year. Sen. Ted Stevens (R-AK) was indicted in July 2008 on seven counts of failing to properly report gifts, and served for more than five additional months.
...
“There’s no formal process to remove a member. You can be charged and convicted of a crime, and even if you’re in prison you can still serve,” said Josh Huder, a congressional scholar at Georgetown’s Government Affairs Institute, adding that dozens of members have clung to their seats while facing criminal charges.
...
“You can prevent him from being part of the caucus; they can ostracize him. But there’s no formal mechanism to remove him from office outside of impeachment,” Huder said.
It’s depressingly common for members of Congress to serve while facing criminal charges - Vox, May 25, 2017
Elsewhere:
Prosecutions for treason are rare in the United States, with fewer than four dozen such cases brought since our nation’s founding. As noted in “The Heritage Guide to the Constitution,” one reason is that constitutional standards associated with the definition and proof of treason are specific and quite high.
...
Indeed, this war has already brought the first indictment of a US citizen for treason since 1952, on Oct. 11, 2006 — of Adam Gadahn, a k a Adam Pearlman.
Gadahn grew up in California, converted to Islam and moved to Pakistan, where he eventually became a senior commander to Osama bin Laden. As an al Qaeda media adviser, he has appeared in numerous terrorist propaganda videos spewing hatred of and violence toward the nation of his birth. He remains at large.
The trouble with prosecuting treason - NY Post Opinion, May 5, 2010.
Treason is a pretty high bar that hasn't been hurdled in quite a while and one tat people are apparently reluctant to attempt.
a reply to: PokeyJoe
Lots of it has been proven. What are you talking about?
The whole passage about Carter Page to start. Meetings in the Seychelles? Proven. Cohen in Prague? Maybe...not calling that proven... Yet. Manaforts connection to oligarchs? Proven.
I don't have to waste time trying to disprove any of it. If it's not true that will be revealed. Like these things that are true have been revealed.
Lots of it has been proven. What are you talking about?
The whole passage about Carter Page to start. Meetings in the Seychelles? Proven. Cohen in Prague? Maybe...not calling that proven... Yet. Manaforts connection to oligarchs? Proven.
I don't have to waste time trying to disprove any of it. If it's not true that will be revealed. Like these things that are true have been revealed.
originally posted by: TomLawless
a reply to: pavil
They're a part of five eyes. Lots of deep staters frequent/built homes in New Zealand. They can get away from it all, yet still have access to the operation.
I am many pages behind so this may have been mentioned. Kim Dot.com is in NZ. I would guess his mega upload server is there as well. Maybe a leak?
originally posted by: crankyoldman
originally posted by: pavil
originally posted by: dashen
a reply to: pavil
It's not that simple. The server has to have a chain of custody. It has to have been seized legally in order to be admissible as evidence in court.
I wonder if this has anything to do with the raids on the awans
That's what I'm talking about. Having a chain of custody. I have to think, if they have "The Server", what was it for and who would have been in possession of it?
Supposedly some major Obama officials , including the former President were communicating via unofficial Means
.
Remember what back when they were moving Obama's records and such to Chicago for his library? Q seemed to imply they they were in possession of some of it.
