It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
a reply to: Justoneman
My sister, brother in law and cousin are all military.
They would not follow those orders.
And I think anyone would have a hell of a time killing off the usa military.
My sister, brother in law and cousin are all military.
They would not follow those orders.
And I think anyone would have a hell of a time killing off the usa military.
edit on 7-8-2020 by scraedtosleep because: (no reason
given)
Ka-BOOOM
==BREAKING: Lebanon's president has said an investigation into the Beirut blast is exploring the possibility it was caused by "a rocket or a bomb" - Sky News
twitter.com...
==BREAKING: Lebanon's president has said an investigation into the Beirut blast is exploring the possibility it was caused by "a rocket or a bomb" - Sky News
twitter.com...
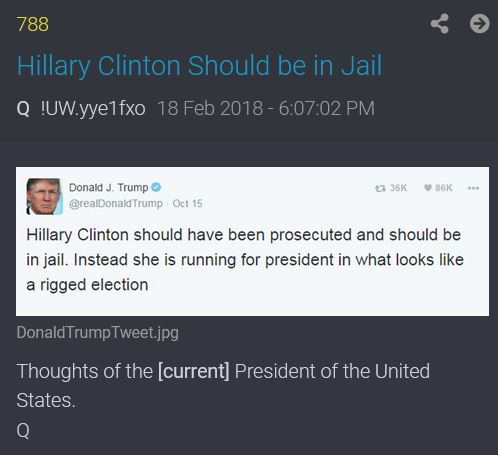
POTUS: "So I have a lot of enemies out there. This may be the last time you’ll see me for a while. A lot of very, very rich enemies, but they are
not happy with what I’m doing."
88 days till election.
Trump = 88
Q88 - "10 Days of Darkness"
From Dan (Trump in Ohio Aug 6):

👇
👇
 👉 Q2.
👉 Q2.
88 days till election.
Trump = 88
Q88 - "10 Days of Darkness"
From Dan (Trump in Ohio Aug 6):

👇

👇

a reply to: EndtheMadnessNow
I know you did not mean it this way, but "88" is Neonazi shorthand for "Heil Hitler" (H being the 8th letter of the alphabet).
Cheers
Trump = 88
I know you did not mean it this way, but "88" is Neonazi shorthand for "Heil Hitler" (H being the 8th letter of the alphabet).
Cheers
Regarding Trump's statement about not being seen for a while, it's pretty clear the SS received a credible threat to his life. The only other option
to hide the President, in my humble opinion, would be a strike of some kind from space.
Regarding the submarine taking on new personnel, I think it picked up a SEAL team.
Recently, three "kids" scaled a fence at Mar-A-Lago. They had an AK-47 with them. I think there's more to this story.
A lot of strange things are happening - fires, explosions, bombings. wild weather. Again, in my humble opinion, it looks like a coordinated effort of some kind, as these incidents are kicking off one after another in a specific area of the world.
I can't see the bigger picture, but I'm willing to bet everything is connected in some way.
I did just have a fleeting thought that Trump is disappearing because there will be a huge reveal with respect to all the investigations, etc. Something so big that a blatant attempt may be made to murder him and, possibly, his family.
Regarding the submarine taking on new personnel, I think it picked up a SEAL team.
Recently, three "kids" scaled a fence at Mar-A-Lago. They had an AK-47 with them. I think there's more to this story.
A lot of strange things are happening - fires, explosions, bombings. wild weather. Again, in my humble opinion, it looks like a coordinated effort of some kind, as these incidents are kicking off one after another in a specific area of the world.
I can't see the bigger picture, but I'm willing to bet everything is connected in some way.
I did just have a fleeting thought that Trump is disappearing because there will be a huge reveal with respect to all the investigations, etc. Something so big that a blatant attempt may be made to murder him and, possibly, his family.
originally posted by: SideEyeEverything
a reply to: oldschoolwarhawk
Sorry. no.
whoops my bad i mis read a previous post then
POTUS TYPO Tweet at 07:34:36 but now deleted:
1) TYPO - 2 ways to read this:
a) their is = The IRIS = The EYE
b) Their should be there giving IR to RE
Could be anagram IRRE = ERR i = Missile error?
