It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
a reply to: KnightErrant
I watched the first episode of S1 and was not impressed until after the second half. Intriguing but wish they were more experienced investigators.
Aside from the coal town Hellier, the series was also partly filmed in Covington, Kentucky; which gained notoriety from the students from Covington Catholic High School and a Native American man engaged in a form of conflict last January in D.C. Though, Covington Catholic High School is not located in Covington but in Park Hills, which is a neighboring city.
Because of the word -naut & paranormal doorways reminds me of the...
Randonauts
Randonauts, AFAIK are a collective of existential investigators researching unknown spaces outside of predetermined reality tunnels. They do this using a quantum random location generator.
Enter...

I watched the first episode of S1 and was not impressed until after the second half. Intriguing but wish they were more experienced investigators.
Aside from the coal town Hellier, the series was also partly filmed in Covington, Kentucky; which gained notoriety from the students from Covington Catholic High School and a Native American man engaged in a form of conflict last January in D.C. Though, Covington Catholic High School is not located in Covington but in Park Hills, which is a neighboring city.
Because of the word -naut & paranormal doorways reminds me of the...
Randonauts
The fatum-project was born as an attempt to research unknown spaces outside predetermined probability-tunnels of the holistic world and has become a fully functional reality-tunnel creating machine that digs rabbit holes to wonderland.
Randonauts, AFAIK are a collective of existential investigators researching unknown spaces outside of predetermined reality tunnels. They do this using a quantum random location generator.
Enter...

a reply to: carewemust
That was a good article for explanation and also short and sweet. While I was watching the video though I saw this guy run by. He seems very out of place for wearing a suit in the middle of that mayhem. Wonder who he is? I dont think it would be someone from the embassy itself running out into that crowd. Wouldnt make sense. So where did he come from?
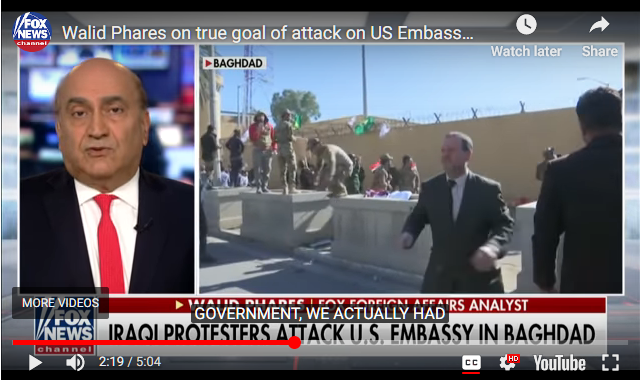
That was a good article for explanation and also short and sweet. While I was watching the video though I saw this guy run by. He seems very out of place for wearing a suit in the middle of that mayhem. Wonder who he is? I dont think it would be someone from the embassy itself running out into that crowd. Wouldnt make sense. So where did he come from?

originally posted by: onehuman
a reply to: carewemust
That was a good article for explanation and also short and sweet. While I was watching the video though I saw this guy run by. He seems very out of place for wearing a suit in the middle of that mayhem. Wonder who he is? I dont think it would be someone from the embassy itself running out into that crowd. Wouldnt make sense. So where did he come from?
Hunter Biden? If so, that is where he has been!
Hunter needs this distraction in the news.
originally posted by: F2d5thCavv2
a reply to: doobydoll
All timelines lead to the same future, no more possibilities.
Interesting. The 'game' is programmed to produce one outcome. Players believe they can make choices but that is illusionary.
Cheers
Predetermination.
Free will is not an illusion, but ends up being a sad joke.
The video "'Yoda' the Warmonger is Dead" at link
covering the DoD Office of Net Assessment, Senior Executive Service (SES), Highlands Group & DARPA is worth watching.
Andrew Marshall was recently mentioned here a few times. He
didn't retire until age 93 and died a few years later in March 2019.

Massive amount of Q themed info at Americans for Innovation.
The Miller Act is hugely important to subcontractors and suppliers when it comes to getting paid on a federal construction projects.
The Miller Act Claims
Who Really Owns the Military Industrial Complex: The Highland Group Exposed
Though much of the article has been discussed and brought to light in these threads over the past 2 years, this article helps put it all together.