Pav,
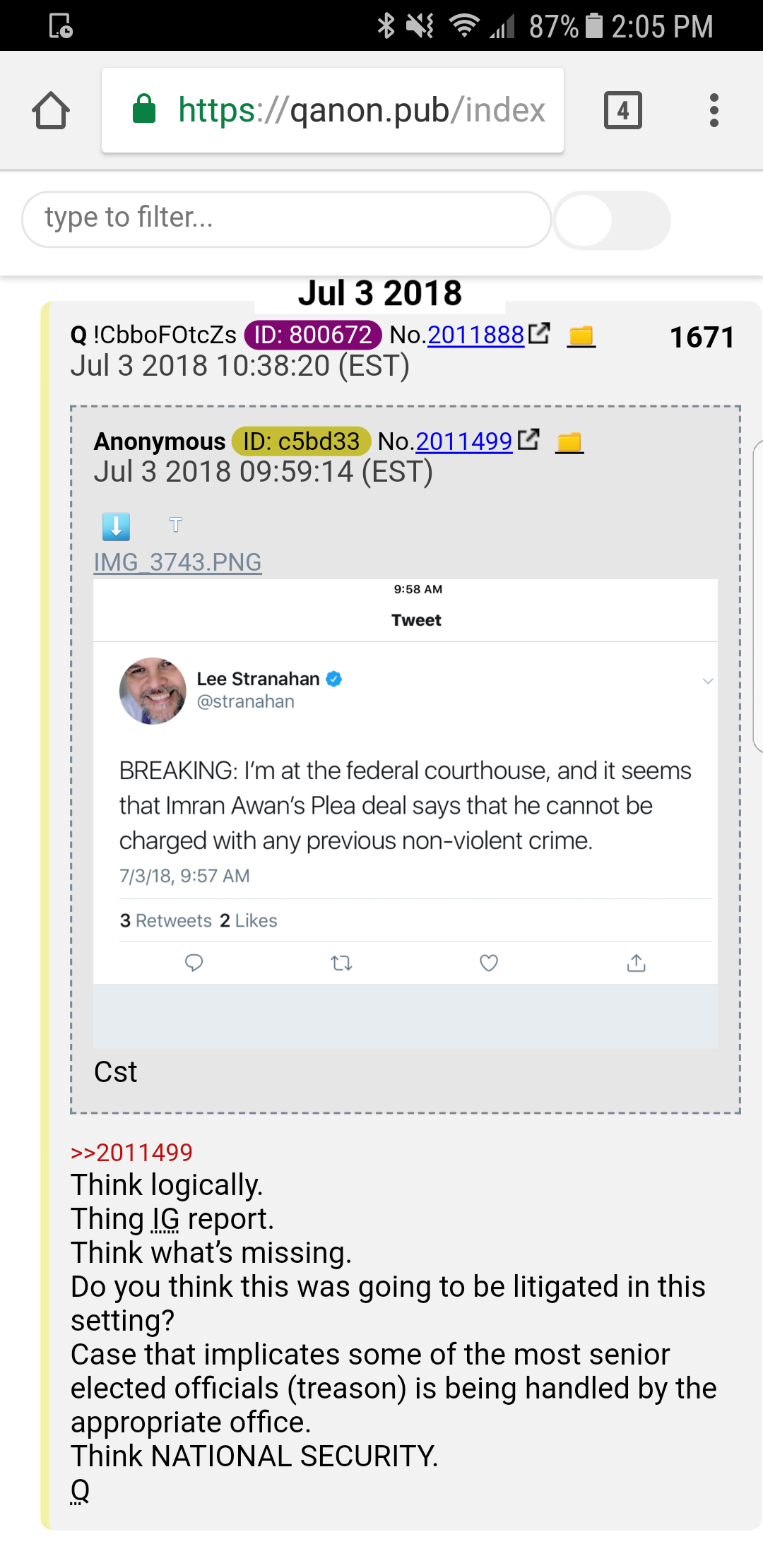
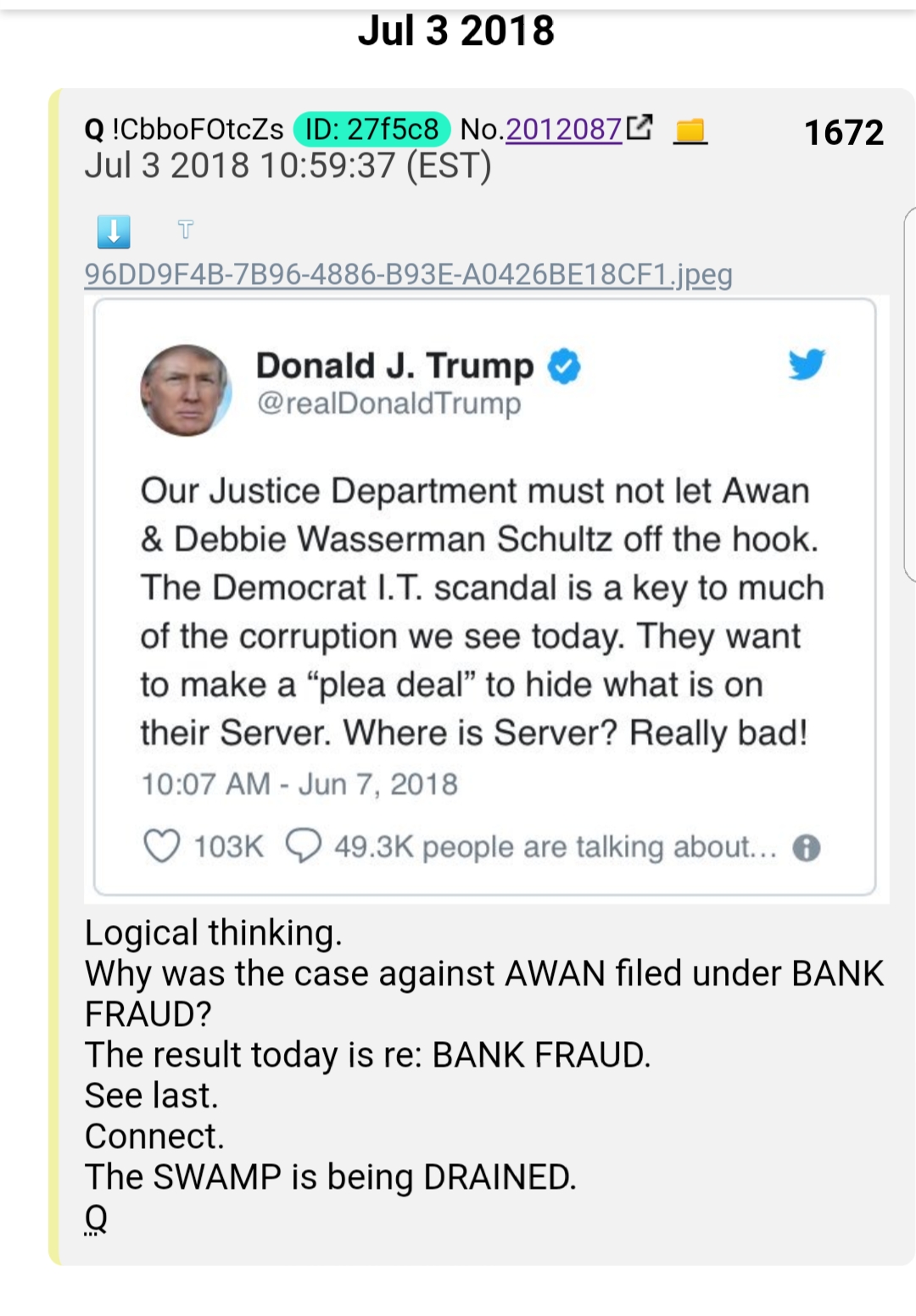
Awan goes to court today. Important. Awan CAN authenticate the server, in which case it becomes evidence. The needs the server here, not the information, so an NSA copy is of no use. Awan goes to court for Fraud today, my sense is, per Trump tweets, his deal opens the door for server: why I posted the Awan story yesterday and today, Q posts server....
I posted this before Q's drops on the topic, sorry for not waiting: 1672 and 1671
Just reading the clues.
OMG! YOU ARE Q, Cranky!!! ;o)
Sorry to interrupt the awesome conversations that are going on, but there's some new Q drops:
qanon.pub...


qanon.pub...
edit on 3-7-2018 by AgarthaSeed because: Spacing
(post by BringMeThanos removed for a manners violation)
Thing IG report.
Spelling mistake... should be K... missing. Extra G.
Think Think
Spelling mistake... should be K... missing. Extra G.
Think Think
originally posted by: liveandlearn
originally posted by: TomLawless
a reply to: pavil
They're a part of five eyes. Lots of deep staters frequent/built homes in New Zealand. They can get away from it all, yet still have access to the operation.
I am many pages behind so this may have been mentioned. Kim Dot.com is in NZ. I would guess his mega upload server is there as well. Maybe a leak?
