It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
Flame authors order infected computers to remove all traces of the malware
www.cio.com.au
(visit the link for the full news article)
The creators of the Flame cyber-espionage threat ordered infected computers still under their control to download and execute a component designed to remove all traces of the malware and prevent forensic analysis, security researchers from Symantec said on Wednesday.
Flame has a built-in feature called SUICIDE that can be used to uninstall the malware from infected computers. However, late last week, Flame's creators decided to distribute a different self-removal module to infected computers...
So in this very interesting cyber-war scenario, the perpetrators are in the act of covering their tracks.... I wonder why?
A twist worth remembering for those following the developments as the media reports them:
What might a reverse-engineering of the coded 'modules' have revealed? No one says... but I bet it has to do with tracking how the Flame networked and what streams of data went where....
www.cio.com.au
(visit the link for the full news article)
The module is called browse32.ocx and its most recent version was created on May 9, 2012. "It is unknown why the malware authors decided not to use the SUICIDE functionality, and instead make Flamer perform explicit actions based on a new module," the Symantec researchers said.
However, even though it is similar in functionality to the SUICIDE feature -- both being able to delete a large number of files associated with the malware -- the new module goes a step further.
"It locates every [Flame] file on disk, removes it, and subsequently overwrites the disk with random characters to prevent anyone from obtaining information about the infection," the Symantec researchers said. "This component contains a routine to generate random characters to use in the overwriting operation. It tries to leave no traces of the infection behind."
A twist worth remembering for those following the developments as the media reports them:
According to Aleks Gostev, chief security expert with Kaspersky Lab's global research & analysis team, the overwriting of file data with meaningless characters happens before the Flame files get deleted by browse32.ocx, not after as Symantec suggested. However, the goal is the same -- eliminating all traces of the malware and making forensic analysis harder, he said via email.
What might a reverse-engineering of the coded 'modules' have revealed? No one says... but I bet it has to do with tracking how the Flame networked and what streams of data went where....
www.cio.com.au
(visit the link for the full news article)
Interesting information.
What I keep thinking, however, is that Kaspersky Labs has to have something to do with this. They were the first to reveal and analyze Stuxnet and Flame, although there are dozens of top-flight malware analysis firms around the world. People forget that the Russians have perhaps the most robust cyber warfare capabilities of any nation other than the United States, and often times can rival or surpass those of the US.
What I keep thinking, however, is that Kaspersky Labs has to have something to do with this. They were the first to reveal and analyze Stuxnet and Flame, although there are dozens of top-flight malware analysis firms around the world. People forget that the Russians have perhaps the most robust cyber warfare capabilities of any nation other than the United States, and often times can rival or surpass those of the US.
This is uber shady...Its a kind of stealth hit and run.
Someone wants to cover their tracks.
Wasn't the boss or ex boss of Kaspersky just raided for having a meth lab and loads of guns recently?
Is there a connection I wonder-I am not saying he made the virus,but there could be some connection maybe.
Someone wants to cover their tracks.
Wasn't the boss or ex boss of Kaspersky just raided for having a meth lab and loads of guns recently?
Is there a connection I wonder-I am not saying he made the virus,but there could be some connection maybe.
reply to post by Dreine
You know, this is always good to remember - all sources must be considered.
But there is at least a 'possible' reason that we heard from them first (and more fully.... it's just a hypothesis - no allegation intended)...
Kapersky is not tightly affiliated with the 'anti-malware' industry which reside in countries like the US. UK, and Australia... and I wouldn't be exactly surprised that these "western" players are just as likely to be providing 'cover' for any operation in which they had a hand, or had 'guilty knowledge.'
Had Kapersky been even remotely suspected of complicity in the affair, I think many populists would have leaped on the opportunity to cast them in a bad light; them being "Russian" and all.
I often notice how none of these companies are quick to say bad things about the others in their industrial 'clique.'
You know, this is always good to remember - all sources must be considered.
But there is at least a 'possible' reason that we heard from them first (and more fully.... it's just a hypothesis - no allegation intended)...
Kapersky is not tightly affiliated with the 'anti-malware' industry which reside in countries like the US. UK, and Australia... and I wouldn't be exactly surprised that these "western" players are just as likely to be providing 'cover' for any operation in which they had a hand, or had 'guilty knowledge.'