2) Timestamp points to:
Q7 Hillary/Obama Emailgate
Q734 Experimental Drug Promises to Kill Flu Virus
Q34 Q Clearance Patriot
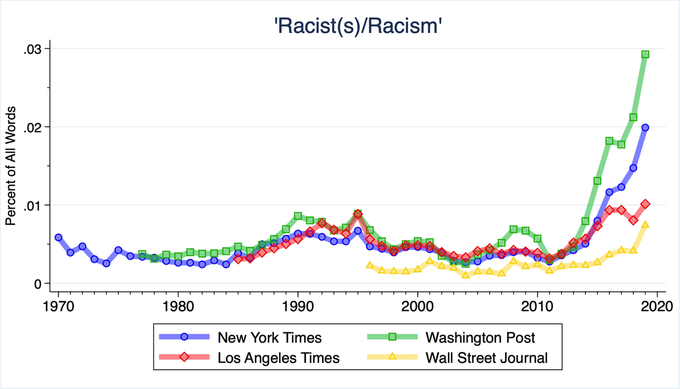
Q3436 Rep. Ilhan Omar is Projecting Racism and Division
Q36 Military Intelligence: There is simply no other way than to use the military. It’s that corrupt and dirty. Please be safe and pray for those in harms way as they continually protect and serve our great country.
3) Tweet Delta of 04:33 points to:
Q433 TRUST WRAY.
4) CAPS only simple gematria gives:
a) Base = SJBBVTNVWL = 146
Q146
b) Remove Dupes = Q98 Graphic is good. Please update and continue to log. Important more than you know. Review each sentence post happenings. Big picture. Signatures have necessary meaning. Snow White. Godfather III.
c) Base+nums = Q155 Green Stringer:
d) RemoveDupes+nums = Q107:
Sleepy Joe Biden just lost the Black Vote. This statement is a disaster from which their is no recovery! t.co...
1) TYPO - 2 ways to read this:
a) their is = The IRIS = The EYE
b) Their should be there giving IR to RE
Could be anagram IRRE = ERR i = Missile error?
2) Timestamp points to:
Q7 Hillary/Obama Emailgate
Q734 Experimental Drug Promises to Kill Flu Virus
Q34 Q Clearance Patriot
Q3436 Rep. Ilhan Omar is Projecting Racism and Division
Q36 Military Intelligence: There is simply no other way than to use the military. It’s that corrupt and dirty. Please be safe and pray for those in harms way as they continually protect and serve our great country.
3) Tweet Delta of 04:33 points to:
Q433 TRUST WRAY.
4) CAPS only simple gematria gives:
a) Base = SJBBVTNVWL = 146
Q146
::::WARNING::::
This is not a game!
DIRECT ATTACK TODAY BY NYT/CLOWNS IN AMERICA:
www.nytimes.com...
Do you believe in coincidences?
How many coincidences do you need before you believe?
This is the biggest insider drop in the history of the world.
Pray.
b) Remove Dupes = Q98 Graphic is good. Please update and continue to log. Important more than you know. Review each sentence post happenings. Big picture. Signatures have necessary meaning. Snow White. Godfather III.
c) Base+nums = Q155 Green Stringer:
_Conf_D-TT_^_v891_0600_yes
_green1_0600
Bunker Apple Yellow Sky [… + 1]
Yes
Godspeed.
Q
d) RemoveDupes+nums = Q107:
Code:
May God also grant all of us the wisdom to ask what concrete steps we can take to reduce the violence and weaponry in our midst.
Note when we just sent the go orders and when this Tweet went live.
Coincidence?
Pray.
Q
Contractors
U.S. Government Contractor Embedded Software in Apps to Track Phones
U.S. Government Contractor Embedded Software in Apps to Track Phones
A small U.S. company with ties to the U.S. defense and intelligence communities has embedded its software in numerous mobile apps, allowing it to track the movements of hundreds of millions of mobile phones world-wide, according to interviews and documents reviewed by The Wall Street Journal.
