It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
The National Security Agency has implanted software in about 100,000 computers around the world, allowing the United States to surveil those machines while creating a trail that can be used to launch cyber-attacks.
Though most of the software is installed by gaining access to computer networks, the NSA can also employ technology that enters computers and alters data without needing internet access.
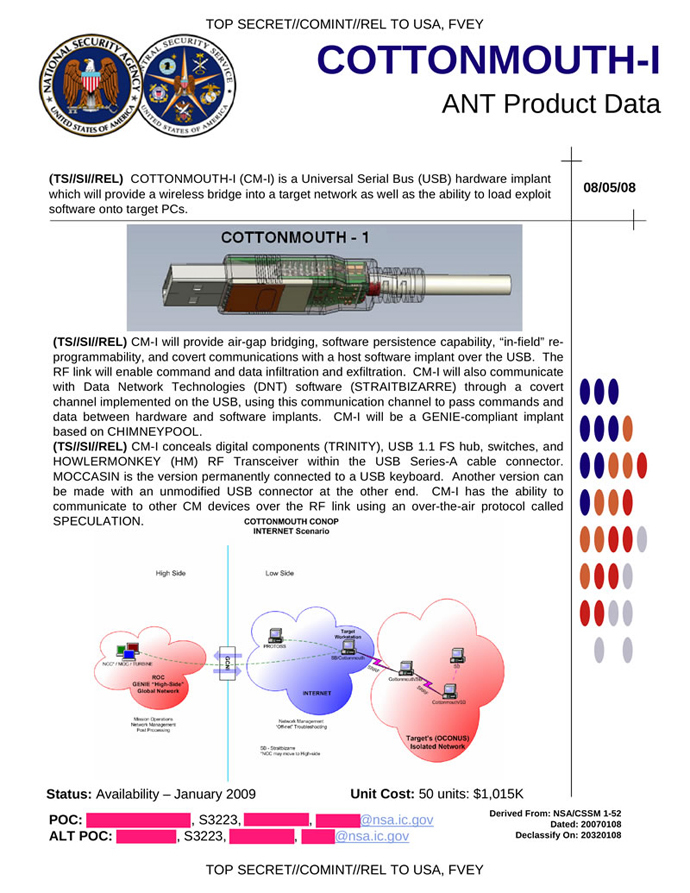
The secret technology uses covert radio waves transmitted from small circuit boards and USB cards clandestinely inserted into targeted computers, The New York Times reported. The waves can then be sent to a briefcase-sized relay station intelligence agencies can set up just miles away, according to NSA documents.
NSA able to target offline computers using radio-waves for surveillance, cyber-attacks
mods delete if already posted please
-----------
nytimes story
The technology, which the agency has used since at least 2008, relies on a covert channel of radio waves that can be transmitted from tiny circuit boards and USB cards inserted surreptitiously into the computers. In some cases, they are sent to a briefcase-size relay station that intelligence agencies can set up miles away from the target.
The radio frequency technology has helped solve one of the biggest problems facing American intelligence agencies for years: getting into computers that adversaries, and some American partners, have tried to make impervious to spying or cyberattack. In most cases, the radio frequency hardware must be physically inserted by a spy, a manufacturer or an unwitting user.
basically if you got a usb cable you may have a transmitter for the NSA
edit on 15-1-2014 by Indigent because: (no reason given)
Officials told The Times most of the implants, by far, were for surveillance and to serve as early warning for a cyber-attack aimed at the US. One official likened them to buoys used to track submarines.
The US has targeted a Chinese Army unit thought to be responsible for most of the bigger cyber-attacks wielded against the US. Documents from Snowden’s trove show the US has two data centers in China from which it can insert malware into computers.
The US maintains Quantum is not used for economic purposes, as it has complained that Chinese attacks have done.
edit on 15-1-2014 by
Indigent because: (no reason given)
reply to post by Indigent
I wonder how long it will be before people start flooding NSA with law suits.
I wonder how long it will be before people start flooding NSA with law suits.
