It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
Hey ATS!
Are you ready to enter the new era of Quantum Internet?

As shown in this PDF file, its structure has been discussed at a workshop.


So what do you think this new "virtually unhackable" internet will bring to our society, ATS?
Are you ready to enter the new era of Quantum Internet?

Today, the Department of Energy (DOE) announced America’s Blueprint for the Quantum Internet. When developed with DOE’s National Labs and private sector partners, the Quantum Internet will offer a world of new possibilities and opportunities.
The Quantum Internet will one day connect computers that can solve challenges of incredible complexity, enabling a faster flow of information and opening up entirely new areas of scientific research and economic development.
We now have the Blueprint to make this Quantum Internet a reality, and I am elated to share our plan with you all today.
As part of DOE’s effort, Argonne and Fermi National Labs will continue to play a critical part in our effort to develop this Quantum Internet and realize its many benefits.
These experts are already making extraordinary achievements. For example, in February, the Chicago Quantum Exchange – anchored by the University of Chicago and Argonne and Fermilab – launched a 52-mile testbed for Quantum communications amongst several other universities, which will allow scientists and engineers to address the challenges of operating a Quantum network under real-world conditions.
Of course, the research benefits from “Quantum sensors” will also be transformative for our entire way of life. Quantum sensor networks could be equally transformative, with applications ranging from increasing our understanding of dark matter to improving the resolution of extra-solar planets to making better predictions of volcanic eruptions.
Eventually, we will connect all 17 DOE National Labs as the backbone of the Quantum Internet. We’ll also add in universities and private sector partners, working with a broad community of individuals and institutions with diverse and complementary skill sets.
As shown in this PDF file, its structure has been discussed at a workshop.
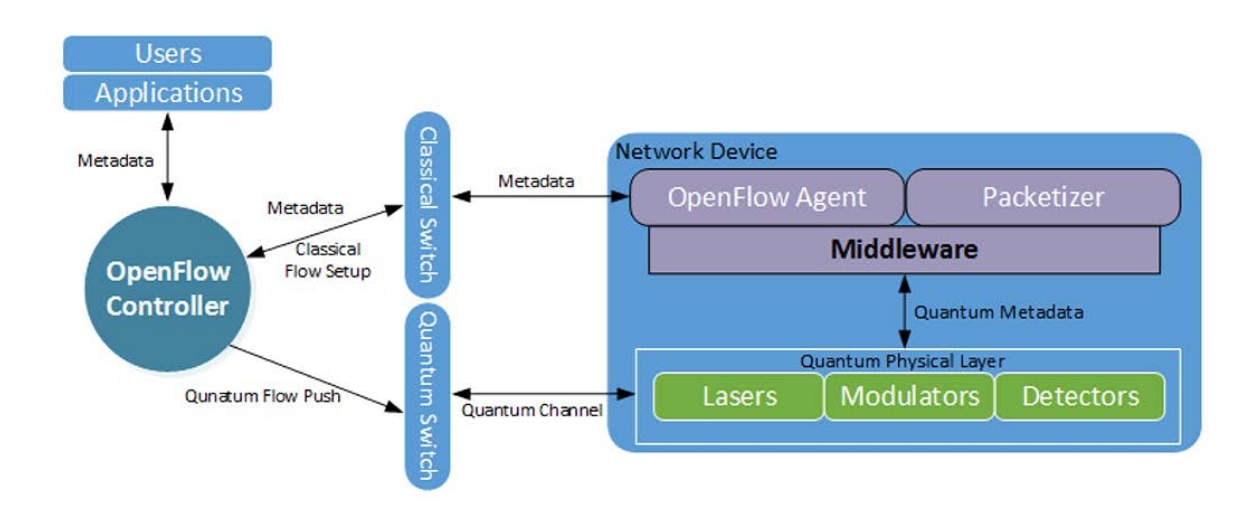
Figure 2:1. Concept of a cascaded quantum network protype using classical network control interacting with nodes equipped with quantum hardware. Reproduced from “Proc. SPIE 9873, Quantum Information and Computation IX,” 98730B (2016)