The Senior Executive Service (SES) and Britain’s Crown Agents were/are Marshall’s fascist troops.
Institutionalized patent theft has driven American and British (fascist) economies for 100 years.
Marshall directed Highlands Group patent theft planning as government policy with James P. Chandler, III since 1973 through the DoD Office of Net Assessment & DARPA.

Massive amount of Q themed info at Americans for Innovation.
The Miller Act is hugely important to subcontractors and suppliers when it comes to getting paid on a federal construction projects.
The Miller Act Claims
Who Really Owns the Military Industrial Complex: The Highland Group Exposed
Many readers to this site will be quite familiar with the usual suspects: the Rothchilds, Rockefellers, and big banksters who command the top tier of the human wealth pyramid. We also know that they work closely with government agencies to plan and implement continuing military, cyber, and economic wars. We have all read about how the Bilderberg Club, Illuminati, and the Knights of Malta coordinate these machinations with the Vatican. We know that the U.S. Federal Reserve is just a private corporation with a monopoly to print Federal Reserve notes that manipulates and plunders the U.S and global economy.
But there is a more secret group that directs the military in its future goals. One group, essentially one man, has been behind creating the direction of military and commercial warfare for decades. He founded the Highland Group which hosts forums for DARPA, Department of Defense, CIA, FBI, In-Q-Tel, Homeland Security, SAIC, and many other government agencies and organizations.
It is what we don’t know that interested us. So we decided to follow the money. Who are the war profiteers that are plundering American lives, wealth, and democracy?
Though much of the article has been discussed and brought to light in these threads over the past 2 years, this article helps put it all together.
2020
#626
#666
Happy Q year!
#626
Chatter exploding.
Change of narrative will be required.
[-4][-5]
Public to awaken [mass-start].
Sleeping pill reject.
OP Mockingbird FAILURE.
FAKE>REAL.
BLIND>20/20.
KILL_CHAIN.
Where we go one, we go ALL>
Q
#666
Why did the #Memo drop a Friday [& before the SB]?
Did this seem strange to you?
Watch the news.
Rothschild estate sale [Black Forest].
Stock market DIVE [666 - coincidence?].
Soros transfer of wealth.
Dopey FREED.
Marriage for POWER, not LOVE.
Hilton/Roth.
Soros/Clinton.
Etc.
News unlocks MAP.
Think Mirror.
Which team?
THEY don't know.
APACHE.
These people are EVIL.
Still don't believe you are SHEEP to them?
20/20 coming.
PUBLIC is VITAL.
RELEASE of INFO VITAL.
OUTRAGE.
JUSTICE.
Can we simply arrest the opposition w/o first exposing the TRUTH?
FOLLOW THE LIGHT.
Q
Happy Q year!
a reply to: KnoxMSP
Thank you for locating the Ivanka clock to Sacre-coure - Musee d'Orsay in Paris, FR, KnoxMSP!
I think It is important because of this corrected POTUS tweet last night:
original at 06:13:43 PM
corrected at 06:25:01 PM to
1) Difference = @parisac
I guess we all assumed @parisac was the official twitter account for the Paris Accord - but it's NOT!
@parisac is the twitter account for parisa chehrehsa, set up in June 2009.
The account has NEVER tweeted or replied and has no profile picture or information but has 50 followers (including android, iphone and games developers) and is following Obama and 6 others mostly with middle east names.
Parisa appears to be an Iranian hair stylist, artist and singer living in Concord California (MyLife.com link). She has 5 aliases and is linked to David Koenig and Terry and Cathy Baldwin. By 2013 she had become Parisa Vaaleh. Odd to see a singer/artist who never tweets?
She may be related to Sara Chehrehsa, a lawyer in San Francisco who represents high growth technology companies in venture capital and private equity financings, and mergers and acquisitions.
So where does this take us?
1) News focus is on Iran - parisa is Iranian living in California, a Democrat following Obama,
2) Possible link to a lawyer specialising in organising funding,
2) Ivanka appears as a black queen behind the clock face of a PARIS clock,
3) POTUS tweets, then removes @parisac.
4) Q1241 links Paris accord to Iran deal kickbacks to Europe,
5) Parisac = Paris bank account?