AthlonSavage
reply to post by Indigent
I wonder how long it will be before people start flooding NSA with law suits.
They will say its not in use in USA, its only for enemy countries, they always says the same
So, uh...yeah....
Meet BadBIOS
This was originally scoffed. And has since been heavily scorned.
However, frankly, now it doesn't seem quite so unfeasible. Hell, even the way it is suggested in the article I proposed here sounds ENTIRELY plausible, if not probable.
NSA...are you listening ?
Meet BadBIOS
This was originally scoffed. And has since been heavily scorned.
However, frankly, now it doesn't seem quite so unfeasible. Hell, even the way it is suggested in the article I proposed here sounds ENTIRELY plausible, if not probable.
NSA...are you listening ?
reply to post by zeroBelief
Its in use since 2008, if you are on the internet they are listening, this new stuff is for isolated terminals not connected to internet.
NSA...are you listening ?
Its in use since 2008, if you are on the internet they are listening, this new stuff is for isolated terminals not connected to internet.
reply to post by Indigent
Two years ago a friend of mine called me paranoid because I have a triple head setup, I run linux and I have a kde widget embeded in the background of one of my monitors that's constantly monitoring Snort IDS, all incoming/outgoing connections + ports and usblockdown with a strick set of rules that only accept input data from the vendors of the USB devices I own and pops me alert on the widget of anything fishy on my network or if something comes from a USB stick.
NOW WHO'S LAUGHING!!!
Two years ago a friend of mine called me paranoid because I have a triple head setup, I run linux and I have a kde widget embeded in the background of one of my monitors that's constantly monitoring Snort IDS, all incoming/outgoing connections + ports and usblockdown with a strick set of rules that only accept input data from the vendors of the USB devices I own and pops me alert on the widget of anything fishy on my network or if something comes from a USB stick.
NOW WHO'S LAUGHING!!!
Indigent
reply to post by zeroBelief
NSA...are you listening ?
Its in use since 2008, if you are on the internet they are listening, this new stuff is for isolated terminals not connected to internet.
Let me expound, this is a *related* kind of hack....not the same...but as soon as I read the OP article, it immediately reminded me of BadBIOS...which I read about two months or so ago....
Feel free to read the article. IT IS about listening. And not while connected to the Internet. And in a slightly different way.
edit
on 15-1-2014 by zeroBelief because: Just to illuminat....
Have they caught the Target Hackers yet? They had to have some computer device to pull that off.
If not, then, I guess it doesn't work.
If not, then, I guess it doesn't work.
edit on 15-1-2014 by Diabolical because: (no reason given)
_R4t_
reply to post by Indigent
Two years ago a friend of mine called me paranoid because I have a triple head setup, I run linux and I have a kde widget embeded in the background of one of my monitors that's constantly monitoring Snort IDS, all incoming/outgoing connections + ports and usblockdown with a strick set of rules that only accept input data from the vendors of the USB devices I own and pops me alert on the widget of anything fishy on my network or if something comes from a USB stick.
NOW WHO'S LAUGHING!!!
no one because it was true? it is a sad news
edit on 15-1-2014 by Indigent because: ''is'' was missing
If I'm reading the "Cottonmouth" chart correctly 50 units=$1015K or a bit over $20,000 each.
A couple of years ago I remember thinking how ridiculous the government contractor was for smashing up monitors , cables and disks after being virus infected. Guess he knew a bit more the extent of the problem at the time than I thought!
ganjoa
A couple of years ago I remember thinking how ridiculous the government contractor was for smashing up monitors , cables and disks after being virus infected. Guess he knew a bit more the extent of the problem at the time than I thought!
ganjoa
I prefer "tempest", why hack a users computer when you can just look over they're shoulder from a fai distance away and WATCH everyting they are
doing with the machine. When they shut if off and leave it unattended, you have a recording of everything they did, and you can just log right in, to
that users computer, and it will LOOK like the actual user is sitting right there! and so much less tedious than hacking or stealing, and when you do
it right? nobody will ever know! it's like the perfect crime, you know, tearing that "do not remove" lable from that new mattress you bought, or
making hillary the SECSTATE!, truly hideous crimes I know !
