It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
0
share:
Is it possible to have a user account that is invisible?
Recently I was checking into a process that I didn't recognize on my computer. An online website was looking for instances of the process and found one in C:UsersXXXX. The problem is I've never heard of XXXX and when I went to the C:Users folder, there was no XXXX subfolder.
Whoops: running Win 7 Home Prem. in Admin account.
All help appreciated, as usual.
Recently I was checking into a process that I didn't recognize on my computer. An online website was looking for instances of the process and found one in C:UsersXXXX. The problem is I've never heard of XXXX and when I went to the C:Users folder, there was no XXXX subfolder.
Whoops: running Win 7 Home Prem. in Admin account.
All help appreciated, as usual.
edit on 18-8-2013 by ipsedixit because: (no reason given)
reply to post by ipsedixit
Some users don't always show up in the User Accounts area so you'll need to go to Computer Manager -> Local Users and Groups to see "all" accounts. Let me me know if you need more details.
Also, many applications run as a "service" which some times run with a built-in account like Local System or Network Service.
Some users don't always show up in the User Accounts area so you'll need to go to Computer Manager -> Local Users and Groups to see "all" accounts. Let me me know if you need more details.
Also, many applications run as a "service" which some times run with a built-in account like Local System or Network Service.
edit on 18-8-2013
by usertwelve because: (no reason given)
Originally posted by usertwelve
reply to post by ipsedixit
Some users don't always show up in the User Accounts area so you'll need to go to Computer Manager -> Local Users and Groups to see "all" accounts. Let me me know if you need more details.
This screen grab will show that there is no "Local Users and Groups" folder in the Computer Management folder.
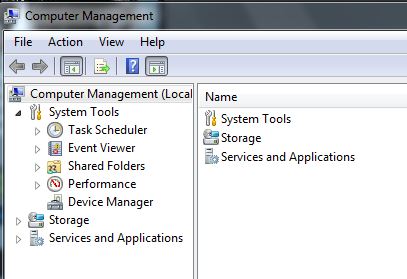
??????? I know there is supposed to be one.
edit on 18-8-2013 by ipsedixit because: (no reason given)
I just found out the "Local Users and Groups" is not available in Windows 7 Home Premium. Maybe I need to upgrade.
reply to post by ipsedixit
Maybe the account you are logged in with does not have the rights to view/make changes to Local Users and Groups
Maybe the account you are logged in with does not have the rights to view/make changes to Local Users and Groups
edit on 18-8-2013 by PhoenixOD because: (no reason given)
Ah sorry i didnt spot you have win7 home premium. It not available in that version or lower in that GUI.
Though it is possible to view it. If you really want to mess around with your system.
Though it is possible to view it. If you really want to mess around with your system.
edit on 18-8-2013 by PhoenixOD because: (no reason given)
Originally posted by PhoenixOD
Though it is possible to view it. If you really want to mess around with your system.
The idea is more along the lines of seeing if that has already been done.
reply to post by ipsedixit
well its not so much view it as use some of the functions with 'net user' through an elevated command prompt.
well its not so much view it as use some of the functions with 'net user' through an elevated command prompt.
edit on 18-8-2013 by PhoenixOD because: (no reason given)
reply to post by ipsedixit
I haven't seen this done in particular, but it's just a set of files on a hard drive. If you know enough about how anything is constructed and have access to the CPU outside of the operating system itself, you can do pretty much anything you desire. On the programming side, you would probably want to write in assembly and use an assembler that does not enforce the operating system memory space and monitoring paradigm. An assembler like this may be hard to find these days, but they are certain to be out there somewhere.
Then, when you are given the CPU (usually requested by an interrupt when I used to write stuff like this), your little program can do literally anything you know how to do, understand the structure and protocols of, and know where the dedicated or shared memory is in terms of absolute addresses (relative addresses might work, in some cases). Once you are outside of the operating system, the entire computer and all connected hardware is yours and nothing but your own ignorance gets in your way. FYI: if you do something "bad" you can really screw things up too.