Had Kapersky been even remotely suspected of complicity in the affair, I think many populists would have leaped on the opportunity to cast them in a bad light; them being "Russian" and all.
I often notice how none of these companies are quick to say bad things about the others in their industrial 'clique.'
reply to post by Maxmars
I would be interested to see Mandiant's take on the issue, I hold their opinion in higher regards than I do Symantec... who just happens to be the USG largest anti-hacking software provider. Heck, why hasn't RSA or SANS been able to get ahold of any traces or instances of Flame for that matter as well? Both are giants in the cyber security realm.
State-sponsored? I'd say that is a resounding "HELL YES".
I would be interested to see Mandiant's take on the issue, I hold their opinion in higher regards than I do Symantec... who just happens to be the USG largest anti-hacking software provider. Heck, why hasn't RSA or SANS been able to get ahold of any traces or instances of Flame for that matter as well? Both are giants in the cyber security realm.
State-sponsored? I'd say that is a resounding "HELL YES".
This addition almost merits a thread of its own... but I knew you all might be interested in including the discussion here so, here goes...
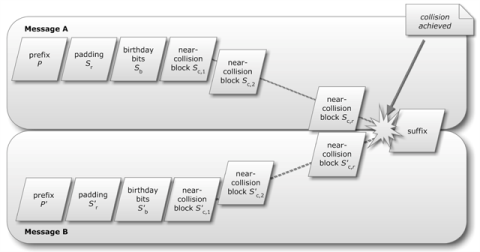
and further on:
Source ARS

Crypto breakthrough shows Flame was designed by world-class scientists
The Flame espionage malware that infected computers in Iran achieved mathematic breakthroughs that could only have been accomplished by world-class cryptographers, two of the world's foremost cryptography experts said.
"We have confirmed that Flame uses a yet unknown MD5 chosen-prefix collision attack," Marc Stevens and B.M.M. de Weger wrote in an e-mail posted to a cryptography discussion group earlier this week. "The collision attack itself is very interesting from a scientific viewpoint, and there are already some practical implications."
and further on:
According to Stevens and de Weger, the collision attack was unlike any that cryptographers have seen before. They arrived at that conclusion after using a custom-designed forensic tool to analyze Flame components.
"More interestingly, the results have shown that not our published chosen-prefix collision attack was used, but an entirely new and unknown variant," Stevens wrote in a statement distributed on Thursday. "This has led to our conclusion that the design of Flame is partly based on world-class cryptanalysis. Further research will be conducted to reconstruct the entire chosen-prefix collision attack devised for Flame."
The analysis reinforces theories that researchers from Kaspersky Lab, CrySyS Lab, and Symantec published almost two weeks ago. Namely, Flame could only have been developed with the backing of a wealthy nation-state.
Source ARS
I've started to suspect that, by agreeing to install bloatware like Norton Security, McAfee.. what have you... so-called "anti-virus" security. That,
you are agreeing to install intrusive software that in more ways than one, resembles the fabled "man in the middle" scenario.
It's just taken for granted that your particular choice of Windows, or your particular choice of AV suite has no intention to harm. Antivirus software literally intercepts every data transfer, every major write to the disk. That is a "man in the middle" scenario. It is very easily corrupted for more nefarious means. It would be less than simple to suggest such methods could be used for obfuscation purposes.
It's just taken for granted that your particular choice of Windows, or your particular choice of AV suite has no intention to harm. Antivirus software literally intercepts every data transfer, every major write to the disk. That is a "man in the middle" scenario. It is very easily corrupted for more nefarious means. It would be less than simple to suggest such methods could be used for obfuscation purposes.
edit on 8-6-2012 by SyphonX
because: (no reason given)
I think this has to do with the White House leak confirming US involvement in Stuxnet development.
They can't afford another snafu. Since keyboards have been busy determining whether Flame generated from the US/Israel as well, I suppose they took that to mean the heat was on, best to put out the Flame. Better to look guilty, than be proven guilty.
Just like how Holder's email mentioning "Fast and Furious" was about the second round of the Candyland World Championships.