Now think why paratroopers have been airlifted into the Embassy in Iraq... just to defend? Or to extract evidence related to the Iran deal? The latter would explain why POTUS compared the Iraq Embassy to "Anti-benghazi":
In Benghazi, HRC didn't want a server to be found? In Iraq POTUS is securing evidence from the Embassy?
Thank you for locating the Ivanka clock to Sacre-coure - Musee d'Orsay in Paris, FR, KnoxMSP!
I think It is important because of this corrected POTUS tweet last night:
original at 06:13:43 PM
How is the Paris Accord doing? Don’t ask! @parisac
t.co...
corrected at 06:25:01 PM to
How is the Paris Accord doing? Don’t ask! t.co...
1) Difference = @parisac
I guess we all assumed @parisac was the official twitter account for the Paris Accord - but it's NOT!
@parisac is the twitter account for parisa chehrehsa, set up in June 2009.
The account has NEVER tweeted or replied and has no profile picture or information but has 50 followers (including android, iphone and games developers) and is following Obama and 6 others mostly with middle east names.
Parisa appears to be an Iranian hair stylist, artist and singer living in Concord California (MyLife.com link). She has 5 aliases and is linked to David Koenig and Terry and Cathy Baldwin. By 2013 she had become Parisa Vaaleh. Odd to see a singer/artist who never tweets?
She may be related to Sara Chehrehsa, a lawyer in San Francisco who represents high growth technology companies in venture capital and private equity financings, and mergers and acquisitions.
So where does this take us?
1) News focus is on Iran - parisa is Iranian living in California, a Democrat following Obama,
2) Possible link to a lawyer specialising in organising funding,
2) Ivanka appears as a black queen behind the clock face of a PARIS clock,
3) POTUS tweets, then removes @parisac.
4) Q1241 links Paris accord to Iran deal kickbacks to Europe,
5) Parisac = Paris bank account?
Now think why paratroopers have been airlifted into the Embassy in Iraq... just to defend? Or to extract evidence related to the Iran deal? The latter would explain why POTUS compared the Iraq Embassy to "Anti-benghazi":
In Benghazi, HRC didn't want a server to be found? In Iraq POTUS is securing evidence from the Embassy?
edit on 1-1-2020 by RelSciHistItSufi
because: (no reason given)
a reply to: RelSciHistItSufi
Nice detective work, Rel!
The @parisac > 'Paris AC' maps to the "AC Hotel Paris Porte Maillot" which is affiliated with Marriott Hotels Paris and is walking distance to Epstein's former Apartment on Avenue Foch and about 10 min drive via Arc de Triomphe to the Eiffel Tower where the pic in Q3647 was taken.
Another Qoincidence??
Nice detective work, Rel!
The @parisac > 'Paris AC' maps to the "AC Hotel Paris Porte Maillot" which is affiliated with Marriott Hotels Paris and is walking distance to Epstein's former Apartment on Avenue Foch and about 10 min drive via Arc de Triomphe to the Eiffel Tower where the pic in Q3647 was taken.
Another Qoincidence??
a reply to: RelSciHistItSufi
Re POTUS @parisac Paris Accord tweet and my dig this replies to...
I missed something important!
@parisac = ATPARISAC = anagram of AAA SCRIPT
IBM AAA script usage:
custom AAA script in XSL seems to be a way to hack through PUBLIC KEY AUTHORISATION in IBM websphere applications!:
Re POTUS @parisac Paris Accord tweet and my dig this replies to...
I missed something important!
@parisac = ATPARISAC = anagram of AAA SCRIPT
IBM AAA script usage:
I found an example of a custom AAA in XSL (www-01.ibm.com...). However I did not find any example in gateway script.
What is the protocol? How does my gateway script tell the rest of the policy whether the user has been authenticated or not?
custom AAA script in XSL seems to be a way to hack through PUBLIC KEY AUTHORISATION in IBM websphere applications!:
Configuring SFTP Front-side Handler Public Key authentication on the IBM WebSphere DataPower SOA Appliance
...
