It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
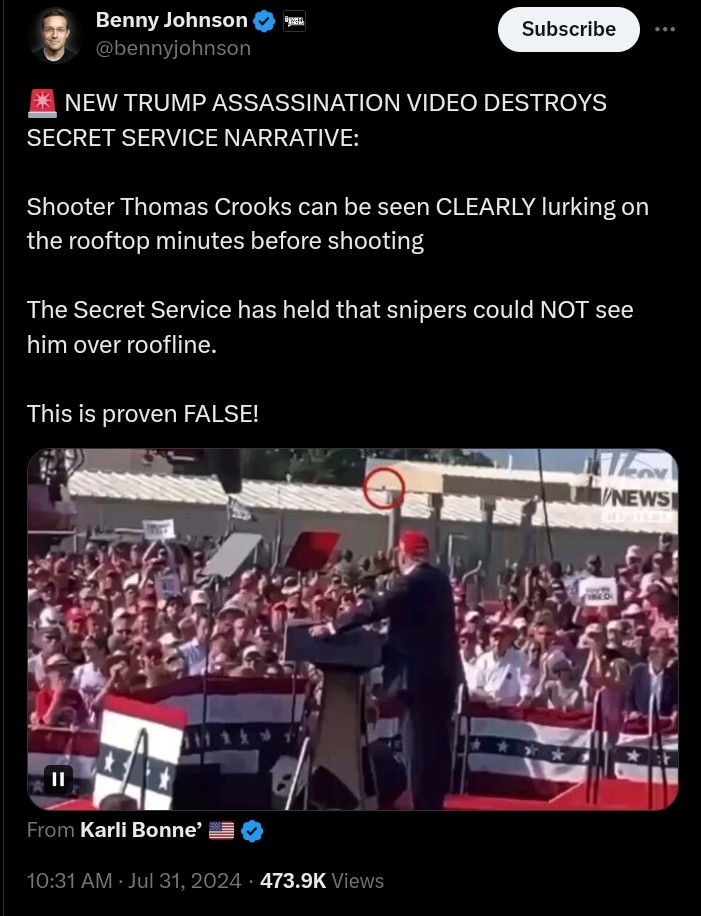
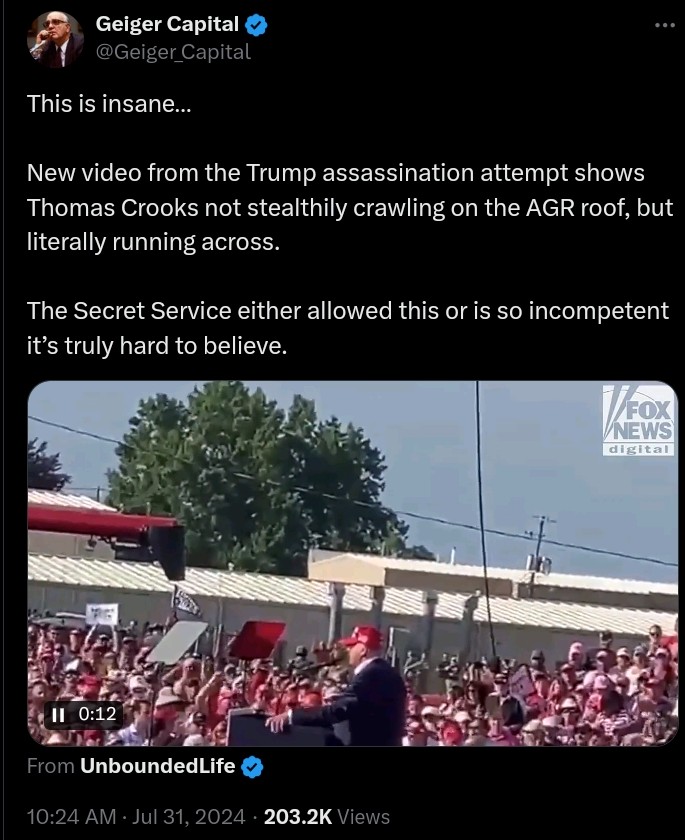
FBI dep. dir. Abbate says FBI still doesn't have access to all the encrypted accounts on the Trump shooter's emails
I bet they do and they are covering what they found for political reasons.
originally posted by: Zanti Misfit
a reply to: grey580
Intelligence Agencies have " Back Doors " to EVERY Piece of Tech the Public is Allowed to Have . Come On Man ! Your Not that Naive , Right ?
Nah, disagree, which is to say that a backdoor of that sort is only as good as the person who would theoretically be vulnerable to it not knowing how to circumvent it. I'm no expert hacker, but have done some reading on this subject over the years, and as far as I know that's how it works.