Makes me want to pour rat poison on my head and eat my own face off.
They can't afford another snafu. Since keyboards have been busy determining whether Flame generated from the US/Israel as well, I suppose they took that to mean the heat was on, best to put out the Flame. Better to look guilty, than be proven guilty.
Just like how Holder's email mentioning "Fast and Furious" was about the second round of the Candyland World Championships.
Makes me want to pour rat poison on my head and eat my own face off.
reply to post by Maxmars
My guess is to prevent it from being replicated or used as a template for something different/stronger that could be used to attack US computers. OR even more dangerously.. being used by a clever individual for nefarious purposes outside of government to defraud average users. This is smart thinking to have a suicide button, unlike stutnex that anyone can look at.
I wonder why?
My guess is to prevent it from being replicated or used as a template for something different/stronger that could be used to attack US computers. OR even more dangerously.. being used by a clever individual for nefarious purposes outside of government to defraud average users. This is smart thinking to have a suicide button, unlike stutnex that anyone can look at.
Originally posted by chasingbrahman
I think this has to do with the White House leak confirming US involvement in Stuxnet development.
They can't afford another snafu. Since keyboards have been busy determining whether Flame generated from the US/Israel as well, I suppose they took that to mean the heat was on, best to put out the Flame. Better to look guilty, than be proven guilty.
Just like how Holder's email mentioning "Fast and Furious" was about the second round of the Candyland World Championships.
Makes me want to pour rat poison on my head and eat my own face off.
I'm inclined to stray towards that inference too.... this kind of makes me think it may be a U.S.-related matter...
Barack Obama facing calls for investigation into intelligence leaks
The Obama administration is facing cross-party calls for an independent investigation into a spate of recent intelligence leaks about its secret war against al-Qaeda and efforts to disable Iran's nuclear programme using computer viruses.
Ugh. The politicians will be the death of us all.
Senior Republicans have accused the Obama White House of deliberately leaking material in order to burnish his credentials as commander-in-chief.
Senator John McCain, the 2008 Republican presidential candidate, said the leaks were deliberately designed to make the president "look decisive" and came from the "highest levels" of the White House, an accusation that the White House spokesman, Jay Carney, said was "grossly irresponsible".
reply to post by Maxmars
Here's an interesting point I had missed that I found in an interview here (Vitaly is from Kapersky labs):
Catch that? It was found once the UN requested it be researched. I would find it odd that the US/Israel created the Stuxnet hydra, and some other country developed Godzilla. Then there's this:
Sound like the wet dream of CISPA or NDAA yet?
Here's an interesting point I had missed that I found in an interview here (Vitaly is from Kapersky labs):
RT: So, how did you spot the malware, was it a planned investigation, or did it come by surprise?
Vitaly Kamlyuk: It was by surprise. We were initially searching for a [different form of] malware. We were aware of the malware that had spread throughout the Middle East, attacked hundreds of computers and wiped their hard drives, making the systems unbootable after that. It was actually after an inquiry from the International Telecommunications Union, which is a part of the United Nations, who actually asked us to start conducting research. When we started looking for this mysterious malware in the Middle East, we discovered this suspicious application that turned out to be even more interesting than the initial target of our search.
Catch that? It was found once the UN requested it be researched. I would find it odd that the US/Israel created the Stuxnet hydra, and some other country developed Godzilla. Then there's this:
It’s also quite unique in the way it steals information. It’s possible to steal different types of information with the help of this spyware tool. It can record audio if a microphone is attached to the infected system, it can do screen captures and transmit visual data. It can steal information from the input boxes when they are hidden behind asterisks, password fields; it can get information from there. Also it can scan for locally visible Bluetooth devices if there is a Bluetooth adapter attached to the local system.
Sound like the wet dream of CISPA or NDAA yet?
I think this has to do with the White House leak confirming US involvement in Stuxnet development.
I agree with this as well and expand the new instruction was to delete all evidence of so that it can not be rewitten and used agianst Us.