Anomaly Six LLC a Virginia-based company founded by two U.S. military veterans with a background in intelligence, said in marketing material it is able to draw location data from more than 500 mobile applications, in part through its own software development kit, or SDK, that is embedded directly in some of the apps. An SDK allows the company to obtain the phone’s location if consumers have allowed the app containing the software to access the phone’s GPS coordinates......
a reply to: oldschoolwarhawk
no biggie. I wouldn't have even known myself if I hadn't gone to the goog to look him up.
no biggie. I wouldn't have even known myself if I hadn't gone to the goog to look him up.
a reply to: Creep Thumper
Regarding Trump moving out of the public eye... could it be that some things are going to come to light that perhaps would be better if he wasn't in the spot light? I've been having thoughts on and off, that when information (real information) starts to drop, that it is for everyone... left and right. The fever pitch Trump hate could get in the way of anti-Trumpers looking at it without the glasses.
I'm very reluctant to raise hopes for myself or anyone else... I know the boom hopes have been dashed many times. My JFK posts also didn't help... I hold my hands up to them.
But as you point out, there are many real events happening that on the surface seem disconnected, but yet the proximity of timing adds a dimension. I guess we have to find out like everyone else.
Regarding Trump moving out of the public eye... could it be that some things are going to come to light that perhaps would be better if he wasn't in the spot light? I've been having thoughts on and off, that when information (real information) starts to drop, that it is for everyone... left and right. The fever pitch Trump hate could get in the way of anti-Trumpers looking at it without the glasses.
I'm very reluctant to raise hopes for myself or anyone else... I know the boom hopes have been dashed many times. My JFK posts also didn't help... I hold my hands up to them.
But as you point out, there are many real events happening that on the surface seem disconnected, but yet the proximity of timing adds a dimension. I guess we have to find out like everyone else.
Another interesting POTUS tweet at 09:55:17:

1.8 = 18 = R
1) Timestamp points to:
Q9 Dem's Control Black Population
Q955 US Marine Corp Activated in 3 US Cities
Q55 Look to Twitter: Exactly this: "My fellow Americans, the Storm is upon us......." God bless.
Q17 Focus on the power of POTUS as it relates to the Marines. How can MI be applied to prosecute bad actors and avoid corrupt agencies and judges? Biggest drop on Pol.
2) Tweet delta = 06:17 pointing to:
Q617 Select news members / journalists are vital to delivering the message (as are YOU). Imagine if these people were removed. Total control re: MSM. They represent a clear and present danger to the enemy. Re-read past crumbs re: security. Where is JS? How do we truly protect those important to us? [19] immediates [no longer with us]. Self-suicide if actioned. Real life.
3) CAPS only simple gematria gives:
a) Base = MILLIONJOBSADDEDINJULY = 239
Q239 The Asia Foundation. CIA-RDP84B00049R001303260026-4 Happy hunting.
b) RemoveDupes = MBSAEUY = 86
Q86 Saudi Arabia - The Bloody Wonderland. =Alice & Wonderland signatures
c) Base+nums = 248
Q248 #FLYROTHSFLY#
d) RemoveDupes+nums = 95
Q95 What happened in SA will happen here, Asia, and EU. Keep digging and keep organizing the info into graphics (critical). God bless. Hillary & Saudi Arabia Snow White Godfather III

1.8 = 18 = R
1) Timestamp points to:
Q9 Dem's Control Black Population
Q955 US Marine Corp Activated in 3 US Cities
Q55 Look to Twitter: Exactly this: "My fellow Americans, the Storm is upon us......." God bless.
Q17 Focus on the power of POTUS as it relates to the Marines. How can MI be applied to prosecute bad actors and avoid corrupt agencies and judges? Biggest drop on Pol.
2) Tweet delta = 06:17 pointing to:
Q617 Select news members / journalists are vital to delivering the message (as are YOU). Imagine if these people were removed. Total control re: MSM. They represent a clear and present danger to the enemy. Re-read past crumbs re: security. Where is JS? How do we truly protect those important to us? [19] immediates [no longer with us]. Self-suicide if actioned. Real life.