Indigent
_R4t_
reply to post by Indigent
Two years ago a friend of mine called me paranoid because I have a triple head setup, I run linux and I have a kde widget embeded in the background of one of my monitors that's constantly monitoring Snort IDS, all incoming/outgoing connections + ports and usblockdown with a strick set of rules that only accept input data from the vendors of the USB devices I own and pops me alert on the widget of anything fishy on my network or if something comes from a USB stick.
NOW WHO'S LAUGHING!!!
no one because it was true? it is a sad newsedit on 15-1-2014 by Indigent because: ''is'' was missing
If you take in account it takes a single click to a link thats hooked with codes you'll never see that is getting run transparently to the page your going to see if you will, which can then forward you to a server that'll automatically detect which version of browser your using, the operating system its on, guess the version and launch an automated custom attack using those parameters to then exploit a hole in the browser so a payload can be uploaded... Than a post-exploitation script can automatically be fired to kill all traces and erase logs all within minutes. From there all the websites you've been, passwords to all your bank accounts, any credit card number you type on will be caught and sent back to the attacker.
And thats not the NSA champ...
And thats only moderately sophesticated in terms of attack... Thats the stuff most kids with mid grade computer knowledge can find how to do on youtube. You don't want to hear about the more high end stuff trust me... For 20$ at radio shack I can McGiver you a device that plugs into a power socket and stiff ever single damn keystroke of an entire building by pluging it into 1 power socket... As long as they have PS2 keyboards and those are still commonly used.
There's a huge difference between paranoiya and awareness...
Those codes get injected in publicity ads you see often pretty much everywhere because said companies doesn't verify the codes in the adds they just bother with taking payment and displaying it...
Thats how the Zeus banking trojan worked and which helped them steal over 70millions from poor folks that would say the same thing you just did, hell you might even be one of them and you'll only find out in a couple of years...
At this very moment your name, address and enough info is probably in the hands of someone thats just waiting a year or two to order some credit cards in your name. The trick is they catch the info and wait as long as possible before using it, it makes it almost impossible to trace back to how they got it in first place...
I personally know someone that went to BC once in her life about 5 years ago and used a credit card which was used last year again in BC... they waited 4 years to use the stolen info...
I work in the field of security and with the stuff that I know it would make you paranoid to the point where you wouldn't even leave your bedroom... A guy that owns a pizza shop I know told me about 3 months ago he had installed security cam in his house that he could access anytime with his phone. I told him to get reg cameras that just record to a DVR type of device cuz those could be hacked within minutes, he wouldn't believe me... took me about 5 minutes because the particular make and model have an embeded backdoor. 90% of them either have no default admin user/pass, either they have some but they are admin/pass or admin/default or admin/admin and in the best case scenario a backdoor thats not logged like the model he had...
He turned green and purple when I shown him I could watch him in his house anytime I wanted or anyone else on the internet that knew how and could just scan his address and his the camera firmware page would be able to do the same... Hell he prolly was or would of ended up listed on shodanhq...
edit on 15-1-2014 by _R4t_ because: (no reason given)
tencap77
I prefer "tempest", why hack a users computer when you can just look over they're shoulder from a fai distance away and WATCH everyting they are doing with the machine.
Works with unshielded CRTs. Not so much with LCDs. Sad to say.
When they shut if off and leave it unattended, you have a recording of everything they did, and you can just log right in, to that users computer, and it will LOOK like the actual user is sitting right there!
Not at all. It's a method for getting data from noise leaks, but you absolutely can't "log right in, to that user's computer".
_R4t_
Indigent
_R4t_
reply to post by Indigent
Two years ago a friend of mine called me paranoid because I have a triple head setup, I run linux and I have a kde widget embeded in the background of one of my monitors that's constantly monitoring Snort IDS, all incoming/outgoing connections + ports and usblockdown with a strick set of rules that only accept input data from the vendors of the USB devices I own and pops me alert on the widget of anything fishy on my network or if something comes from a USB stick.