Oh sure, What's App, it's run by Facebook, they'd flip on most anybody I'd suspect in a heartbeat. Snapchat, the messages disappear, ooooh. Doesn't mean a thing if there's a man in the middle screen capping everything. Other encrypted messaging services may or may not be as secure as they like to represent to the public, but are likely mostly susceptible to IC pressure. There are also backdoors built into much of the hardware, as you claim, such as the "management engine" system built in to most PC's, plus other hardware hacks I have heard rumors of that I wouldn't be surprised to find were true.
Thing is, there are workarounds for most of that technology as far as I know. For instance, an encrypted message exchange site where the sender simply posts the encrypted characters to a bulletin board. Anybody can look at it, but nobody without the right key can decrypt it. Pretty simple really, not much to go wrong there if you want to keep your messages from being read by anybody other than the intended recipient. If your management engine feature is disabled, and other backdoor spying features are also circumvented, and the password protecting the encryted message is sufficiently strong to protect it, I'd guess that that's pretty difficult to crack, if not impossible. I could be wrong, but I don't think I am.
Don't get me wrong though. I don't find it hard to believe at all that the attempted hit on Trump was intentionally allowed to happen even if it wasn't planned and orchestrated by some nefarious insiders. Honestly don't find it hard to believe that it may have indeed been planned and orchestrated by nefarious insiders. I'm just not so sure that the FBI could easily crack his encrypted coms. As far as I know they can't, if he was doing it right.
originally posted by: cherokeetroy
x.com...
x.com...
I'd say it's pretty safe to say...we now know what happened to JFK.
I would have never thought it possible, but there are elements within our government whom are actively involved in the assassination of political candidates / leaders in this country.
On a side note, people have often questioned what revelations have come about on ATS over the years. This incident is probably one of the biggest of all time. And what is this revelation? Well, despite all the naysayers, there really IS a "Deep State". That's HUGE!
a reply to: Zanti Misfit
That's funny. As if changing some settings would actually make one of those Orwellian spying machines secure.
We both know that's not how that works. Regardless, the fact that almost every smartphone made is made with built in back doors, as you say, doesn't mean that a person can't figure out how to send encrypted messages that can't be hacked easily, or at all even.
That's funny. As if changing some settings would actually make one of those Orwellian spying machines secure.
We both know that's not how that works. Regardless, the fact that almost every smartphone made is made with built in back doors, as you say, doesn't mean that a person can't figure out how to send encrypted messages that can't be hacked easily, or at all even.
a reply to: F2d5thCavv2
I would imagine they have their vulnerabilities built in just like the rest of the standard industrially produced equipment, but according to these articles, even if they didn't, Apple will gladly roll over on you at law enforcement request.
appleinsider.com...
www.wired.com...
If you watch the Eric Prince interview that Tucker Carlson conducted, he has started a coms company known as Unplugged that is built for security but that also does not keep customer records that can be made available to law enforcement. The service provider HAS nothing to provide even if they are forced by court order to do so.
There was a company called Black Phone, and its companion service provider known as Silent Circle, that also made strong claims about protecting privacy. Not sure what came out in the wash with those guys.
Edit to add:
Silent Circle's website, and a cnet article that came up reviewing the "Blackphone 2":
www.silentcircle.com...
www.cnet.com...
The Unplugged Phone's site and a couple of reviews. Technology Review doesn't like it, Medium's Headline seems more positive in outlook:
unplugged.com...
www.technologyreview.com...
medium.com...@aihelpbot/introducing-unplugged-the-future-of-privacy-and-security-9b6f112e96fb
I would imagine they have their vulnerabilities built in just like the rest of the standard industrially produced equipment, but according to these articles, even if they didn't, Apple will gladly roll over on you at law enforcement request.
appleinsider.com...
www.wired.com...
If you watch the Eric Prince interview that Tucker Carlson conducted, he has started a coms company known as Unplugged that is built for security but that also does not keep customer records that can be made available to law enforcement. The service provider HAS nothing to provide even if they are forced by court order to do so.
There was a company called Black Phone, and its companion service provider known as Silent Circle, that also made strong claims about protecting privacy. Not sure what came out in the wash with those guys.
Edit to add:
Silent Circle's website, and a cnet article that came up reviewing the "Blackphone 2":
www.silentcircle.com...
www.cnet.com...
The Unplugged Phone's site and a couple of reviews. Technology Review doesn't like it, Medium's Headline seems more positive in outlook:
unplugged.com...
www.technologyreview.com...
medium.com...@aihelpbot/introducing-unplugged-the-future-of-privacy-and-security-9b6f112e96fb
edit on 3-8-2024 by badcabbie because: to add the last bit
a reply to: F2d5thCavv2
That's nice. I think you can get into the bios and disable it in most pc type computers. Some will malfunction slightly if you do it though, so I've heard. It shuts off every thirty minutes or so or something like that.
