It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
There have been many claims that "there is no evidence" regarding the identity of those responsible for hacks of the DNC, DCCC and John Podesta's
email. In a truly surreal development, it's also being claimed by many, not least of which President-elect Trump, that allegations that the Russian
government was behind the hacks are a recent development that is part of a ficticious post-election narrative intended to delegitimize the election of
Trump.
In reality, Russian responsibility has been indicated since the very first public revelation of the DNC hack and considerable evidence has been publicly available for six months (as it happens, exactly six as of the writing of this post).
While we wait to see if information from the CIA assessment will be released or better, the results of a comprehensive investigation with Congressional oversight, it seems useful to apprise ourselves of what is currently available from non-government sources (and non media for that matter). This is something of a follow up to an earlier thread of mine from October 1st. I cannot possibly hope to cover even a fraction of what has been written by cyber security experts in regards to these events and those believed to be responsible. In fact, as I was composing this thread it became clear that I would have to divide what information I have over two threads and possibly a third. Given my two orphaned "Part 1" threads from the last few months, I'm not putting the "Part 1" jinx in the title but there will be a second one, hopefully later today.
In this first thread, I'll touch on the initial tip-off that the DNC was being actively targeting which in turn triggered the DNC to call in CrowdStrike. I will also cover information pertaining to one of the two threat actors identified by CrowdStrike, Fancy Bear.
Yahoo
According to both the DNC and CrowdStrike, the cyber security firm had been contracted in May after DNC consultant Alexandra Chalupa, who was investigating then Trump campaign manager Paul Manafort's ties to the Kremlin, began receiving ominous pop-up messages from Yahoo when logging into her personal email account and contacted Luis Miranda, the DNC's national communications director.
Ironically, evidence of this happening can be found in the hacked DNC emails published by WikiLeaks. In the DNC emails archive, refer to the email with id 3962. Here's the text of the email which was forwarded to by Miranda to Mark Paustenbach:
At the bottom of the body of the email, the following image from Yahoo was embedded (included in WikiLeak's archive):
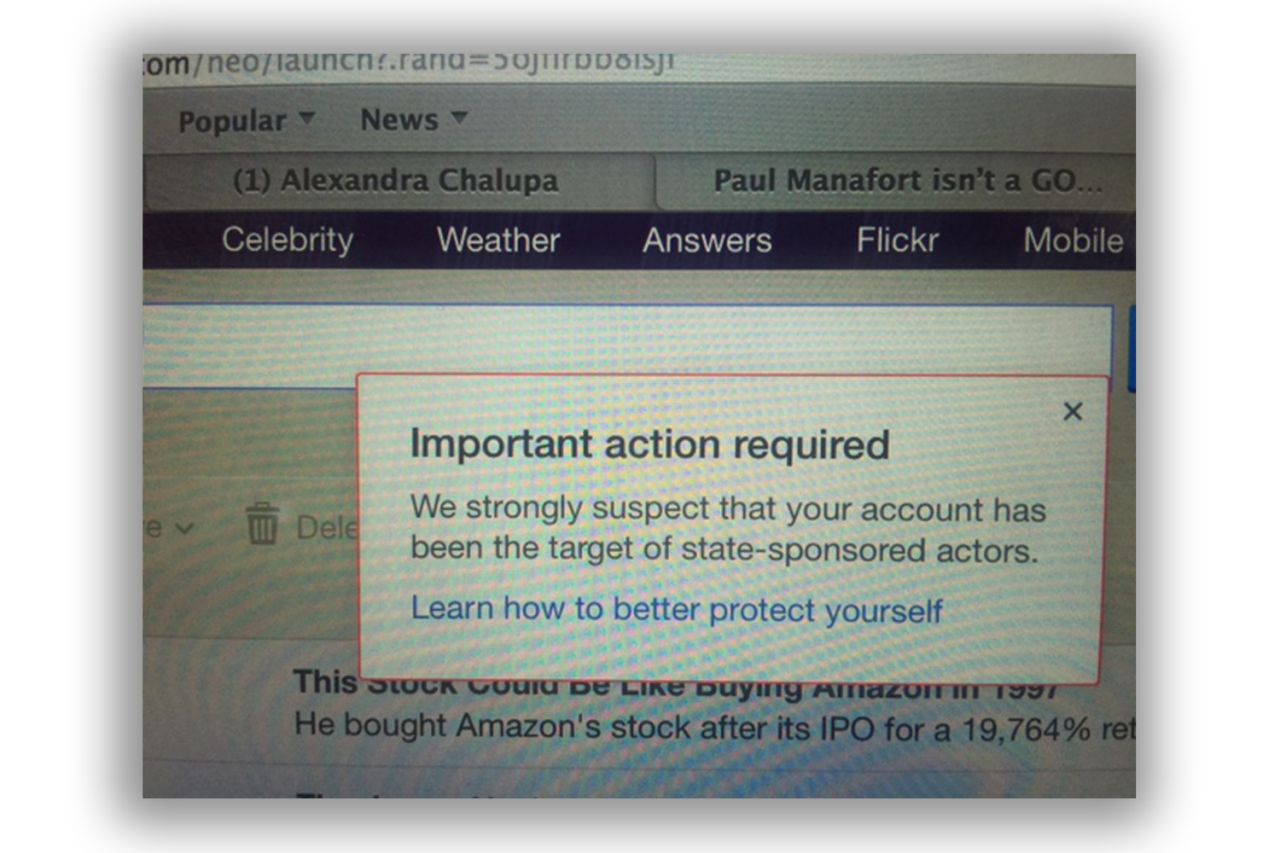
The authenticity of this particular variety of warning notification is substantiated by a blog post from Bob Lord, Yahoo's Chief Information Security Officer, posted in December of 2015:
CrowdStrike
I have not come across any information as to the precise date that CrowdStrike began its work but it would make sense that it was sometime after May 3rd but not much later than May 25th which is the newest email from the DNC emails archive on WikiLeaks based on my search. According to CrowdStrike co-founder and CTO, Dmitri Alperovitch, the intruders were monitored over a period of weeks. The intruders were kicked out the weekend of June 10th-11th.
In other words, the intruders were caught in the act, their activities were closely monitored and they were unable to remove evidence of their activities. Here's a clip from an interview of Alperovitch by Wolf Blitzer, conducted last night (12/12):
On June 14th, 2016, Alperovitch publicly revealed that DNC systems had been hacked and provided evidence collected by his firm in a blog post. The evidence obtained by CrowdStrike is the highest quality evidence provided to the public.
Bears in the Midst: Intrusion into the Democratic National Committee
In reality, Russian responsibility has been indicated since the very first public revelation of the DNC hack and considerable evidence has been publicly available for six months (as it happens, exactly six as of the writing of this post).
While we wait to see if information from the CIA assessment will be released or better, the results of a comprehensive investigation with Congressional oversight, it seems useful to apprise ourselves of what is currently available from non-government sources (and non media for that matter). This is something of a follow up to an earlier thread of mine from October 1st. I cannot possibly hope to cover even a fraction of what has been written by cyber security experts in regards to these events and those believed to be responsible. In fact, as I was composing this thread it became clear that I would have to divide what information I have over two threads and possibly a third. Given my two orphaned "Part 1" threads from the last few months, I'm not putting the "Part 1" jinx in the title but there will be a second one, hopefully later today.
In this first thread, I'll touch on the initial tip-off that the DNC was being actively targeting which in turn triggered the DNC to call in CrowdStrike. I will also cover information pertaining to one of the two threat actors identified by CrowdStrike, Fancy Bear.
Yahoo
According to both the DNC and CrowdStrike, the cyber security firm had been contracted in May after DNC consultant Alexandra Chalupa, who was investigating then Trump campaign manager Paul Manafort's ties to the Kremlin, began receiving ominous pop-up messages from Yahoo when logging into her personal email account and contacted Luis Miranda, the DNC's national communications director.
Ironically, evidence of this happening can be found in the hacked DNC emails published by WikiLeaks. In the DNC emails archive, refer to the email with id 3962. Here's the text of the email which was forwarded to by Miranda to Mark Paustenbach:
From: Chalupa, Ali
Sent: Tuesday, May 03, 2016 11:56 PM
To: Miranda, Luis
Subject: Re: You saw this, right?
A lot more coming down the pipe. I spoke to a delegation of 68 investigative journalists from Ukraine last Wednesday at the Library of Congress - the Open World Society's forum - they put me on the program to speak specifically about Paul Manafort and I invited Michael Isikoff whom I've been working with for the past few weeks and connected him to the Ukrainians. More offline tomorrow since there is a big Trump component you and Lauren need to be aware of that will hit in next few weeks and something I'm working on you should be aware of.
Since I started digging into Manafort these messages have been a daily occurrence on my yahoo account despite changing my password often:
At the bottom of the body of the email, the following image from Yahoo was embedded (included in WikiLeak's archive):