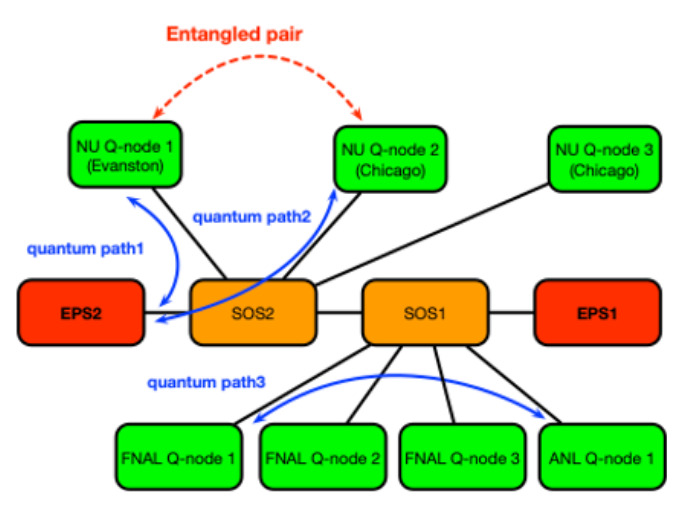
Figure 2:2. Quantum path and routing of entangled photons using SDNs using the Chicago quantum network

Figure 2:3. Example of a one-hop, first-generation quantum repeater. Two sources generate independent entangled pairs A-B and C-D. One member of each pair, B and C, are brought together and interfered at an intermediate location, projecting the B-C pair onto one of four Bell states (Bell state measurement). This partial collapse of the four-particle wavefunction results in the two remaining particles, A and D, being in an entangled state, separated by a long distance.

Figure 3:3. Long Island quantum network extended to New York City. The network will use a chain of quantum repeaters, extended across Long Island via three entangled sources, six quantum memories, and two entanglement swapping stations. Using ESnet’s existing fiber infrastruc-ture, the network will connect SBU to New York City via Brookhaven Lab with intermediate stations on the two campuses and in Garden City, N.Y. This is expected to be the first quantum repeater network of its kind in the world.