I used to write a lot of my own drivers for keyboard, video, mouse, and hard drives to enable dynamic debugging of software that was running that I didn't want to disturb because the run times were very, very long (days in some cases). I'd go scan register contents, shared video memory, hard disk buffers, keyboard buffers, printer buffers, etc. Generally peeking to see what was going on (monitoring) but occasionally poking new contents to see how the program reacted. It's basically trivial to do, with the right knowledge and a little experimentation.
So, yeah -- it should be possible. If I were doing something like that, I think I would try looking for a spot on the hard drive to leave a file outside of the file system (essentially lie to the allocation table). Then, when your little program begins running, if you want to expose it to the operating system, you could just correct the allocation table. I'm not sure why you would want to expose a hidden user account though, except perhaps to do something you don't quite understand yet or that takes too long to write in assembly?
I haven't seen this done in particular, but it's just a set of files on a hard drive. If you know enough about how anything is constructed and have access to the CPU outside of the operating system itself, you can do pretty much anything you desire. On the programming side, you would probably want to write in assembly and use an assembler that does not enforce the operating system memory space and monitoring paradigm. An assembler like this may be hard to find these days, but they are certain to be out there somewhere.
Then, when you are given the CPU (usually requested by an interrupt when I used to write stuff like this), your little program can do literally anything you know how to do, understand the structure and protocols of, and know where the dedicated or shared memory is in terms of absolute addresses (relative addresses might work, in some cases). Once you are outside of the operating system, the entire computer and all connected hardware is yours and nothing but your own ignorance gets in your way. FYI: if you do something "bad" you can really screw things up too.
I used to write a lot of my own drivers for keyboard, video, mouse, and hard drives to enable dynamic debugging of software that was running that I didn't want to disturb because the run times were very, very long (days in some cases). I'd go scan register contents, shared video memory, hard disk buffers, keyboard buffers, printer buffers, etc. Generally peeking to see what was going on (monitoring) but occasionally poking new contents to see how the program reacted. It's basically trivial to do, with the right knowledge and a little experimentation.
So, yeah -- it should be possible. If I were doing something like that, I think I would try looking for a spot on the hard drive to leave a file outside of the file system (essentially lie to the allocation table). Then, when your little program begins running, if you want to expose it to the operating system, you could just correct the allocation table. I'm not sure why you would want to expose a hidden user account though, except perhaps to do something you don't quite understand yet or that takes too long to write in assembly?
Originally posted by BayesLike
I'm not sure why you would want to expose a hidden user account though, except perhaps to do something you don't quite understand yet or that takes too long to write in assembly?
Thanks for your post. I do get the jist of it but actually doing anything along the lines you describe is beyond my skill level and time constraints.
I want to delete the hidden user account, if it is there, or at the very least verify that it is there. It turned up in an online scan related to an .exe that I didn't recognize.
Could something like that crop up if a browser extension were installed? For example a user account was created in order to configure the installation and then the user account was deleted at the end of the installation process?
This might be related to my recent installation of the new piratebrowser addons to Internet Explorer.
The other possibility is that your Windows 7 install isn't a fresh install.
If you had a previous version of Windows, or even a previous version of Windows 7, it's quite possible to have user accounts, permissions or settings from the previous install left over.
For example...
if you installed Windows 7 over the top of another pre-existing installation, then ran software that had been installed while USING the previous installation, the username would show up in the task manager as... usually a sequence of numbers. Likewise with permissions and security settings.
Does that sound like the issue you're having?
If you had a previous version of Windows, or even a previous version of Windows 7, it's quite possible to have user accounts, permissions or settings from the previous install left over.
For example...
if you installed Windows 7 over the top of another pre-existing installation, then ran software that had been installed while USING the previous installation, the username would show up in the task manager as... usually a sequence of numbers. Likewise with permissions and security settings.
Does that sound like the issue you're having?
reply to post by Awen24
No. This was the install that was on the computer when I bought it. The account doesn't show up when I go to Users and Groups in the control panel. I wonder if it might be from the install disk the store used to install the software on the computer, that it came with, which is similar to what you are saying.
No. This was the install that was on the computer when I bought it. The account doesn't show up when I go to Users and Groups in the control panel. I wonder if it might be from the install disk the store used to install the software on the computer, that it came with, which is similar to what you are saying.
reply to post by ipsedixit
Could be an account that was used by the manufacturer to setup the PC. Once they have it setup they may have removed the account but the Profile folder remained. I'd just move the folder somewhere else and then delete it completely after a week or so.