LAL,
You raise and interesting point. Mega MUST have had stuff on it that people didn't want available. KDC went down in a heap and my speculation was at the time it was not copyright, but he had something (knowingly or unknowingly) that freaked out the controllers. We know goog docs was used to exchange messages, why not Mega, and of course there is the possibility of Podesta and friends presence there too....
originally posted by: Enderdog
originally posted by: crankyoldman
originally posted by: pavil
originally posted by: dashen
a reply to: pavil
It's not that simple. The server has to have a chain of custody. It has to have been seized legally in order to be admissible as evidence in court.
I wonder if this has anything to do with the raids on the awans
That's what I'm talking about. Having a chain of custody. I have to think, if they have "The Server", what was it for and who would have been in possession of it?
Supposedly some major Obama officials , including the former President were communicating via unofficial Means
.
Remember what back when they were moving Obama's records and such to Chicago for his library? Q seemed to imply they they were in possession of some of it.
Pav,
Awan goes to court today. Important. Awan CAN authenticate the server, in which case it becomes evidence. The needs the server here, not the information, so an NSA copy is of no use. Awan goes to court for Fraud today, my sense is, per Trump tweets, his deal opens the door for server: why I posted the Awan story yesterday and today, Q posts server....
I posted this before Q's drops on the topic, sorry for not waiting: 1672 and 1671
Just reading the clues.
OMG! YOU ARE Q, Cranky!!! ;o)
Edog, I was outed on day one.
It will be interesting to see how the media folks handle the Awan situation from here on out. In the past, say the Rosenbergs, it was a big damn deal. He seems to be getting pass - except for Trump Tweets which is really telling. Wasserman gets no deal IMO, as she has nothing to offer after Awan, her alley deadended.
a reply to: BringMeThanos
Some insight into the most recent drops.
Immunity from prosecution is used to get cooperation from a witness so that other, more important subjects can be targeted:
What Immunity Means for a Witness
Problems arise, though, when those granted immunity lie after having been given such. Do we know anyone to whom that may apply?
Who might Awan give testimony against in trade for the immunity he was granted?
You might be taken a little more seriously if your schtick weren't so transparent.
Some insight into the most recent drops.
Immunity from prosecution is used to get cooperation from a witness so that other, more important subjects can be targeted:
Immunity from prosecution is an important tool for prosecutors. They can offer immunity to witnesses for all types of crimes, even serious ones like kidnapping and murder. But prosecutors will often give immunity to a person who has committed minor crimes in order to compel that person to testify against someone who has committed more significant offenses. A common example is a prosecutor offering a small-time drug dealer immunity in exchange for against a big-time drug lord.
What Immunity Means for a Witness
Problems arise, though, when those granted immunity lie after having been given such. Do we know anyone to whom that may apply?
Who might Awan give testimony against in trade for the immunity he was granted?
You might be taken a little more seriously if your schtick weren't so transparent.
edit on 3-7-2018 by jadedANDcynical because: removed extraneous word
a reply to: jadedANDcynical
Thanks Jaded. I'll take that into consideration.
One day i'll reach your level of posting the definition of immunity as a valid contribution.
Any insight into the latest Q drops. They seem like a bunch of hashed buzzwords gleaned from the msn/anti-msm and trump twitter feeds. These crumbs could be created from trawling the ATS political forum.
I've also always wandered why Q talks to his fanbase like they are children... Think, think, think logically. Logical thinking. All very strange.
Thanks Jaded. I'll take that into consideration.
One day i'll reach your level of posting the definition of immunity as a valid contribution.
Any insight into the latest Q drops. They seem like a bunch of hashed buzzwords gleaned from the msn/anti-msm and trump twitter feeds. These crumbs could be created from trawling the ATS political forum.
I've also always wandered why Q talks to his fanbase like they are children... Think, think, think logically. Logical thinking. All very strange.
a reply to: jadedANDcynical
Do we know he has been given immunity?
His bank fraud charges were separate from all the DNC stuff.
Perhaps they used it to strong arm him.
I'm betting he already gave them what they wanted.
Do we know he has been given immunity?
His bank fraud charges were separate from all the DNC stuff.