NOW WHO'S LAUGHING!!!
no one because it was true? it is a sad newsedit on 15-1-2014 by Indigent because: ''is'' was missing
If you take in account it takes a single click to a link thats hooked with codes you'll never see that transparently to the page your going to see if you will, which can then forward you to a server that'll automatically detect which version of browser your using, the operating system its on, guess the version and launch an automated customer attack using those parameters to then exploit a hole in the browser so a payload can be uploaded... Than a post-exploitation script can automatically be fired to kill all traces and erase logs all within minutes. From there all the websites you've been, passwords to all your bank accounts, any credit card number you type on will be caught and sent back to the attacker.
And thats not the NSA champ...
And thats only moderately sophesticated in terms of attack... Thats the stuff most kids with mid grade computer knowledge can find how to do on youtube. You don't want to hear about the more high end stuff trust me... For 20$ at radio shack I can McGiver you a device that plugs into a power socket and stiff ever single damn keystroke of an entire building by pluging it into 1 power socket... As long as they have PS2 keyboards and those are still commonly used.
There's a huge difference between paranoiya and awareness...
Ummm, I kinda sorta think you're preaching to the choir here......
Bedlam
tencap77
I prefer "tempest", why hack a users computer when you can just look over they're shoulder from a fai distance away and WATCH everyting they are doing with the machine.
Works with unshielded CRTs. Not so much with LCDs. Sad to say.
When they shut if off and leave it unattended, you have a recording of everything they did, and you can just log right in, to that users computer, and it will LOOK like the actual user is sitting right there!
Not at all. It's a method for getting data from noise leaks, but you absolutely can't "log right in, to that user's computer".
Bedlam is right on this again, TEMPEST is derived from the work of guy named Van Eck which released a paper back in the 80's if I recall properly called Van Eck Phreaking with explanations and a proof of concept on how CRT monitors are leaking EMF that can be process and reconstructed several meters away... Althought it was very rudimentary and not that great image quality wise you could still distinguish enough to be a security threat but that was back in the mid 80's I wonder what the NSA cooked with the budget they have...
reply to post by _R4t_
It's a tough go with flat panels. When CRTs were king, there were two or three ways to skin that cat. Not only could you catch emissions off the electron beam, if you had a clear view into an office where a guy was working on a CRT, you could look at the light from the screen bouncing off a light colored surface and reconstruct the image from that.
LCDs have long decay times and they're written in several chunks simultaneously. At the same time, they've gotten a lot better at shielding leaks.
It's a tough go with flat panels. When CRTs were king, there were two or three ways to skin that cat. Not only could you catch emissions off the electron beam, if you had a clear view into an office where a guy was working on a CRT, you could look at the light from the screen bouncing off a light colored surface and reconstruct the image from that.
LCDs have long decay times and they're written in several chunks simultaneously. At the same time, they've gotten a lot better at shielding leaks.
reply to post by Bedlam
Yup I know, its amazing sometimes what can be caught through thinking out of the box in the form of side-channel attacks. And thats what scares me the most about the NSA they most relie on side-channels instead of trying to directly break inside your machine straight from the net.
There's very interesting conference about the NSA type of attacks and the other tools they have by a guy called Jacob Applebaum did its called "To Protect and Infect" its free on youtube, you guys might want to watch it. Its amazing how they even use race conditions by using random people's modems/routers as means to carry on certain attack to redirect web traffic so they end up as Man In The Middle and/or worst...
Just a good example of how powerful thinking out of the box can be under the right circumstance... No one would of ever though you could literally sniff high standard encryption keys just by pointing microphones at a PC's power supply... yet its been done...
www.cs.tau.ac.il...
Yup I know, its amazing sometimes what can be caught through thinking out of the box in the form of side-channel attacks. And thats what scares me the most about the NSA they most relie on side-channels instead of trying to directly break inside your machine straight from the net.