The authenticity of this particular variety of warning notification is substantiated by a blog post from Bob Lord, Yahoo's Chief Information Security Officer, posted in December of 2015:
We’re committed to protecting the security and safety of our users, and we strive to detect and prevent unauthorized access to user accounts by third parties. As part of this effort, Yahoo will now notify you if we strongly suspect that your account may have been targeted by a state-sponsored actor. We’ll provide these specific notifications so that our users can take appropriate measures to protect their accounts and devices in light of these sophisticated attacks.
CrowdStrike
I have not come across any information as to the precise date that CrowdStrike began its work but it would make sense that it was sometime after May 3rd but not much later than May 25th which is the newest email from the DNC emails archive on WikiLeaks based on my search. According to CrowdStrike co-founder and CTO, Dmitri Alperovitch, the intruders were monitored over a period of weeks. The intruders were kicked out the weekend of June 10th-11th.
In other words, the intruders were caught in the act, their activities were closely monitored and they were unable to remove evidence of their activities. Here's a clip from an interview of Alperovitch by Wolf Blitzer, conducted last night (12/12):
On June 14th, 2016, Alperovitch publicly revealed that DNC systems had been hacked and provided evidence collected by his firm in a blog post. The evidence obtained by CrowdStrike is the highest quality evidence provided to the public.
Bears in the Midst: Intrusion into the Democratic National Committee
CrowdStrike Services Inc., our Incident Response group, was called by the Democratic National Committee (DNC), the formal governing body for the US Democratic Party, to respond to a suspected breach. We deployed our IR team and technology and immediately identified two sophisticated adversaries on the network – COZY BEAR and FANCY BEAR. We’ve had lots of experience with both of these actors attempting to target our customers in the past and know them well. In fact, our team considers them some of the best adversaries out of all the numerous nation-state, criminal and hacktivist/terrorist groups we encounter on a daily basis. Their tradecraft is superb, operational security second to none and the extensive usage of ‘living-off-the-land’ techniques enables them to easily bypass many security solutions they encounter. In particular, we identified advanced methods consistent with nation-state level capabilities including deliberate targeting and ‘access management’ tradecraft – both groups were constantly going back into the environment to change out their implants, modify persistent methods, move to new Command & Control channels and perform other tasks to try to stay ahead of being detected. Both adversaries engage in extensive political and economic espionage for the benefit of the government of the Russian Federation and are believed to be closely linked to the Russian government’s powerful and highly capable intelligence services.
To properly evaluate the significance of the evidence, it's critically important to understand how security professionals identify threat
actors (hackers/hacking teams). The simplest way of thinking of it would be much how traditional detectives operate in the offline world. Even
when the evidence doesn't point to a suspect's identity, it can be used to positively link that person's crimes. Much as a serial offender might be
known by a monicker given by law enforcement (e.g. "The Gentleman Bandit"), known threat actors are given names by security teams. And just like their
counterparts in the offline world, cyber security pros construct profiles of their suspects.
One of the most useful methods for identifying the threat actor behind an intrusion forensically is by examining the tools that get left behind when the threat actor is caught in the act. As you'd probably guess, the toolkits of upper echelon professionals are considerably more sophisticated than those used by others. These tools may be in active development by mulitple devs over the span of years, constantly refined and updated to incorporate new features and to keep pace with evolving detection measures. In a competitive environment where obscurity is a vital part of avoiding detection, it's not good to share your warez and for this reason, high level threat actors can be tightly linked to their unique tools.
CrowdStrike identified two separate threat actors working independently within the DNC systems. The next two sections will detail the evidence for the identification of each.
Fancy Bear
Fancy Bear is CrowdStrike's name for the threat actor also known by the following names and others: APT28 (FireEye), Sofacy (Kaperskey, PwC), TG-4127 (Dell SecureWorks CTU), Pawn Storm (Trend Micro), Sednit (ESET, Trend Micro), Strontium (Microsoft) and Tsar Team.
It is believed to have been active since at least 2004 and possibly earlier. According to CrowdStrike, they breached the DNC in April of 2016.
From Alperovitch's post:
In the Indicators of Compromise (IOC) section at the bottom of his post, Alperovitch lists two pieces of malware in the Fancy Bear toolkit that were discovered in the DNC systems:

Slovakian security firm ESET has an exhaustive and thoroughly comprehensive analysis of both of these implants in the following document: En Route With Sednet Part: Observering the Comings & Goings (PDF).
Xagent/X-Agent (aka SPLM, CHOPSTICK)
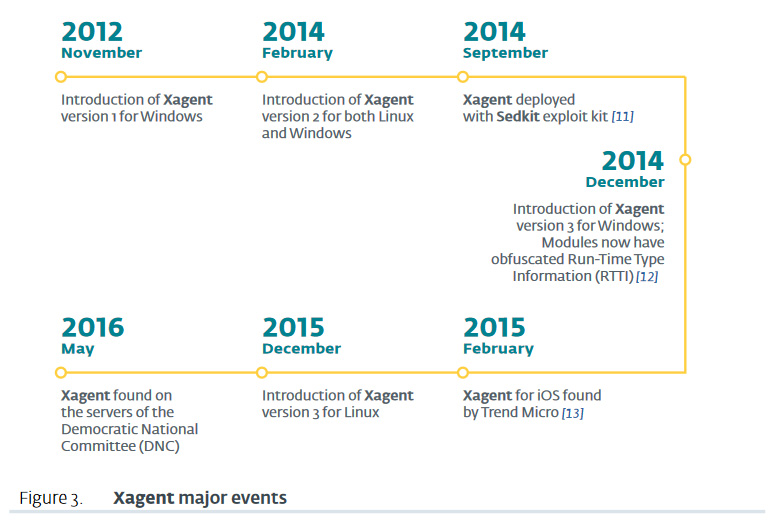
A brief list of X-Agent's capabilities can be found on Mitre's ATT&CK wiki here.
XTunnel/X-Tunnel/
CrowdStrike shared samples of the recovered binaries with members of the security community. In July, security expert Pat Belcher of Invincea did an analysis of this iteration of X-Tunnel:
Tunnel of Gov: DNC Hack and the Russian XTunnel
X-Tunnel started out back in 2004 as an open source utility from a Chinese VoIP company called Xten. The project became closed source later when the Xten was folded into its parent company. While that early code formed the early basis for Fancy Bear's proprietary X-Tunnel — as is the case with dogs and bears, who have also have a common ancestor — it's evolved into a whole new animal.
One of the most useful methods for identifying the threat actor behind an intrusion forensically is by examining the tools that get left behind when the threat actor is caught in the act. As you'd probably guess, the toolkits of upper echelon professionals are considerably more sophisticated than those used by others. These tools may be in active development by mulitple devs over the span of years, constantly refined and updated to incorporate new features and to keep pace with evolving detection measures. In a competitive environment where obscurity is a vital part of avoiding detection, it's not good to share your warez and for this reason, high level threat actors can be tightly linked to their unique tools.
CrowdStrike identified two separate threat actors working independently within the DNC systems. The next two sections will detail the evidence for the identification of each.
Fancy Bear
Fancy Bear is CrowdStrike's name for the threat actor also known by the following names and others: APT28 (FireEye), Sofacy (Kaperskey, PwC), TG-4127 (Dell SecureWorks CTU), Pawn Storm (Trend Micro), Sednit (ESET, Trend Micro), Strontium (Microsoft) and Tsar Team.
It is believed to have been active since at least 2004 and possibly earlier. According to CrowdStrike, they breached the DNC in April of 2016.
From Alperovitch's post:
FANCY BEAR adversary used different tradecraft, deploying X-Agent malware with capabilities to do remote command execution, file transmission and keylogging. It was executed via rundll32 commands such as:
rundll32.exe “C:Windowstwain_64.dll”
In addition, FANCY BEAR’s X-Tunnel network tunneling tool, which facilitates connections to NAT-ed environments, was used to also execute remote commands. Both tools were deployed via RemCOM, an open-source replacement for PsExec available from GitHub. They also engaged in a number of anti-forensic analysis measures, such as periodic event log clearing (via wevtutil cl System and wevtutil cl Security commands) and resetting timestamps of files.
In the Indicators of Compromise (IOC) section at the bottom of his post, Alperovitch lists two pieces of malware in the Fancy Bear toolkit that were discovered in the DNC systems:

Slovakian security firm ESET has an exhaustive and thoroughly comprehensive analysis of both of these implants in the following document: En Route With Sednet Part: Observering the Comings & Goings (PDF).
Xagent/X-Agent (aka SPLM, CHOPSTICK)
Xagent is the flagship backdoor of the Sednit group, deployed by them in many of their operations over the past two years. It is usually dropped on targets deemed interesting by the operators after a reconnaissance phase, but it has also been used as first-stage malware in a few cases.

Distinguishing characteristics
• Xagent is developed in C++ with a modular architecture, around a core module named AgentKernel
• Xagent has been compiled for Windows, Linux and iOS (at least)
• Xagent possesses two different implementations of its C&C communication channel, one over HTTP and the other over emails (SMTP/POP3 protocols)
• Xagent binaries are often compiled for specific targets, with a special choice of modules and communication channels
A brief list of X-Agent's capabilities can be found on Mitre's ATT&CK wiki here.
XTunnel/X-Tunnel/
CrowdStrike shared samples of the recovered binaries with members of the security community. In July, security expert Pat Belcher of Invincea did an analysis of this iteration of X-Tunnel:
Tunnel of Gov: DNC Hack and the Russian XTunnel
Crowdstrike released the hashes of binaries found for both the Cozy Bear and the Fancy Bear breaches. In this blog, we are going to discuss the capabilities of the Fancy Bear XTunnel binary, which posed as a file called “vmupgradehelper.exe.” Its MD5 is 9e7053a4b6c9081220a694ec93211b4e, and you can view its capabilities online here.
Invincea uses its DARPA-funded deep learning to automatically analyze and extract known capabilities of malware based on matching strings to StackOverflow definitions, and where possible, cluster them into related families of malware based on similarities of design and function. The XTunnel malware used by Russian threat actor Fancy Bear did not cluster with other known malware, meaning this binary was likely a purpose-built original piece of code to be used specifically against the DNC. However, while it may not cluster, it certainly does list its capabilities.
The XTunnel tool having VPN-style capabilities of course uses encryption, including exchanging SSH keys, using private encryption keys, compresses and decompresses data, etc. However, the remaining functionality and configurability of the XTunnel tool spelled doom for the DNC. The tool supports access to locally stored passwords and can even access the LDAP server. It is modular, so it can download additional files, probe the network for open ports, PING hosts and send and receive emails.
X-Tunnel started out back in 2004 as an open source utility from a Chinese VoIP company called Xten. The project became closed source later when the Xten was folded into its parent company. While that early code formed the early basis for Fancy Bear's proprietary X-Tunnel — as is the case with dogs and bears, who have also have a common ancestor — it's evolved into a whole new animal.
edit on 2016-12-14 by theantediluvian because:
(no reason given)
Also from the IOC table at the bottom of Alperovitch's post are the destination IP addresses and ports of the implants' command and control (C2) node.
You'll notice that the port used in each case is 443 (HTTPS):

The first IP address is owned by a Swedish VPS company called Yourserver which accepts among other payment types, Bitcoin (BTC). The next is owned by Vultr, another VPS provider, which appears to be based in San Jose but has servers in Paris, Frankfurt, London and Amsterdam. Interesting Vultr has per hour billing. Starting in October of 2014, Vultr accepted payments in BTC but stopped in April of 2016 because:
The last address belongs to another hosting outfit, Swiftway Communications (Swiftway.net), which has operations in Europe & the US. It's unclear if they do or have taken BTC or another cryptocurrency. While it's always possible that the C2 nodes could be themselves compromised systems, there is good reason to believe that the Vultr host was not. This additional information comes from ThreatConnect in a post from June 17, 2016.
Rebooting Watergate: Tapping into the Democratic National Committee
In other words, the IP address for one of the two C2 nodes for X-Tunnel had previously been used for the domain misdepatrment.com which was clearly part of a spearphishing campaign launched against MIS Department, an IT services company whose first two clients listed were Obama/Biden and the DNC. Interestingly, as of the time that I'm writing this, the company's website is simply their logo against a solid background.
Dell SecureWorks
From the last excerpt above, you'll see mention of a SecureWorks report. The following excerpts are taken from that report.
Threat Group-4127 Targets Hillary Clinton Presidential Campaign
Here's an example of the Fancy Bear/APT28/TG-4127 fraudulent Google Accounts login page:
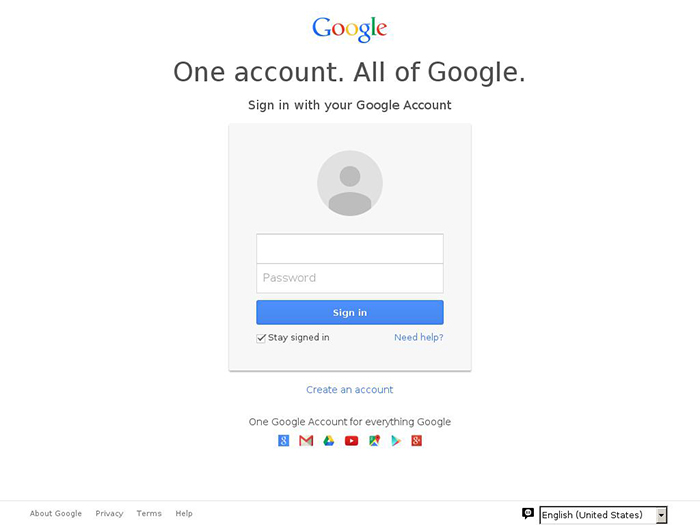
You'll need to read the report for full details of the multiple attacks revealed by SecureWorks but here are details relating to the Clinton campaign and the DNC:

The first IP address is owned by a Swedish VPS company called Yourserver which accepts among other payment types, Bitcoin (BTC). The next is owned by Vultr, another VPS provider, which appears to be based in San Jose but has servers in Paris, Frankfurt, London and Amsterdam. Interesting Vultr has per hour billing. Starting in October of 2014, Vultr accepted payments in BTC but stopped in April of 2016 because:
"significant portion of ToS violators paying with Bitcoin."
The last address belongs to another hosting outfit, Swiftway Communications (Swiftway.net), which has operations in Europe & the US. It's unclear if they do or have taken BTC or another cryptocurrency. While it's always possible that the C2 nodes could be themselves compromised systems, there is good reason to believe that the Vultr host was not. This additional information comes from ThreatConnect in a post from June 17, 2016.
Rebooting Watergate: Tapping into the Democratic National Committee
In building upon Crowdstrike’s analysis, ThreatConnect researched and shared 20160614A: Russia-based groups compromise Democratic National Committee within the ThreatConnect Common Community. This incident includes the IP address 45.32.129[.]185 which Crowdstrike lists as a FANCY BEAR X-Tunnel implant Command and Control (C2) node.
Using ThreatConnect’s Farsight passive DNS integration to review the resolution history for 45.32.129[.]185 we uncovered some additional domain resolutions. One of these domain resolutions is the suspicious domain misdepatrment[.]com (note the transposition of the “t” and the “r” in department).
In reviewing the Domain Whois information, our DomainTools integration reveals that the domain was registered on March 22, 2016 by frank_merdeux@europe[.]com.
The domain misdepatrment[.]com was registered on March 22, 2016. Farsight lists the earliest domain resolution as March 24, 2016. On April 24th, 2016 the domain misdepatrment[.]com moved from the parking IP Address 5.135.183[.]154 to the FANCY BEAR Command and Control IP Address 45.32.129[.]185 where it remains resolved at of the time of this writing.
It is important to note that within the Crowdstrike blog, the authors make two key distinctions:
“This group is known for its technique of registering domains that closely resemble domains of legitimate organizations they plan to target.”
The domain misdepatrment[.]com closely resembles the legitimate domain for misdepartment.com. Of note, MIS Department Inc. is a technology services provider that lists a variety of clients on its website, one of which is the DNC. Their staff profiles include individuals who provided technical leadership and expertise to the Obama-Biden Campaigns as well as the DNC. Any attacker targeting a particular victim would find the most success targeting organizations and individuals who have administrative access across enterprise assets.
In other words, the IP address for one of the two C2 nodes for X-Tunnel had previously been used for the domain misdepatrment.com which was clearly part of a spearphishing campaign launched against MIS Department, an IT services company whose first two clients listed were Obama/Biden and the DNC. Interestingly, as of the time that I'm writing this, the company's website is simply their logo against a solid background.
On June 16, 2016 Secureworks reported that a Russia-based group, operating on behalf of the Russian government, used a combination of (link tracking not allowed) short links and a fake Google login page to target the Clinton Campaign between mid-March and mid-May 2016. The group, dubbed TG-4127 (aka APT28, Sofacy, Sednit, and Pawn Storm), also targeted DNC staff between mid-March and mid-April 2016. This timeline is consistent with the misdepatrment[.]com registration and resolution changes as well as CrowdStrike’s assessment of FANCY BEAR tactics, techniques, and procedures (TTP).
Dell SecureWorks
From the last excerpt above, you'll see mention of a SecureWorks report. The following excerpts are taken from that report.
Threat Group-4127 Targets Hillary Clinton Presidential Campaign
Between October 2015 and May 2016, CTU researchers analyzed 8,909 Bitly links that targeted 3,907 individual Gmail accounts and corporate and organizational email accounts that use Gmail as a service. In March 2016, CTU researchers identified a spearphishing campaign using Bitly accounts to shorten malicious URLs.
The short links in the spearphishing emails redirected victims to a TG-4127-controlled URL that spoofed a legitimate Google domain. A Base64-encoded string containing the victim's full email address is passed with this URL, prepopulating a fake Google login page displayed to the victim. If a victim enters their credentials, TG-4127 can establish a session with Google and access the victim's account. The threat actors may be able to keep this session alive and maintain persistent access.
Here's an example of the Fancy Bear/APT28/TG-4127 fraudulent Google Accounts login page:

You'll need to read the report for full details of the multiple attacks revealed by SecureWorks but here are details relating to the Clinton campaign and the DNC:
CTU researchers observed the first short links targeting hillaryclinton.com email addresses being created in mid-March 2016; the last link was created in mid-May. During this period, TG-4127 created 213 short links targeting 108 email addresses on the hillaryclinton.com domain. Through open-source research, CTU researchers identified the owners of 66 of the targeted email addresses. There was no open-source footprint for the remaining 42 addresses, suggesting that TG-4127 acquired them from another source, possibly other intelligence activity.
The U.S. Democratic party's governing body, the Democratic National Committee (DNC), uses the dnc.org domain for its staff email. Between mid-March and mid-April 2016, TG-4127 created 16 short links targeting nine dnc.org email accounts. CTU researchers identified the owners of three of these accounts; two belonged to the DNC's secretary emeritus, and one belonged to the communications director. Four of the 16 short links were clicked, three by the senior staff members. As of this publication, dnc.org does not use the Google Apps Gmail email service. However, because dnc.org email accounts were targeted in the same way as hillaryclinton.com accounts, it is likely that dnc.org did use Gmail at that time and later moved to a different service.
Full disclosure: You'll notice from the SecureWorks report that they identify Fancy Bear as a Russian state-sponsored threat actor with moderate
confidence which is a step below high confidence.
I will now touch on a few of the principal threads of evidence supporting the identification of Fancy Bear as a team within or controlled by the Russian intelligence apparatus. In October of 2014, cyber security firm FireEye designated the Fancy Bear team APT28 and released a comprehensive, 45-page report making their case for the identification of APT28 as a Russian, state-sponsored threat actor. Like everything else I've linked, I strongly suggest reading all documents in their entirety. (Nobody said getting to the truth would be easy, did they?) First a table from the blog post announcing the report, summarizing key points from the document:
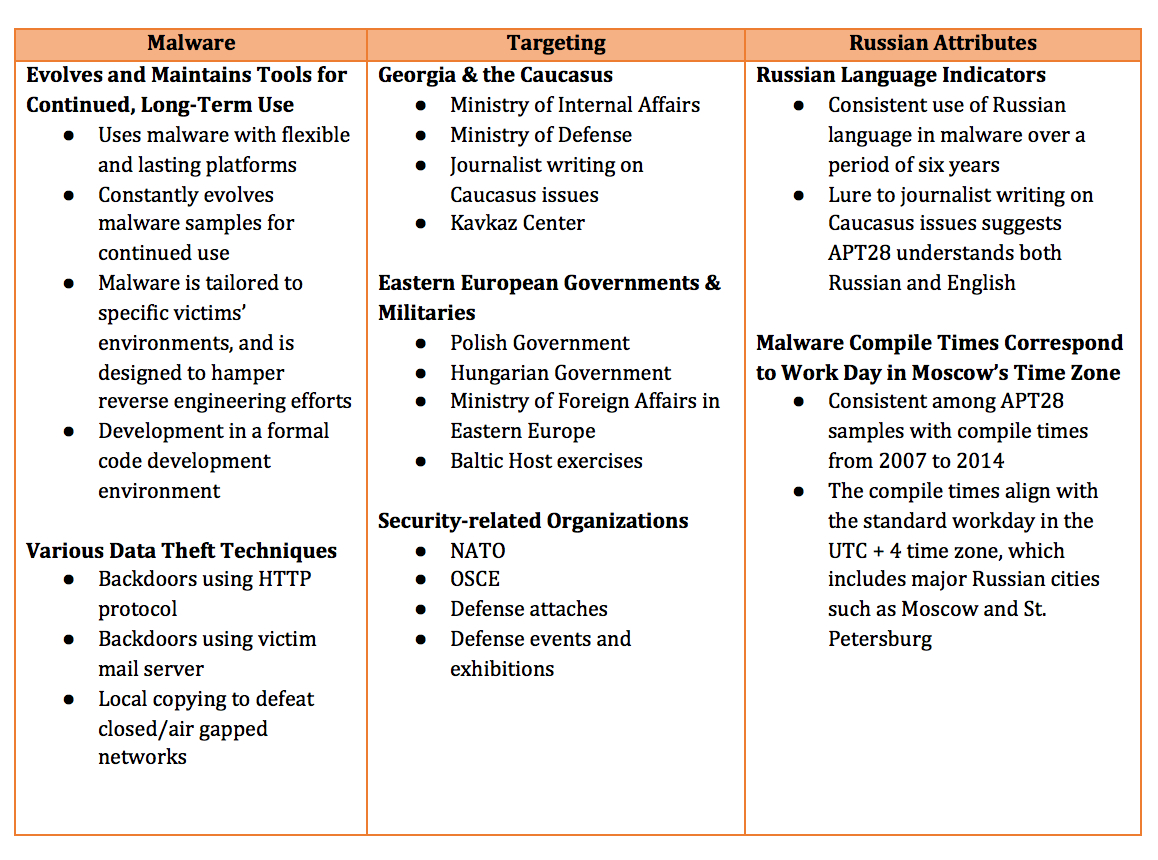
And here are relevant exceprts from the document for two of these items pointing to Russian origin:
APT28: A WINDOW INTO RUSSIA’S CYBER ESPIONAGE OPERATIONS? (PDF)
The table shows 59 samples with Russian language settings, 27 US English, 16 language neutral and 1 UK English.
Other researchers have come to similar conclusions based on their own analysis. The consensus view is that the malware employed by Fancy Bear is Russian in origin. This doesn't in of itself prove that Fancy Bear is a Russian outfit but it's a significant piece of the puzzle. Another piece that is covered in the same report is the group's choice in targets. I debated where to put this next bit but I think it fits well here.
German Spy Service Says Russia Behind Major Cyber Attacks
BfV is Bundesamt für Verfassungsschutz, the German domestic intelligence agency btw. As it turns out, beyond the identification by multiple independent cyber security firms/experts of Fancy Bear as the responsible party in both instances, there is forensic evidence linking the Bundestag hack to the DNC hack.
Digital Attack on German Parliament: Investigative Report on the Hack of the Left Party Infrastructure in Bundestag
Noted security researcher Thomas Rid, professor, Department of War Studies at King’s College London, discovered that a hardcoded IP address for a C2 node from the binaries recovered from the DNC systems (not one of the few included in the IOC table in the CrowdStrike post) was also hardcoded in the samples retreived in the Bundestag hack — 176.31.112[.]10.
Rid also discovered that the same SSL certificate used for encrypting communications with the C2 node in the Bundestag hack was also used for 23.227.196[.]217, the X-Tunnel C2 IP that was previously used for the MIS Department spearphishing site.
I will now touch on a few of the principal threads of evidence supporting the identification of Fancy Bear as a team within or controlled by the Russian intelligence apparatus. In October of 2014, cyber security firm FireEye designated the Fancy Bear team APT28 and released a comprehensive, 45-page report making their case for the identification of APT28 as a Russian, state-sponsored threat actor. Like everything else I've linked, I strongly suggest reading all documents in their entirety. (Nobody said getting to the truth would be easy, did they?) First a table from the blog post announcing the report, summarizing key points from the document:

And here are relevant exceprts from the document for two of these items pointing to Russian origin:
APT28: A WINDOW INTO RUSSIA’S CYBER ESPIONAGE OPERATIONS? (PDF)
During our research into APT28’s malware, we noted two details consistent across malware samples. The first was that APT28 had consistently compiled Russian language settings into their malware. The second was that malware compile times from 2007 to 2014 corresponded to normal business hours in the UTC + 4 time zone, which includes major Russian cities such as Moscow and St. Petersburg.
Use of Russian and English Language Settings in PE Resources
PE resources include language information that can be helpful if a developer wants to show user interface items in a specific language. 25 Non-default language settings packaged with PE resources are dependent on the developer’s build environment. Each PE resource includes a “locale” identifier with a language ID “composed of a primary language identifier indicating the language and a sublanguage identifier indicating the country/region.” 26
At the time of the writing of this paper, we had identified 103 malware samples that were both attributed to APT28 and contained PE resources. Table 5 shows the locale identifiers 27 with associated language and country/region for these samples.
Compile Times Align with Working Hours in Moscow and St. Petersburg
Of the 140 malware samples that we have attributed to APT28 so far, over 89% were compiled between 0400 and 1400 UTC time, as depicted in Figure 10. Over 96% were compiled between Monday and Friday. This parallels the working hours in UTC+0400 (that is, compile times begin about 8AM and end about 6PM in this time zone). This time zone includes major Russian cities such as Moscow and St. Petersburg.
The table shows 59 samples with Russian language settings, 27 US English, 16 language neutral and 1 UK English.
The samples with Russian language settings were compiled between late 2007 and late 2013, as depicted in Figure 9. This consistency over a long timeframe suggests that the developers of APT28 malware were using a build environment with Russian language settings at least some of the time and made no effort to obscure this detail. Overall, the locale IDs suggest that APT28 developers can operate in both Russian and English.
Other researchers have come to similar conclusions based on their own analysis. The consensus view is that the malware employed by Fancy Bear is Russian in origin. This doesn't in of itself prove that Fancy Bear is a Russian outfit but it's a significant piece of the puzzle. Another piece that is covered in the same report is the group's choice in targets. I debated where to put this next bit but I think it fits well here.
German Spy Service Says Russia Behind Major Cyber Attacks
The operations cited by the BfV intelligence agency ranged from an aggressive attack called Sofacy or APT 28 that hit NATO members and knocked French TV station TV5Monde off air, to a hacking campaign called Sandstorm that brought down part of Ukraine's power grid last year.
"Cyberspace is a place for hybrid warfare. It opens a new space of operations for espionage and sabotage," said Hans-Georg Maassen, who heads the BfV agency.
"The campaigns being monitored by the BfV are generally about obtaining information, that is spying," he said. "However, Russian secret services have also shown a readiness to carry out sabotage."
Germany itself fell victim to one of these rogue operations, with the Sofacy attack last year hitting the German lower house of parliament.
Chancellor Angela Merkel's CDU party confirmed it had been targeted in April, adding that "we have adapted our IT infrastructure as a result".
The BfV said the "cyber attacks carried out by Russian secret services are part of multi-year international operations that are aimed at obtaining strategic information."
"Some of these operations can be traced back as far as seven to 11 years."
BfV is Bundesamt für Verfassungsschutz, the German domestic intelligence agency btw. As it turns out, beyond the identification by multiple independent cyber security firms/experts of Fancy Bear as the responsible party in both instances, there is forensic evidence linking the Bundestag hack to the DNC hack.
Digital Attack on German Parliament: Investigative Report on the Hack of the Left Party Infrastructure in Bundestag
After initialization, the artifact will attempt to establish a connection by creating a socket. In case of failure, it will sleep for three seconds and try again. The authors of the malware didn’t appear to have spent any effort in concealing indicators or obfuscating code – the IP address with which it tries to communicate is hardcoded in clear-text inside the binary. We can observe below, the procedure through which the artifact attempts to establish a connection with the IP address „176.31.112.10“:
Noted security researcher Thomas Rid, professor, Department of War Studies at King’s College London, discovered that a hardcoded IP address for a C2 node from the binaries recovered from the DNC systems (not one of the few included in the IOC table in the CrowdStrike post) was also hardcoded in the samples retreived in the Bundestag hack — 176.31.112[.]10.
Rid also discovered that the same SSL certificate used for encrypting communications with the C2 node in the Bundestag hack was also used for 23.227.196[.]217, the X-Tunnel C2 IP that was previously used for the MIS Department spearphishing site.
edit on 2016-12-14 by theantediluvian because: (no reason given)
I'd intended to list some additional targets at this point but I'm now on my fifth post and it's 2:40 AM EST. I'll likely update this thread with some
additional information/commentary about the targeting. In the meantime, the FireEye report is an excellent start.
Um, didn't Guccifer2.0 do the DNC hack leak?
In any event, how much did this event impact the election? Scale of 1-10?
As I've been arguing, that Russia would hate Hillary for doing the following to their ally is no shocker:
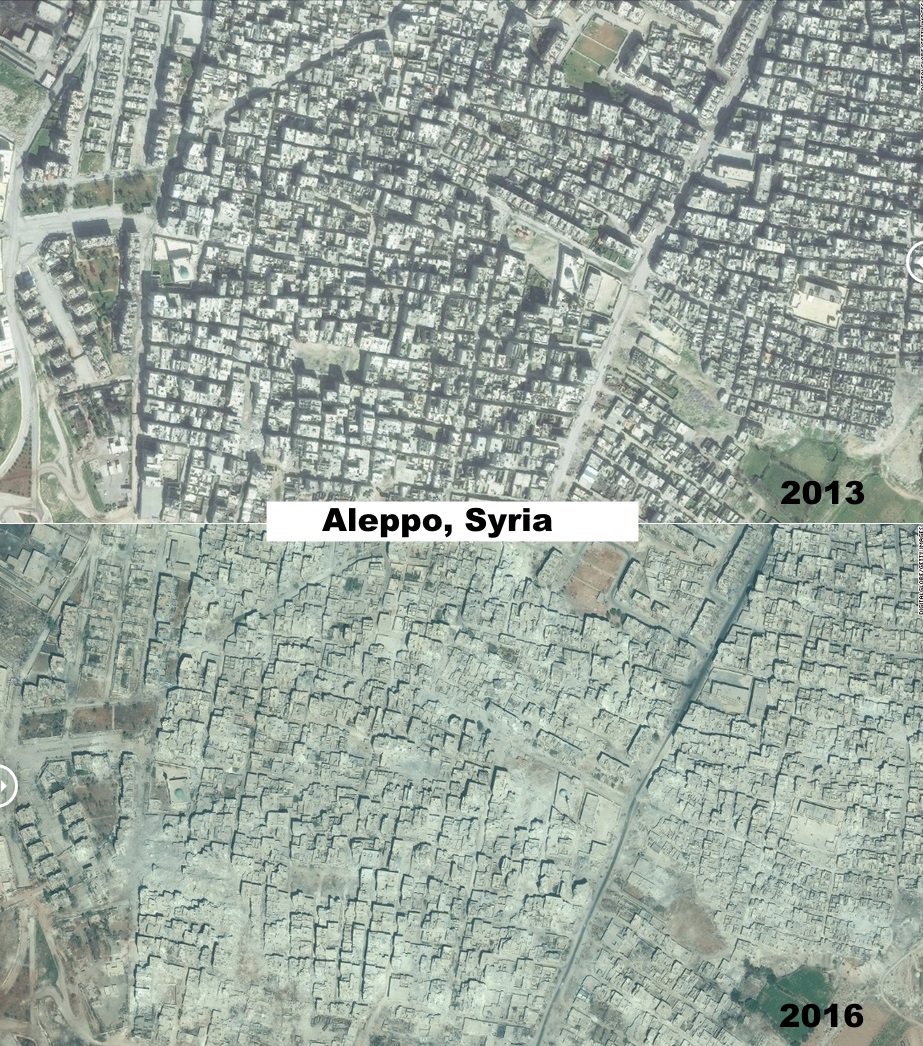
Photos of Syria BEFORE & AFTER Obama & Hillary sent in Al Qaeda (via the CIA)

It's just this liberal narrative I keep seeing that 'they did it because Trump is their whipping boy' is total BS.
Considering the millions of lives she destroyed, if absolutely true the Russia did it thing, and they actually did impact the election, who could argue it wasn't for the best?
In any event, how much did this event impact the election? Scale of 1-10?
As I've been arguing, that Russia would hate Hillary for doing the following to their ally is no shocker:
Photos of Syria BEFORE & AFTER Obama & Hillary sent in Al Qaeda (via the CIA)