So what do you think this new "virtually unhackable" internet will bring to our society, ATS?
Virtually unhackable... as if a quantum medium would change the nature of the machines that communicate accross it.
Hogwash.
a reply to: Anon283799
Hogwash.
a reply to: Anon283799
a reply to: Anon283799
Unfortunately a lot of it is being done in Chicago, so I dont have much hope for it.
Unfortunately a lot of it is being done in Chicago, so I dont have much hope for it.
a reply to: Anon283799
I think quantum systems can augment the capability of the internet in the United States especially as it applies to efficient traffic management and error correction. It would definitely make search engnies FAR more capable of understanding context and natural language. Translations would certainly get better. Encryption will have to change dramatically and NOW is the time to start educating oneself on quantum computing.
I think quantum systems can augment the capability of the internet in the United States especially as it applies to efficient traffic management and error correction. It would definitely make search engnies FAR more capable of understanding context and natural language. Translations would certainly get better. Encryption will have to change dramatically and NOW is the time to start educating oneself on quantum computing.
"Quantum" is BS promotional jingoism to lure investors into questionable technology. It should work great!! I might even throw in a few bucks,
but before I do, show me something besides charts and graphs. And I don't mean Hardys paradox double slit crap; something practical perhaps?
edit on 25-7-2020 by olaru12 because: (no reason given)
originally posted by: hombero
Virtually unhackable... as if a quantum medium would change the nature of the machines that communicate accross it.
Hogwash.
a reply to: Anon283799
Totally agree, quantum computing doesn't mean "unhackable", in fact with the increased speeds, it actually makes password breaking much faster. So unless new methods of security are implemented where required, it won't change anything.
Additionally, the hardware and software will still have to configured and programmed by people, human error will always exist
a reply to: olaru12
I partially agree with you actually. The industry certainly needs more research dollars and more time before that can become a reality. Quantum is a descriptor for a system that takes advantage of the Standard Model.
I do believe the United States should start taking larger leaps in this field. Currently, China has managed to build a few practical quatum systems and with their penchant for espionage it would make sense to develop a quantum internet system to even be able to mount a reasonable defense.
I partially agree with you actually. The industry certainly needs more research dollars and more time before that can become a reality. Quantum is a descriptor for a system that takes advantage of the Standard Model.
I do believe the United States should start taking larger leaps in this field. Currently, China has managed to build a few practical quatum systems and with their penchant for espionage it would make sense to develop a quantum internet system to even be able to mount a reasonable defense.
Did they give a timeline on this thing or what? Couldn't find any but maybe I missed something. Less then 5 years would be amazing but things like
this always take longer so I say prolly 2030's... The conspiracy theorist in me say someone somewhere in Government has one working right now.
edit on 25-7-2020 by watchandwait410 because: (no reason given)
a reply to: watchandwait410
The best answer to your question is to visit the websites of the aforementioned organizations.
I'm still spying on the university of buffalo to see what arndt pralle's labs are up to with their remote control human technology. Momuch of it is very sophisticated science language. What I am waiting for is a commercial sponsor to pop up. I suspect it will be defenze related, but either way that benefactor and their donation will become public record.
Investigate everything!
The best answer to your question is to visit the websites of the aforementioned organizations.
I'm still spying on the university of buffalo to see what arndt pralle's labs are up to with their remote control human technology. Momuch of it is very sophisticated science language. What I am waiting for is a commercial sponsor to pop up. I suspect it will be defenze related, but either way that benefactor and their donation will become public record.
Investigate everything!
The thread title says "quantum internet", not "quantum computer". "unhackable" is a bit of an oversimplification in one word, but it's not totally erroneous to claim that's more or less possible for a quantum internet.
originally posted by: Zcustosmorum
Totally agree, quantum computing doesn't mean "unhackable", in fact with the increased speeds, it actually makes password breaking much faster. So unless new methods of security are implemented where required, it won't change anything.
The gritty details are that in fact the quantum communication channel could be "hacked", but the reason they say it's "unhackable", is because there is a method of detecting any such hack, and of course one could program the channel to cease communication as soon as such a hack is detected. So the hackers get nothing, and in that sense it's essentially "unhackable". I would suppose the military would be the earliest adopter. This is from page 11 of the pdf in the OP:
"it is the information exchange over a quantum channel—with its ability to detect any interception—that offers the ultimate in secure communication. Early adopters for such future solutions will be found in areas such as national security, banking, and energy delivery infrastructure."
The basic theoretical ideas are sound, but implementation and working out the kinks, like the current distance limitations, will take time.
edit on 2020725 by Arbitrageur because: clarification
originally posted by: olaru12
"Quantum" is BS promotional jingoism to lure investors into questionable technology. It should work great!! I might even throw in a few bucks, but before I do, show me something besides charts and graphs. And I don't mean Hardys paradox double slit crap; something practical perhaps?
I concur.
They need the research money
Thinking of he practical bits at the moment and first thoughts are more the environment needed to keep these repeaters working probably would be very
expensive and prone to failure and with such short distances the number required to make it work becomes silly once you start to scale up.
I don't know about the practical security angle as while you can detect interception during transmission at the moment you need so many people to make it work theres plenty of opportunity for spies etc at either end of the transmission chain to pick up the information and the fact that you need lots and lots of cooling means it'll probably be pretty easy for people to work out where giant tanks of LN2 are and pop them causing downtime.
I don't know about the practical security angle as while you can detect interception during transmission at the moment you need so many people to make it work theres plenty of opportunity for spies etc at either end of the transmission chain to pick up the information and the fact that you need lots and lots of cooling means it'll probably be pretty easy for people to work out where giant tanks of LN2 are and pop them causing downtime.