Flame and Stuxnet are the products of Operation Olympic Games and they gave away one of the biggest "assets" over a poll bounce.
reply to post by chasingbrahman
It certainly goes beyond the motives of normal cyber-attacks, doesn't it? Normally attacks are done for reasons of profiting from fraud, or theft. In the case of spying, the motive is localized and not broad, people data-mine for a specific purpose. I'm sure there could be organizations out there that have the sole intent of harvesting "all" information as much as possible, to broker it to other criminals, but they wouldn't be able to run such a tight ship, in my opinion.
It's like they have 20/20 hindsight in the matter. Press a button to turn it on, press a button to turn it off. Yea, okay.
It certainly goes beyond the motives of normal cyber-attacks, doesn't it? Normally attacks are done for reasons of profiting from fraud, or theft. In the case of spying, the motive is localized and not broad, people data-mine for a specific purpose. I'm sure there could be organizations out there that have the sole intent of harvesting "all" information as much as possible, to broker it to other criminals, but they wouldn't be able to run such a tight ship, in my opinion.
It's like they have 20/20 hindsight in the matter. Press a button to turn it on, press a button to turn it off. Yea, okay.
The problem with the antivirus software is they search through software files and look for files that operate in a certain way that is virus like. The
Stuxnet Flame Duqu are not complete files. They are pieces scattered through out the system. None of the pieces are whole. Take the Zip programs that
were created to zip files into compressed files. The antivirus programs used to have a hard time searching a zipped file for viruses. But they came
out with a program to search within a zipped file. So they began simply zipping files twice. But then they found a way to also look into a zip file
that has been zipped up to three times Zip programs then started with a feature to break zip files into multiple pieces and avoided the antivirus
scanning. And the antivirus companies still have not been able to create a smart scanner that can unsplit a zipped file and put it back together to
look inside. So then when you look at it in this light you start to see why TinyOS is the perfect program for STUXnet Flame Duqu. And TinyOS was
created to travel any platform any connection and operates the same way these zip programs have been doing it breaks apart into tiny pieces but still
operates as if it is a whole program still. Its a split into multiple pieces and zipped but acts as if it is whole. The anitvirus software has no
feature to do anything about it or even find it. The only thing they can do is search for it communicating. But TinyOS is made to operate in the
cellphone industry. It operates in burst and waits for normal communication and hides in it to reduce the power it uses. So finding its communication
means having to do a complete break down of every communication stream sent out. Very hard and time consuming project to under take.
nescc.sourceforge.net...
nescc.sourceforge.net...
edit on 8-6-2012 by JBA2848 because: (no reason given)
reply to post by JBA2848
Thank you for explaining how these viruses work in a way that I can actually understand! That's the first time an explanation has actually clicked in my brain. Needless to say I'm not very learned in computer jargin. Appreciation to you!
Thank you for explaining how these viruses work in a way that I can actually understand! That's the first time an explanation has actually clicked in my brain. Needless to say I'm not very learned in computer jargin. Appreciation to you!
reply to post by chasingbrahman
Flame and Stuxnet have similarities that show they are from the same origin. If the files had been left on the computers, then forensics teams could have traced the advancement of the code and had further proof of this.
Flame and Stuxnet have similarities that show they are from the same origin. If the files had been left on the computers, then forensics teams could have traced the advancement of the code and had further proof of this.
It occurs to me that I am about to ask what many may choose to think of as a very naive question. I suppose it is a matter of perception....
Since the last three noteworthy breakouts, (duqu, stuxnet, and now flame) all have distinctly 'advanced' qualities, ranging from cryptoanalytic, unique "new" code (the so-called "mystery-language"), and cross-platform operation - is it not possible that these packages are in fact machine "AI"-generated?
Anybody know anything about meta-programming decision-making code?
Since the last three noteworthy breakouts, (duqu, stuxnet, and now flame) all have distinctly 'advanced' qualities, ranging from cryptoanalytic, unique "new" code (the so-called "mystery-language"), and cross-platform operation - is it not possible that these packages are in fact machine "AI"-generated?
Anybody know anything about meta-programming decision-making code?