Perhaps they used it to strong arm him.
I'm betting he already gave them what they wanted.
a reply to: dashen
link to tweet
#BREAKING Peter Strzok has been subpoenaed to testify publicly before a joint @HouseJudiciary & @GOPoversight hearing on Tuesday, July 10, at 10AM
link to tweet
Five Eyes - with a few pics of facilities
The last line above really says all you need to know - Without this thread I would have never known to what level all was being monitored.
Also note all the countries (Except one have a "Queen") or do We ? (Admiralty Court)
Freedom isn't free
Early drafts of the FVEY agreement were released in 2010 and indicate that partners will share by default, with exclusions at an absolute minimum, in the 1) collection of traffic; 2) acquisition of communications documents and equipment; 3) traffic analysis; 4) cryptanalysis; 5) decryption and translation; and 6) acquisition of information regarding communications organizations, procedures, practices and equipment. A FVEY PowerPoint slide released by Snowden puts the collection posture in less formal language: Sniff it All, Know it All, Collect it All, Process it All, Exploit it All, Partner it All.
The last line above really says all you need to know - Without this thread I would have never known to what level all was being monitored.
Also note all the countries (Except one have a "Queen") or do We ? (Admiralty Court)
Freedom isn't free
edit on 732018 by MetalThunder because: (no reason given)

So Q knew how to weaponize a force of anons.
They aren't motivated by fame or money.
They just want TRUTH.
They aren't easily fooled either.
Q would have been buried long ago if they were.
The other side cannot figure out how to fight this, because they don't even UNDERSTAND it.
Old tactics are lost on this bunch.
Besides, it's already gone way too far to ever be stopped.
So SUCK IT all you bad guys.
a reply to: pavil
Yes indeed. Strzok was threatening to cancel his voluntary testimony, so now the committee has made it involuntary.
I wonder if he'll plead the 5th on everything, or just skip the hearing and risk a contempt of congress indictment.
After the IG report, he must know they have him dead to rights.
Yes indeed. Strzok was threatening to cancel his voluntary testimony, so now the committee has made it involuntary.
I wonder if he'll plead the 5th on everything, or just skip the hearing and risk a contempt of congress indictment.
After the IG report, he must know they have him dead to rights.
originally posted by: BringMeThanos
originally posted by: FlyingFox
originally posted by: BringMeThanos
a reply to: pavil
Well surely if NK has immediately continued its accelerated program both Q and Trump are big losers?
Not if Trump makes an example out of him.
So you'd go from praising Trump for making friends to praising him for making an example.
Nice to see how easily you'll jump ship.
It's called "stick & carrot". Kind of hard to comprehend if you have no stick.
new topics
top topics
-
January 6th report shows disturbing trend (nobody is shocked)
US Political Madness: 15 hours ago, 22 flags -
The Truth about Migrant Crime in Britain.
Social Issues and Civil Unrest: 16 hours ago, 11 flags -
Let's talk planes.
General Chit Chat: 13 hours ago, 5 flags -
Inexplicable military simulation - virtual reality showdown in the night..
The Gray Area: 15 hours ago, 2 flags
active topics
-
Greatest thing you ever got, or bought?
General Chit Chat • 23 • : DAVID64 -
ILLUMINATION: Dimensions / Degrees – Da Vincis Last Supper And The Philosophers Stone
Secret Societies • 12 • : Compendium -
The Truth about Migrant Crime in Britain.
Social Issues and Civil Unrest • 13 • : TimBurr -
Stuck Farmer And His Queue Jumping Spawn
Rant • 8 • : TimBurr -
Trudeau Resigns! Breaking
Mainstream News • 68 • : MindBodySpiritComplex -
Live updates: Congress meets to certify Trump's presidential election victory
US Political Madness • 19 • : KrustyKrab -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 3953 • : 777Vader -
Judge rules president-elect Donald Trump must be sentenced in 'hush money' trial
US Political Madness • 37 • : JadedGhost -
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 7997 • : KrustyKrab -
Meta Llama local AI system is scary good
Science & Technology • 42 • : Arbitrageur