originally posted by: Arbitrageur
The gritty details are that in fact the quantum communication channel could be "hacked", but the reason they say it's "unhackable", is because there is a method of detecting any such hack, and of course one could program the channel to cease communication as soon as such a hack is detected. So the hackers get nothing, and in that sense it's essentially "unhackable". I would suppose the military would be the earliest adopter. This is from page 11 of the pdf in the OP:
"it is the information exchange over a quantum channel—with its ability to detect any interception—that offers the ultimate in secure communication. Early adopters for such future solutions will be found in areas such as national security, banking, and energy delivery infrastructure."
The basic theoretical ideas are sound, but implementation and working out the kinks, like the current distance limitations, will take time.
I read through the linked articles looking for what properties of the quantum communication channel would enable the data transmitters to "detect any interception"? This may have been covered in the various pictures above, but I didn't find it there.
We already have cryptographic methods today to detect if data has at least been tampered with by an intermediary when party A sends data to party B (party A includes a signature of the payload using their RSA key, party B checks the payload using party A's public key, and it should very clear if somebody has manipulated the data in flight).
But this sounds different, as if the two parties can detect a data leak where someone else passively listens in on the transmission, but doesn't try to change the message. Again, though, even if someone intercepts the message, if it's strongly encrypted, the data won't do them any good unless they can decipher it. I'm sure this has some obscure basis in quantum entanglement, but the nature of how it works is opaque to me.
edit on 26-7-2020 by SleeperHasAwakened because: formatting
Yes that's right, it can detect passive listening. The overview documents don't go into the technical details but here's how it works in simple terms:
originally posted by: SleeperHasAwakened
But this sounds different, as if the two parties can detect a data leak where someone else passively listens in on the transmission, but doesn't try to change the message.
Quantum Communication Just Took a Great Leap Forward
That article goes into a little depth about the problem I mentioned in my earlier post about the difficulties in implementing such a method over long distances.
More specifically, each node of a quantum network consists of quantum processors, which rely on quantum bits, or qubits, instead of classical bits. Qubits can exist in multiple states, known as superposition, allowing them to perform multiple calculations at once, while traditional bits are confined to only a 0 or a 1, limiting them to one calculation at a time. When one quantum processor changes the states of its photons, the corresponding entangled photons are changed in the other quantum processor, thus transferring the necessary qubits.
One benefit of this is that it creates an unhackable system of communication, in that any attempt to eavesdrop or intercept the information would disentangle the particles. This would alter the message and make it immediately obvious that a hacking attempt had occurred.
originally posted by: Arbitrageur
Yes that's right, it can detect passive listening. The overview documents don't go into the technical details but here's how it works in simple terms:
originally posted by: SleeperHasAwakened
But this sounds different, as if the two parties can detect a data leak where someone else passively listens in on the transmission, but doesn't try to change the message.
Quantum Communication Just Took a Great Leap Forward
That article goes into a little depth about the problem I mentioned in my earlier post about the difficulties in implementing such a method over long distances.
More specifically, each node of a quantum network consists of quantum processors, which rely on quantum bits, or qubits, instead of classical bits. Qubits can exist in multiple states, known as superposition, allowing them to perform multiple calculations at once, while traditional bits are confined to only a 0 or a 1, limiting them to one calculation at a time. When one quantum processor changes the states of its photons, the corresponding entangled photons are changed in the other quantum processor, thus transferring the necessary qubits.
One benefit of this is that it creates an unhackable system of communication, in that any attempt to eavesdrop or intercept the information would disentangle the particles. This would alter the message and make it immediately obvious that a hacking attempt had occurred.
Sounds a little to me like Heisenberg's Uncertainty Principle (measuring/testing a system will actually influence its behavior), but this is at the edge of my physics acumen.
Thanks for explanation.
That's a valid principle but that's not exactly what they use, which is what Einstein called "spooky action at a distance", otherwise known as quantum entanglement. They create entangled photons in pairs, and as long as only the two parties Alice and Bob compare the pairs of photons, they correlate as entanglement says they should. When a third party eavesdrops, they also capture some of the entangled photons, so when Alice and Bob compare their pairs of photons, they no longer see full correlation, and figure some photons must be going to a third party passive listener, and their communication is shut down to prevent the hacker from getting anything.
originally posted by: SleeperHasAwakened
Sounds a little to me like Heisenberg's Uncertainty Principle (measuring/testing a system will actually influence its behavior), but this is at the edge of my physics acumen.
Thanks for explanation.
Quantum theory says there's no limit to the distance Bob and Alice can be separated for it to work, but in practice there are distance limitations, that researchers are trying to overcome.
edit on 2020726 by Arbitrageur because: clarification
new topics
-
D.B. Cooper mystery may be solved
General Conspiracies: 27 minutes ago
top topics
-
D.B. Cooper mystery may be solved
General Conspiracies: 27 minutes ago, 4 flags
active topics
-
Petition Calling for General Election at 564,016 and rising Fast
Political Issues • 96 • : BrucellaOrchitis -
D.B. Cooper mystery may be solved
General Conspiracies • 2 • : chr0naut -
I thought Trump was the existential threat?
World War Three • 80 • : andy06shake -
Joe Biden Dabs Away Tears at Farewell White House Dinner
Politicians & People • 27 • : chr0naut -
Results of the use of the Oreshnik missile system in Dnepropetrovsk
World War Three • 241 • : andy06shake -
Why isn't Psychiatry involved?
Social Issues and Civil Unrest • 14 • : BrucellaOrchitis -
Well, here we go red lines crossed Biden gives the go ahead to use long range missiles
World War Three • 396 • : andy06shake -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 3384 • : brewtiger123 -
BIDEN Admin Begins Planning For January 2025 Transition to a New President - Today is 4.26.2024.
2024 Elections • 59 • : WeMustCare -
DOJ Special Counsel Robert HUR Says JOE BIDEN Can Be ARRESTED After Jan 20th 2025.
Above Politics • 30 • : WeMustCare