There's very interesting conference about the NSA type of attacks and the other tools they have by a guy called Jacob Applebaum did its called "To Protect and Infect" its free on youtube, you guys might want to watch it. Its amazing how they even use race conditions by using random people's modems/routers as means to carry on certain attack to redirect web traffic so they end up as Man In The Middle and/or worst...
Just a good example of how powerful thinking out of the box can be under the right circumstance... No one would of ever though you could literally sniff high standard encryption keys just by pointing microphones at a PC's power supply... yet its been done...
www.cs.tau.ac.il...
edit on 15-1-2014 by _R4t_ because: (no reason given)
reply to post by _R4t_
I've seen them pick off encrypted voice comms not by decrypting the traffic but by looking at nearly unmeasurable amplitude and frequency variations caused by the voice amplifiers drawing more or less current and causing the power supply voltages to vary.
I've seen them pick off encrypted voice comms not by decrypting the traffic but by looking at nearly unmeasurable amplitude and frequency variations caused by the voice amplifiers drawing more or less current and causing the power supply voltages to vary.
_R4t_
Just a good example of how powerful thinking out of the box can be under the right circumstance... No one would of ever though you could literally sniff high standard encryption keys just by pointing microphones at a PC's power supply... yet its been done...
You can get around that by randomly modulating the CPU's power draw, some "high security" micros do this as an option, if the CPU can't assist you can cause something pretty confusing by randomly clock skipping or by adding in a big FET and randomly chucking loads on the CPU power.
It's a pretty standard technique in high security comm gear too, random power supply loads are a "must have".
Bedlam
reply to post by _R4t_
I've seen them pick off encrypted voice comms not by decrypting the traffic but by looking at nearly unmeasurable amplitude and frequency variations caused by the voice amplifiers drawing more or less current and causing the power supply voltages to vary.
Hah!... you really had to think about it but I guess its true, beauty does lie in simplicity... I'm impressed though buddy most people I talk to about this stuff either knows nothing about it or have very narrow knowledge about the mechanics of it... You have a vast amout of knowledge too I can deff see that, my hats off to you man...
new topics
-
Cold Blooded Killers on Christmas!! GRRRRrrr!!
Pets: 25 minutes ago -
Plane Crash Today --Azerbaijanian E190 passenger jet
Mainstream News: 4 hours ago -
Orange County Makes Shoplifting a Felony
Other Current Events: 9 hours ago -
It's Offical Now
US Political Madness: 11 hours ago
top topics
-
Orange County Makes Shoplifting a Felony
Other Current Events: 9 hours ago, 16 flags -
It's Offical Now
US Political Madness: 11 hours ago, 13 flags -
The reason it works is.....
General Chit Chat: 12 hours ago, 8 flags -
Dick Van Dyke saved from Wildfire by neighbours on his 99th birthday
People: 14 hours ago, 7 flags -
Plane Crash Today --Azerbaijanian E190 passenger jet
Mainstream News: 4 hours ago, 5 flags -
Cold Blooded Killers on Christmas!! GRRRRrrr!!
Pets: 25 minutes ago, 0 flags
active topics
-
Cold Blooded Killers on Christmas!! GRRRRrrr!!
Pets • 1 • : Flyingclaydisk -
London Christmas Market BANS Word ‘Christmas’
Social Issues and Civil Unrest • 46 • : Connector -
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 7956 • : KrustyKrab -
Plane Crash Today --Azerbaijanian E190 passenger jet
Mainstream News • 10 • : yuppa -
Drones everywhere in New Jersey ---and Elsewhere Master Thread
Aliens and UFOs • 229 • : yuppa -
It's Offical Now
US Political Madness • 14 • : BernnieJGato -
DefCon Teetering on Escalation
World War Three • 49 • : ADVISOR -
Orange County Makes Shoplifting a Felony
Other Current Events • 22 • : FeeshJefe -
Political Warfare & The Resister Special Forces Underground
Political Ideology • 1 • : ADVISOR -
The reason it works is.....
General Chit Chat • 4 • : randomuser2034