Could be an account that was used by the manufacturer to setup the PC. Once they have it setup they may have removed the account but the Profile folder remained. I'd just move the folder somewhere else and then delete it completely after a week or so.
reply to post by usertwelve
The location of the folder is C: (backslash)Users(backslash)XXXX , but the folder is not there. There is no such folder XXXX. It only shows up when an online scan was looking for instances of a certain .exe.
The location of the folder is C: (backslash)Users(backslash)XXXX , but the folder is not there. There is no such folder XXXX. It only shows up when an online scan was looking for instances of a certain .exe.
edit on 19-8-2013 by ipsedixit because: (no reason given)
reply to post by ipsedixit
By "online scan" do you mean a virus scan of your hard drive? If so then it's probably just looking for known locations of existing viruses so if nothing is there then you're clean.
By "online scan" do you mean a virus scan of your hard drive? If so then it's probably just looking for known locations of existing viruses so if nothing is there then you're clean.
reply to post by usertwelve
I went to processchecker.com... to check on something called RaLink.exe. I found out that RaLink is usually called InstallShield. Ok, I've seen the term InstallShield before. It comes up every time you install something. Fine.
But the website said it found one instance of it:
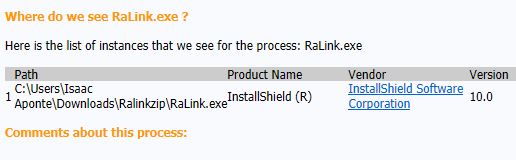
I've never heard of IsaacAponte and there is no folder with his name on it in C: Users.
I went to processchecker.com... to check on something called RaLink.exe. I found out that RaLink is usually called InstallShield. Ok, I've seen the term InstallShield before. It comes up every time you install something. Fine.
But the website said it found one instance of it:

I've never heard of IsaacAponte and there is no folder with his name on it in C: Users.
edit on 19-8-2013 by ipsedixit because: (no reason given)
reply to post by ipsedixit
I see. If I understand it correctly, what they are telling you is that is the location they have a record for that file in their database which was probably found on some guy named "Isaac Aponte's" PC. You might try to do a search for the RaLink.exe file on your file system but I'm guessing there's no need for concern.
I see. If I understand it correctly, what they are telling you is that is the location they have a record for that file in their database which was probably found on some guy named "Isaac Aponte's" PC. You might try to do a search for the RaLink.exe file on your file system but I'm guessing there's no need for concern.
new topics
-
Potter to WHU
World Sports: 4 hours ago -
Dr. Demento
Music: 6 hours ago -
The elephant in the room (wearing a hoodie)
US Political Madness: 6 hours ago
top topics
-
The elephant in the room (wearing a hoodie)
US Political Madness: 6 hours ago, 12 flags -
Green Grapes
General Chit Chat: 17 hours ago, 7 flags -
To become president, Zelensky had to learn Ukrainian
Political Conspiracies: 13 hours ago, 6 flags -
Dr. Demento
Music: 6 hours ago, 5 flags -
Potter to WHU
World Sports: 4 hours ago, 1 flags
active topics
-
The Acronym Game .. Pt.4
General Chit Chat • 1038 • : Moon68 -
The Truth about Migrant Crime in Britain.
Social Issues and Civil Unrest • 41 • : BedevereTheWise -
Los Angeles brush fires latest: 2 blazes threaten structures, prompt evacuations
Mainstream News • 163 • : Flyingclaydisk -
The Fight for Election Integrity Continues -- Audits, Criminal Investigations, Legislative Reform
2024 Elections • 4371 • : WeMustCare -
The elephant in the room (wearing a hoodie)
US Political Madness • 18 • : Irishhaf -
Trump says ownership of Greenland 'is an absolute necessity'
Other Current Events • 76 • : LSU2018 -
Potter to WHU
World Sports • 2 • : Bilbous72 -
Dr. Demento
Music • 12 • : GENERAL EYES -
President Carter has passed
Mainstream News • 45 • : WeMustCare -
To become president, Zelensky had to learn Ukrainian
Political Conspiracies • 30 • : Oldcarpy2
0