3) CAPS only simple gematria gives:
a) Base = MILLIONJOBSADDEDINJULY = 239
Q239 The Asia Foundation. CIA-RDP84B00049R001303260026-4 Happy hunting.
b) RemoveDupes = MBSAEUY = 86
Q86 Saudi Arabia - The Bloody Wonderland. =Alice & Wonderland signatures
c) Base+nums = 248
Q248 #FLYROTHSFLY#
d) RemoveDupes+nums = 95
Q95 What happened in SA will happen here, Asia, and EU. Keep digging and keep organizing the info into graphics (critical). God bless. Hillary & Saudi Arabia Snow White Godfather III
a reply to: oldschoolwarhawk
I think it was me who may have got it wrong and said Doug Band was on the left in picture.
I think it was me who may have got it wrong and said Doug Band was on the left in picture.
Chinese Hackers Have Pillaged Taiwan's Semiconductor
Industry
A campaign called Operation Skeleton Key has stolen source code, software development kits, chip designs, and more.
Those chicom hackers are a tenacious bunch hellbent on infiltrating and stealing anything of value.
A campaign called Operation Skeleton Key has stolen source code, software development kits, chip designs, and more.
Even amidst China's wholesale hacking of its island neighbor, though, CyCraft's Duffy argues that the semiconductor industry represents a particularly dangerous target. Stealing chip schematics, he points out, could potentially allow Chinese hackers to more easily dig up vulnerabilities hidden in computing hardware. "If you have a really deep understanding of these chips at a schematic level, you can run all sorts of simulated attacks on them and find vulnerabilities before they even get released," Duffy says. "By the time the devices hit the market, they're already compromised."
Those chicom hackers are a tenacious bunch hellbent on infiltrating and stealing anything of value.
a reply to: saladfingers123456
I think we should wait for Q to post, which I will stupidly guess will happen soon.
I think we should wait for Q to post, which I will stupidly guess will happen soon.
a reply to: RelSciHistItSufi
Preceding the "1.8 million jobs added in july" tweet, there are 2 other tweets with interesting timestamps/links:
#1 at 08:48:00 links to:
Q848 Watch the Water Marker
#2 at 09:49:00 links to:
Q949 Trust the plan. Full control.
Preceding the "1.8 million jobs added in july" tweet, there are 2 other tweets with interesting timestamps/links:
#1 at 08:48:00 links to:
Q848 Watch the Water Marker
#2 at 09:49:00 links to:
Q949 Trust the plan. Full control.
edit on 7-8-2020 by RelSciHistItSufi because: (no reason
given)
originally posted by: scraedtosleep
a reply to: saladfingers123456
I think he was just being dramatic.
The President is attending a big Fundraiser tomorrow (Saturday).
www.cnbc.com...
a reply to: carewemust
I honestly thought he meant that he would not be returning to Ohio any time soon, when he said it.
I honestly thought he meant that he would not be returning to Ohio any time soon, when he said it.
new topics
-
USSS Agent Fired for Having Sex In Michelle Obama's Bathroom
US Political Madness: 1 hours ago -
Watching TV
Jokes, Puns, & Pranks: 3 hours ago
top topics
-
RFK is Trumps health pick
2024 Elections: 12 hours ago, 18 flags -
Watching TV
Jokes, Puns, & Pranks: 3 hours ago, 5 flags -
USSS Agent Fired for Having Sex In Michelle Obama's Bathroom
US Political Madness: 1 hours ago, 5 flags
active topics
-
The Reactionary Conspiracy 13. The plot’s theology.
General Conspiracies • 296 • : MarxistDebunker2 -
USSS Agent Fired for Having Sex In Michelle Obama's Bathroom
US Political Madness • 11 • : theatreboy -
WATCH LIVE: US Congress hearing on UFOs, unidentified anomalous phenomena
Aliens and UFOs • 67 • : putnam6 -
FLORIDA Sues Biden-Harris FEMA for Denying Disaster Assistance to Homeowners with TRUMP Signs.
US Political Madness • 45 • : grey580 -
Thune selected as Senate Republican Leader
US Political Madness • 72 • : CriticalStinker -
The art of being offended
Social Issues and Civil Unrest • 38 • : bastion -
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 7774 • : underpass61 -
The Acronym Game .. Pt.4
General Chit Chat • 955 • : tinkerbell99 -
RFK is Trumps health pick
2024 Elections • 8 • : marg6043 -
Qatar kicks out HAMAS
Middle East Issues • 20 • : bastion