There's a thread on here about it I did in a past life before the accountpocalypse. Let me see...
There it is!
www.abovetopsecret.com...
I was able to provide some decent info for that thread.
That's nice. I think you can get into the bios and disable it in most pc type computers. Some will malfunction slightly if you do it though, so I've heard. It shuts off every thirty minutes or so or something like that.
There's a thread on here about it I did in a past life before the accountpocalypse. Let me see...
There it is!
www.abovetopsecret.com...
I was able to provide some decent info for that thread.
a reply to: F2d5thCavv2
If you read the federal encryption laws here in the US carefully, you will see it is not only illegal to use encryption which doesn't have a backdoor, but a major offense (like life imprisonment level of 'major') if you get caught using any such encryption across the US border. It doesn't say those exact words, but after you read it several times you'll see where they basically lay out, specifically, what types of encryption are okay, and what ones are not. The essence of it is...anything they don't know about is illegal, and anything they do know about is okay. In other words, they have a backdoor into the ones they know. They go on at length about how any home-brew encryption method beyond a certain level of complexity is highly illegal. There's basically no other way to interpret it, the way they have the laws written.
I would imagine the same laws apply to cellular phone technology. So, as long as you don't use it internationally (i.e. 'across' US borders) you 'might' be okay, but the minute you phone your elderly aunt across the US border you become Public Enemy No. 1 and go on the "10 Most Wanted" list.
I was actually surprised to see this much level of detail codified into law. Normally, laws like this are intentionally left vague, but not the laws governing encryption.
The recent Crowdstrike patch debacle demonstrates just how thorough these backdoors are. The fact any Windows based computers could not even boot up without first being modified illustrates the very low level entry points. The Crowdstrike issue wasn't a virus or a hack, it was just a blown patch update, but it shows how early in the startup (boot) process access to a machine is granted. LINUX and Apple machines were immune, as were any Windows machines not running the Crowdstrike applications. But most large organizations had secretly been running Crowdstrike in the background at the enterprise level for years. (probably did a horrible job explaining what I'm trying to say right here, but you get the idea). To think Intel and AMD don't have backdoors down at the CPU and chipset level is not surprising at all. In fact, I would be shocked if they did NOT have backdoors.
If you read the federal encryption laws here in the US carefully, you will see it is not only illegal to use encryption which doesn't have a backdoor, but a major offense (like life imprisonment level of 'major') if you get caught using any such encryption across the US border. It doesn't say those exact words, but after you read it several times you'll see where they basically lay out, specifically, what types of encryption are okay, and what ones are not. The essence of it is...anything they don't know about is illegal, and anything they do know about is okay. In other words, they have a backdoor into the ones they know. They go on at length about how any home-brew encryption method beyond a certain level of complexity is highly illegal. There's basically no other way to interpret it, the way they have the laws written.
I would imagine the same laws apply to cellular phone technology. So, as long as you don't use it internationally (i.e. 'across' US borders) you 'might' be okay, but the minute you phone your elderly aunt across the US border you become Public Enemy No. 1 and go on the "10 Most Wanted" list.
I was actually surprised to see this much level of detail codified into law. Normally, laws like this are intentionally left vague, but not the laws governing encryption.
The recent Crowdstrike patch debacle demonstrates just how thorough these backdoors are. The fact any Windows based computers could not even boot up without first being modified illustrates the very low level entry points. The Crowdstrike issue wasn't a virus or a hack, it was just a blown patch update, but it shows how early in the startup (boot) process access to a machine is granted. LINUX and Apple machines were immune, as were any Windows machines not running the Crowdstrike applications. But most large organizations had secretly been running Crowdstrike in the background at the enterprise level for years. (probably did a horrible job explaining what I'm trying to say right here, but you get the idea). To think Intel and AMD don't have backdoors down at the CPU and chipset level is not surprising at all. In fact, I would be shocked if they did NOT have backdoors.
edit on 8/3/2024 by Flyingclaydisk because: (no reason given)
a reply to: badcabbie
Yes, that was a good post and article. I remember reading it back in '19.
A lot of interesting things which go on in the encryption and secrets world which people don't understand.
I kind of stopped worrying about government eavesdropping a long time ago; if they want to listen, they'll find a way. The best way to keep secrets is to not keep secrets. People who look like they have a secret will be the ones subjected to the most scrutiny.
Yes, that was a good post and article. I remember reading it back in '19.
A lot of interesting things which go on in the encryption and secrets world which people don't understand.