For this configuration, a AAA policy will have to be attached to the SFTP Server Front Side Handler to handle the SSH client authentication. In the AAA policy, you will have to configure a custom Authentication step to perform the Public Key authentication for the SSH client. In the custom authentication step, you can use a stylesheet to compare the Public key provided in the client's SSH connection to some known value or the client's public key uploaded and stored on the device. The public key presented in the client's SSH connection may be accessed through this variable 'var://context/INPUT/ssh/publickey'.
edit on 1-1-2020 by RelSciHistItSufi because: (no reason given)
a reply to: EndtheMadnessNow
Cheers for the value add EMN, and a Happy New Year to you and all!
Amazing how much info can be uncovered from one 8 character string = @parisac!
Cheers for the value add EMN, and a Happy New Year to you and all!
Amazing how much info can be uncovered from one 8 character string = @parisac!
Happy and prosperous new year guys and gals.
Fight fight fight.
Fight fight fight.
a reply to: liveandlearn
Back in 2003 etc. Wordpad used a Font called Wingdings, someone noted how typing Q93 in such showed a drawn aeroplan with two tall objects in front. This was followed by the Codes in which MSM use of WWW. was the start of anti-christ as in Greek and Hebrew Alphabets the W was number 6. ;;Example enclosed
www.av1611.org...
So it was a prior to this sort of srgument that went like a rocket.
Back in 2003 etc. Wordpad used a Font called Wingdings, someone noted how typing Q93 in such showed a drawn aeroplan with two tall objects in front. This was followed by the Codes in which MSM use of WWW. was the start of anti-christ as in Greek and Hebrew Alphabets the W was number 6. ;;Example enclosed
www.av1611.org...
So it was a prior to this sort of srgument that went like a rocket.
WTH?
Judge in Hunter Biden's Arkansas paternity case abruptly recuses himself
www.foxnews.com...
No reason given. Dollars to donuts that judge did this to avoid his “suicide”.
Judge in Hunter Biden's Arkansas paternity case abruptly recuses himself
www.foxnews.com...
No reason given. Dollars to donuts that judge did this to avoid his “suicide”.
Ok back to full speed lol
Panic in DC MSN
Trump Throws Fresh Fuel on Dangerous QAnon Conspiracy Theory
www.thedailybeast.com...
Panic in DC MSN
Trump Throws Fresh Fuel on Dangerous QAnon Conspiracy Theory
www.thedailybeast.com...
But then again up is down and so on
Dan Silva
@DanSilv56084248
twitter.com...
Replying to @SebGorka
Q is PSYOP formulated by military intelligence to teach public how to think critically and point the citizenry to information hidden and not reported. The entire MSM is owned by 6 corrupt companies, a work around was necessary.
Ignore at your peril.
twitter.com...
Dan Silva
@DanSilv56084248
twitter.com...
Replying to @SebGorka
Q is PSYOP formulated by military intelligence to teach public how to think critically and point the citizenry to information hidden and not reported. The entire MSM is owned by 6 corrupt companies, a work around was necessary.
Ignore at your peril.
twitter.com...
a reply to: steaming
I will admit I did grasp some of what the article is saying, however, hebrew is greek to me. And the seeming difference in Hebrew and Jewish gematria I definitely don't get. I am too old and not worth wasting time on to understand.
My thoughts on this was that in the beginning of (our letter my laptop refuses to print) there was the simple use of
4 10 20 for DJT then we jumped to the, complicated for many, use of gematria. Not really something most of us know or understand.
I will admit I did grasp some of what the article is saying, however, hebrew is greek to me. And the seeming difference in Hebrew and Jewish gematria I definitely don't get. I am too old and not worth wasting time on to understand.
My thoughts on this was that in the beginning of (our letter my laptop refuses to print) there was the simple use of
4 10 20 for DJT then we jumped to the, complicated for many, use of gematria. Not really something most of us know or understand.
originally posted by: Trillium
Ok back to full speed lol
Panic in DC MSN
Trump Throws Fresh Fuel on Dangerous QAnon Conspiracy Theory
www.thedailybeast.com...
Private investigator Dominic Casey also wants to be added to the case, claiming he had obtained Biden’s bank records citing Biden was involved in a counterfeiting scheme in Ukraine that accumulated a $150M fortune.
Ben Tallmadge twitter
Haven't checked this out.
a reply to: EndtheMadnessNow
Yeah, although the seem to have some experience, they're still pretty green behind the ears.