It's just this liberal narrative I keep seeing that 'they did it because Trump is their whipping boy' is total BS.
Considering the millions of lives she destroyed, if absolutely true the Russia did it thing, and they actually did impact the election, who could argue it wasn't for the best?
edit on 14-12-2016 by IgnoranceIsntBlisss because: (no reason given)
Oh, wow! I better check my list of crap no one cares about to see if there's enough room for this thread.
First if you know anything about anonymity you would also know I could sit behind a socks5 proxy out of Russia all day and you'd have no idea if I was Russian or American. That doesnt mean I am Russian.
Second, every government hacks every government -- some more successfully than others. Had HRC won the election I assure you this wouldn't be "news" even if they did hack the DNC. The question is not really whether Russians hacked the DNC because they probably did hack the DNC among many other acronyms. The question is whether or not they are responsible for the leaks.
Ill give you an A for effort due to the amount of content you provided, but you have not convinced me that Russians leaked hacked DNC emails to WikiLeaks in order to subvert US Democracy.
First if you know anything about anonymity you would also know I could sit behind a socks5 proxy out of Russia all day and you'd have no idea if I was Russian or American. That doesnt mean I am Russian.
Second, every government hacks every government -- some more successfully than others. Had HRC won the election I assure you this wouldn't be "news" even if they did hack the DNC. The question is not really whether Russians hacked the DNC because they probably did hack the DNC among many other acronyms. The question is whether or not they are responsible for the leaks.
Ill give you an A for effort due to the amount of content you provided, but you have not convinced me that Russians leaked hacked DNC emails to WikiLeaks in order to subvert US Democracy.
a reply to: theantediluvian
It truly is sad to see your threads come to this.
I've always known you have a lean, but your content was always so good and it made me think. You also always provided evidence.
While others would grab straws you would offer threads to make everyone think about the ramifications of the other side of the coin.
And I say this out of kindness, but now you are grabbing straws. While it's funny to see some melt down because they never really knew why they were representing an ideology, I find no solace in seeing you resort to this.
It truly is sad to see your threads come to this.
I've always known you have a lean, but your content was always so good and it made me think. You also always provided evidence.
While others would grab straws you would offer threads to make everyone think about the ramifications of the other side of the coin.
And I say this out of kindness, but now you are grabbing straws. While it's funny to see some melt down because they never really knew why they were representing an ideology, I find no solace in seeing you resort to this.
edit on 14-12-2016 by CriticalStinker because: (no reason
given)
a reply to: drewlander
Hilary lost because of her and and her parties actions, Russia didn't hold a gun to the people and tell them to vote for the DON, the people chose the DON because they didn't want cousin IT as president.
Your always looking for an excuse! Just face it you lost.

Hilary lost because of her and and her parties actions, Russia didn't hold a gun to the people and tell them to vote for the DON, the people chose the DON because they didn't want cousin IT as president.
Your always looking for an excuse! Just face it you lost.

edit on 14-12-2016 by muSSang because:
Spelling
This is what is known as reaching way out there!Anything to justify the loss of a very unpopular candidate,right?
How bloody stupid would a hacker have to be not to mask their location?
So these Russian hackers can break into the DNC but lack the knowledge to perform a simple action that any 14 year old script kiddie knows? Seems unlikely to me.
Meanwhile Israel and China are proven to hack into the US Department of Defence on an almost daily basis and no one says a word about that.
So these Russian hackers can break into the DNC but lack the knowledge to perform a simple action that any 14 year old script kiddie knows? Seems unlikely to me.
Meanwhile Israel and China are proven to hack into the US Department of Defence on an almost daily basis and no one says a word about that.
edit on -060002am12kam by Ohanka because: (no reason given)
If the Russian Hackers had so much ability, why target Podesta and not Clinton?
Why didn't they hit Clinton's (illegal) private server before she ignored the subpoena and wiped them?
Why couldn't Chinese hackers disguise them self as Fancy Bear?
Better yet, why couldn't the CIA disguise themselves and go in?
after all, you yourself said:
yet the oversee'er of the intelligence community said
also, your ''evidence'' shouldn't include CNN interviewing some random saying ''we have evidence Russian Intelligence were hacking....'' .... this sounds like another WMD/IRAQ scam...
'' we have evidence, we cant show you but we have it ''
Let say, for sh*ts and giggles sake that Russia hacked the DNC server and leaked the emails..
For me, I am perfectly ok with that... why? because Russia didn't leak sensitive secrets, they didn't leak nuclear details or threat vulnerability aspects.. they leaked the truth that the Clinton team tried to keep hidden from the public.
If Clinton had of been honest (like she claimed) the hacking and releasing wouldn't have mattered.
2nd, Clinton wanted to confront Russia, drag out ISIS in Syria and move into Iran with all means available.
Trump wanted to TALK to Russia, destroy ISIS and end the Syrian war
If Russia hacking the DNC, leaking the TRUTH to the people allowed a man wanting PEACE to become president over a women wanting war.. then i say BRAVO RUSSIA!

Why didn't they hit Clinton's (illegal) private server before she ignored the subpoena and wiped them?
Why couldn't Chinese hackers disguise them self as Fancy Bear?
Better yet, why couldn't the CIA disguise themselves and go in?
after all, you yourself said:
While we wait to see if information from the CIA assessment will be released or better
yet the oversee'er of the intelligence community said
The position of the ODNI, which oversees the 17 agency-strong U.S. intelligence community, could give Trump fresh ammunition to dispute the CIA assessment, which he rejected as "ridiculous" in weekend remarks, and press his assertion that no evidence implicates Russia in the cyber attacks.
also, your ''evidence'' shouldn't include CNN interviewing some random saying ''we have evidence Russian Intelligence were hacking....'' .... this sounds like another WMD/IRAQ scam...
'' we have evidence, we cant show you but we have it ''

Let say, for sh*ts and giggles sake that Russia hacked the DNC server and leaked the emails..
For me, I am perfectly ok with that... why? because Russia didn't leak sensitive secrets, they didn't leak nuclear details or threat vulnerability aspects.. they leaked the truth that the Clinton team tried to keep hidden from the public.
If Clinton had of been honest (like she claimed) the hacking and releasing wouldn't have mattered.
2nd, Clinton wanted to confront Russia, drag out ISIS in Syria and move into Iran with all means available.
Trump wanted to TALK to Russia, destroy ISIS and end the Syrian war
If Russia hacking the DNC, leaking the TRUTH to the people allowed a man wanting PEACE to become president over a women wanting war.. then i say BRAVO RUSSIA!