Originally posted by JBA2848
The problem with the antivirus software is they search through software files and look for files that operate in a certain way that is virus like. The Stuxnet Flame Duqu are not complete files. They are pieces scattered through out the system. None of the pieces are whole. Take the Zip programs that were created to zip files into compressed files. The antivirus programs used to have a hard time searching a zipped file for viruses. But they came out with a program to search within a zipped file. So they began simply zipping files twice. But then they found a way to also look into a zip file that has been zipped up to three times Zip programs then started with a feature to break zip files into multiple pieces and avoided the antivirus scanning. And the antivirus companies still have not been able to create a smart scanner that can unsplit a zipped file and put it back together to look inside. So then when you look at it in this light you start to see why TinyOS is the perfect program for STUXnet Flame Duqu. And TinyOS was created to travel any platform any connection and operates the same way these zip programs have been doing it breaks apart into tiny pieces but still operates as if it is a whole program still. Its a split into multiple pieces and zipped but acts as if it is whole. The anitvirus software has no feature to do anything about it or even find it. The only thing they can do is search for it communicating. But TinyOS is made to operate in the cellphone industry. It operates in burst and waits for normal communication and hides in it to reduce the power it uses. So finding its communication means having to do a complete break down of every communication stream sent out. Very hard and time consuming project to under take.
nescc.sourceforge.net...edit on 8-6-2012 by JBA2848 because: (no reason given)
Even if the code stream is broken up into a myriad of pieces, there is still a small kernel piece that is systematically accessing those pieces and pipe lining them into the CPU. The CPU will treat the code like any other multi-threaded process. So the detector here needs to be a realtime debugger application that operates at the instruction pointer level, and has access to all the registers.
The software designed to detect Stuxnet and Flame, will be the only code that can access the debugger stream. This has to be bundled in the OS of the host in such a way that it can be turned on, and is an intrisic part of the firmware, so if it supposed to be on, and not running, then nothing runs.
There is nothing a human can make that another cannot tear apart.
new topics
-
Pelosi injured in Luxembourg
Other Current Events: 1 hours ago -
Nov 2024 - Former President Barack Hussein Obama Has Lost His Aura.
US Political Madness: 3 hours ago -
Something better
Dissecting Disinformation: 8 hours ago -
The Witcher IV — Cinematic Reveal Trailer | The Game Awards 2024
Video Games: 10 hours ago -
Friday thoughts
General Chit Chat: 11 hours ago -
More Ons?
Political Conspiracies: 11 hours ago -
Canada Post strike ended by the Government of Canada
Mainstream News: 11 hours ago
top topics
-
They Know
Aliens and UFOs: 16 hours ago, 18 flags -
Something better
Dissecting Disinformation: 8 hours ago, 8 flags -
Pelosi injured in Luxembourg
Other Current Events: 1 hours ago, 7 flags -
More Ons?
Political Conspiracies: 11 hours ago, 6 flags -
Nov 2024 - Former President Barack Hussein Obama Has Lost His Aura.
US Political Madness: 3 hours ago, 6 flags -
Friday thoughts
General Chit Chat: 11 hours ago, 5 flags -
Canada Post strike ended by the Government of Canada
Mainstream News: 11 hours ago, 4 flags -
The Witcher IV — Cinematic Reveal Trailer | The Game Awards 2024
Video Games: 10 hours ago, 3 flags -
Drones (QUESTION) TERMINATOR (QUESTION)
General Chit Chat: 17 hours ago, 1 flags
active topics
-
Pelosi injured in Luxembourg
Other Current Events • 12 • : WeMustCare -
They Know
Aliens and UFOs • 66 • : Springbok -
A Bunch of Maybe Drones Just Flew Across Hillsborough County
Aircraft Projects • 70 • : WeMustCare -
Biden pardons 39 and commutes 1500 sentences…
Mainstream News • 28 • : charlyv -
The Witcher IV — Cinematic Reveal Trailer | The Game Awards 2024
Video Games • 5 • : Hypntick -
Nov 2024 - Former President Barack Hussein Obama Has Lost His Aura.
US Political Madness • 11 • : WeMustCare -
Something better
Dissecting Disinformation • 14 • : chr0naut -
Drones everywhere in New Jersey
Aliens and UFOs • 109 • : WeMustCare -
More Ons?
Political Conspiracies • 18 • : rickymouse -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 3669 • : xuenchen