Either way, I felt the show was quite a refreshing watch (moreso in terms of the content) considering the plethora of tacky sci-fi, true crime and food shows filling Netflix and the like.
I did note Covington link, but honestly didn't pay it much mind l.
I just remembered that I found Hellier mentioned in the twitter link someone posted on here with the overlaid maps of the extensive cave system in North America and the reported missing persons.
Ahh yes, you posted the stuff about the Randonauts recently I believe? I have it in one of my MANY open tabs right now, but haven't had a good dig into it yet. Don't know enough about it to comment yet
Yeah, although the seem to have some experience, they're still pretty green behind the ears.
Either way, I felt the show was quite a refreshing watch (moreso in terms of the content) considering the plethora of tacky sci-fi, true crime and food shows filling Netflix and the like.
I did note Covington link, but honestly didn't pay it much mind l.
I just remembered that I found Hellier mentioned in the twitter link someone posted on here with the overlaid maps of the extensive cave system in North America and the reported missing persons.
Ahh yes, you posted the stuff about the Randonauts recently I believe? I have it in one of my MANY open tabs right now, but haven't had a good dig into it yet. Don't know enough about it to comment yet
a reply to: onehuman
Re: Embedded FoxNews Clip at: theconservativetreehouse.com...
He looks to be one of the "crisis actors" organizers. Just before that view is cut away from, you can see one of his colleagues grab his arm, to pull him out of the shot.
Re: Embedded FoxNews Clip at: theconservativetreehouse.com...
He looks to be one of the "crisis actors" organizers. Just before that view is cut away from, you can see one of his colleagues grab his arm, to pull him out of the shot.
new topics
-
Leaving the US due to severe TDS?
US Political Madness: 20 minutes ago -
Just a thought by Matt Walsh on the election
2024 Elections: 9 hours ago -
Trump's truth and reconciliation commission
Politicians & People: 9 hours ago -
Liberal women going on sex strike over Trump win
US Political Madness: 10 hours ago -
Where ARE the 20 million votes??? Where ARE they????? WHERE???
US Political Madness: 11 hours ago
top topics
-
Where ARE the 20 million votes??? Where ARE they????? WHERE???
US Political Madness: 11 hours ago, 28 flags -
Just a thought by Matt Walsh on the election
2024 Elections: 9 hours ago, 16 flags -
The Democratic Party’s Stay Behind Program
US Political Madness: 13 hours ago, 13 flags -
President-Elect DONALD TRUMP's 2nd-Term Administration Takes Shape.
Political Ideology: 12 hours ago, 12 flags -
82 yr Woman Arrested for Hate Crime after Assaulting Trump Supporters
2024 Elections: 16 hours ago, 10 flags -
Liberal women going on sex strike over Trump win
US Political Madness: 10 hours ago, 8 flags -
Celestial Objects in Far Northern Reaches of Alaska (Polar Mystery)
Fragile Earth: 14 hours ago, 7 flags -
Groaners II
Jokes, Puns, & Pranks: 17 hours ago, 3 flags -
Trump's truth and reconciliation commission
Politicians & People: 9 hours ago, 2 flags -
Leaving the US due to severe TDS?
US Political Madness: 20 minutes ago, 1 flags
active topics
-
Leaving the US due to severe TDS?
US Political Madness • 2 • : Dandandat3 -
82 yr Woman Arrested for Hate Crime after Assaulting Trump Supporters
2024 Elections • 21 • : Xtrozero -
Liberal women going on sex strike over Trump win
US Political Madness • 25 • : PorkChop96 -
Where is Kamala?
US Political Madness • 69 • : Blackstone0523 -
Where ARE the 20 million votes??? Where ARE they????? WHERE???
US Political Madness • 31 • : Blackstone0523 -
Just a thought by Matt Walsh on the election
2024 Elections • 4 • : watchitburn -
Why Dems Are Probably Wishing Trump Won in 2020...
US Political Madness • 5 • : putnam6 -
On Nov. 5th 2024 - AMERICANS Prevented the Complete Destruction of America from Within.
2024 Elections • 126 • : Oldcarpy2 -
Kamala Address the Nation -- Nov 6 2024 4pm EST
2024 Elections • 75 • : tjack -
Trump's truth and reconciliation commission
Politicians & People • 6 • : Flyingclaydisk