originally posted by: muSSang
a reply to: drewlander
Hilary lost because of her and and her parties actions, Russia didn't hold a gun to the people and tell them to vote for the DON, the people chose the DON because they didst want cousin IT as president.
Your always looking for an excuse! Just face it you lost.
I dunno,had a Zil limousine with a driver with a horrible accent take me to the polls!
a reply to: IgnoranceIsntBlisss
Lmao. Promoting your picture thread in the first response to mine? With big ass pictures? Yikes. There are less obnoxious ways to derail a thread.
According to the Guccifer 2.0 persona, which was created the day after Dmitri Alperovitch's initial post, "he's" also the WikiLeaks source.
If you read my initial thread, there's a section on Guccifer 2.0. I haven't gotten to it here. I may not get around to it again at all. I really wanted to focus on some of the nitty gritty of the evidence that you yourself have repeatedly claimed doesn't exist.
Do you just want me to make something up? I have no idea. The election is over. I'm more concerned with how our next President is handling the matter at this point.
That's not really relevant to the topic of the thread is it? FTR, posting a bunch of pictures doesn't prove your claim. Anything else you'd like to throw at the wall?
Lmao. Promoting your picture thread in the first response to mine? With big ass pictures? Yikes. There are less obnoxious ways to derail a thread.
Um, didn't Guccifer2.0 do the DNC hack?
According to the Guccifer 2.0 persona, which was created the day after Dmitri Alperovitch's initial post, "he's" also the WikiLeaks source.
If you read my initial thread, there's a section on Guccifer 2.0. I haven't gotten to it here. I may not get around to it again at all. I really wanted to focus on some of the nitty gritty of the evidence that you yourself have repeatedly claimed doesn't exist.
In any event, how much did this event impact the election? Scale of 1-10.
Do you just want me to make something up? I have no idea. The election is over. I'm more concerned with how our next President is handling the matter at this point.
Considering the millions of lives she destroyed, if absolutely true the Russia did it thing, who could argue it wasn't for the best?
That's not really relevant to the topic of the thread is it? FTR, posting a bunch of pictures doesn't prove your claim. Anything else you'd like to throw at the wall?
Look how much the Guccifer2.0 leak impacted the polls:
July 22 WikiLeaks did the DNC leak:
glomardisclosure.com...
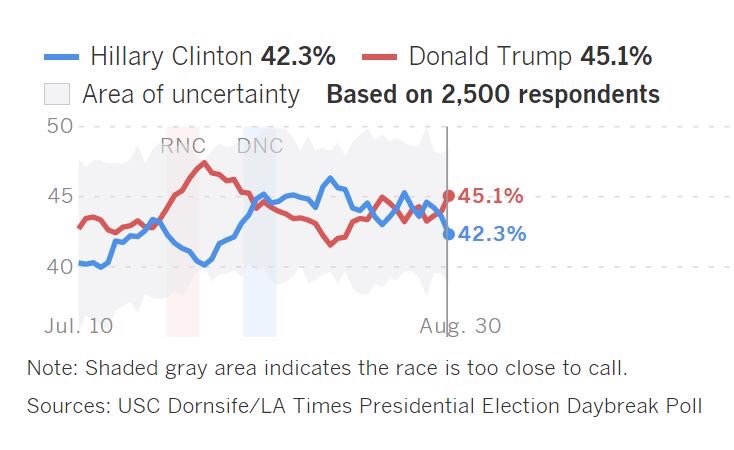
It didn't!
July 22 WikiLeaks did the DNC leak:
glomardisclosure.com...

It didn't!
originally posted by: muSSang
a reply to: drewlander
Hilary lost because of her and and her parties actions, Russia didn't hold a gun to the people and tell them to vote for the DON, the people chose the DON because they didn't want cousin IT as president.
I agree with you entirely. There was very little in the emails that would influence most rational people in deciding who to elect for president. Of more concern to rational people is the home-brew email server run by that dum-dum stonetear or whatever his lame handle was.
That Cage gif is killing me! You could at least use a gif from a good movie he did like "Raising Arizona"
edit on 14-12-2016 by drewlander because: (no reason given)
Providing evidence won't do anything. The technical data will be too complicated and boring for people to understand anyway, so they'll just ridicule
it and brush it off or just find ways to be apologetic about the hacks. People don't understand the danger of such precedent, since it doesn't affect
their supported candidate(s) right at this moment. But it easily could, next time, especially when there are reports of RNC being hacked too.
Blind fanaticism is alive on both sides, sadly. And each of the sides can't see the ignorance of each other, and the dangers it causes. Hypocrisy is a new virtue, it seems.
Blind fanaticism is alive on both sides, sadly. And each of the sides can't see the ignorance of each other, and the dangers it causes. Hypocrisy is a new virtue, it seems.
a reply to: CriticalStinker
What straws am I grabbing at exactly? I'm getting the impression that none of you actually read anything. Maybe the first few sentences?
I did not make any claims about how the hacks affected the outcome of the election. Forgive my bluntness but the lot of you are projecting your hysteria on me.
I came to terms with the fact that Donald Trump would be inaugurated in January way back on November 9th at 3 AM. A number of you on the other hand are so desperate to not discuss the hacks because you have an irrational fear that facing objective reality might somehow result in Hillary Clinton becoming the President.
It won't. Stop being such a reactionary. Maybe you'll be comfortable discussing this once Dear Leader is sworn in?
What straws am I grabbing at exactly? I'm getting the impression that none of you actually read anything. Maybe the first few sentences?
I did not make any claims about how the hacks affected the outcome of the election. Forgive my bluntness but the lot of you are projecting your hysteria on me.
I came to terms with the fact that Donald Trump would be inaugurated in January way back on November 9th at 3 AM. A number of you on the other hand are so desperate to not discuss the hacks because you have an irrational fear that facing objective reality might somehow result in Hillary Clinton becoming the President.
It won't. Stop being such a reactionary. Maybe you'll be comfortable discussing this once Dear Leader is sworn in?
new topics
-
This should be plastered all over the airwaves
Mainstream News: 1 hours ago -
Oh, Good Gosh. “Kremlin Warns Stay Away from Greenland.”
World War Three: 3 hours ago -
Archbisop Vigano Warns of Deep State and Deep Church
New World Order: 4 hours ago -
A Flash of Beauty: Bigfoot Revealed ( documentary )
Cryptozoology: 9 hours ago
top topics
-
Fire insurance in LA withdrawn months ago
General Conspiracies: 12 hours ago, 8 flags -
This should be plastered all over the airwaves
Mainstream News: 1 hours ago, 8 flags -
A Flash of Beauty: Bigfoot Revealed ( documentary )
Cryptozoology: 9 hours ago, 7 flags -
Oh, Good Gosh. “Kremlin Warns Stay Away from Greenland.”
World War Three: 3 hours ago, 7 flags -
Archbisop Vigano Warns of Deep State and Deep Church
New World Order: 4 hours ago, 5 flags
active topics
-
Trump says ownership of Greenland 'is an absolute necessity'
Other Current Events • 122 • : Flyingclaydisk -
The elephant in the room (wearing a hoodie)
US Political Madness • 32 • : xuenchen -
Judge rules president-elect Donald Trump must be sentenced in 'hush money' trial
US Political Madness • 89 • : xuenchen -
This should be plastered all over the airwaves
Mainstream News • 10 • : BeyondKnowledge3 -
Los Angeles brush fires latest: 2 blazes threaten structures, prompt evacuations
Mainstream News • 303 • : xuenchen -
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 8012 • : underpass61 -
The Acronym Game .. Pt.4
General Chit Chat • 1040 • : bally001 -
To become president, Zelensky had to learn Ukrainian
Political Conspiracies • 35 • : Oldcarpy2 -
Oh, Good Gosh. “Kremlin Warns Stay Away from Greenland.”
World War Three • 10 • : Imhere -
Fire insurance in LA withdrawn months ago
General Conspiracies • 26 • : sapien1982