I kind of stopped worrying about government eavesdropping a long time ago; if they want to listen, they'll find a way. The best way to keep secrets is to not keep secrets. People who look like they have a secret will be the ones subjected to the most scrutiny.
a reply to: Flyingclaydisk
Correct. The Deep State is a thing. You can see symptoms of it in the lawfare waged on Trump, the full court press against him by almost the entirety of the corporate media since 2015 or so. Fox dutifully performing as controlled opposition at the appropriate times. The successful seduction of our regulatory agencies by corporate interests. Lots of other observable symptoms if one cares to think on and look thoroughly enough into it. Those come to mind off the top of my head though.
Edit to add a reply to your last post:
I'd tend to agree, which is to say that one can probably make one's tech equipment perfectly private with enough due diligence and effort, but who really wants to work that hard?
The other technical challenge I see in it is that it's still a pretty small playing field right now. By that I mean to say that the numbers of users that are making their communications truly private are still pretty small, and therefore more noticeable when communicating in such a fashion. Being noticed while engaging in "being private"(gasp! The horror!) might invite extra scrutiny from those who like to get into everybody's private business. As the numbers of private users increase, the risk of standing out due to "being private" should decrease.
Correct. The Deep State is a thing. You can see symptoms of it in the lawfare waged on Trump, the full court press against him by almost the entirety of the corporate media since 2015 or so. Fox dutifully performing as controlled opposition at the appropriate times. The successful seduction of our regulatory agencies by corporate interests. Lots of other observable symptoms if one cares to think on and look thoroughly enough into it. Those come to mind off the top of my head though.
Edit to add a reply to your last post:
I'd tend to agree, which is to say that one can probably make one's tech equipment perfectly private with enough due diligence and effort, but who really wants to work that hard?
The other technical challenge I see in it is that it's still a pretty small playing field right now. By that I mean to say that the numbers of users that are making their communications truly private are still pretty small, and therefore more noticeable when communicating in such a fashion. Being noticed while engaging in "being private"(gasp! The horror!) might invite extra scrutiny from those who like to get into everybody's private business. As the numbers of private users increase, the risk of standing out due to "being private" should decrease.
edit on 3-8-2024 by
badcabbie because: more editing
a reply to: Flyingclaydisk
The most galling thing about this kind of crap is that for all the pervasive spying, the bastards still can't prevent surprise attacks. Our IC's history is rife with spectacular failures.
Cheers
The most galling thing about this kind of crap is that for all the pervasive spying, the bastards still can't prevent surprise attacks. Our IC's history is rife with spectacular failures.
Cheers
new topics
-
What's on your mind today?
General Chit Chat: 1 hours ago -
The Nephilim Looked Like Clowns
General Conspiracies: 1 hours ago -
Three very good short films
Movies: 4 hours ago -
Massive Protest Over X Ban in Brasil September 7 Led By Former Leader Jair Bolsonaro
Social Issues and Civil Unrest: 7 hours ago -
Turkey Calls for an Islamic Alliance to Counter Israeli Expansionist Threat
Middle East Issues: 8 hours ago -
BIden Took 48 Years Worth of Vacation While President
US Political Madness: 10 hours ago -
Elderly British Couple Use Double Suicide Pod in Switzerland
Social Issues and Civil Unrest: 11 hours ago
top topics
-
Donald TRUMP on the Fate of Election Fraudsters if Americans Elect Him President Again.
2024 Elections: 17 hours ago, 17 flags -
BIden Took 48 Years Worth of Vacation While President
US Political Madness: 10 hours ago, 15 flags -
Turkey Calls for an Islamic Alliance to Counter Israeli Expansionist Threat
Middle East Issues: 8 hours ago, 10 flags -
Massive Protest Over X Ban in Brasil September 7 Led By Former Leader Jair Bolsonaro
Social Issues and Civil Unrest: 7 hours ago, 9 flags -
Elderly British Couple Use Double Suicide Pod in Switzerland
Social Issues and Civil Unrest: 11 hours ago, 5 flags -
Three very good short films
Movies: 4 hours ago, 4 flags -
The Nephilim Looked Like Clowns
General Conspiracies: 1 hours ago, 1 flags -
What's on your mind today?
General Chit Chat: 1 hours ago, 1 flags
active topics
-
BIden Took 48 Years Worth of Vacation While President
US Political Madness • 14 • : visitedbythem -
The Nephilim Looked Like Clowns
General Conspiracies • 8 • : theatreboy -
Donald TRUMP on the Fate of Election Fraudsters if Americans Elect Him President Again.
2024 Elections • 41 • : Oldcarpy2 -
Show me the financial gain Trump got from being POTUS.
US Political Madness • 65 • : LollieK3 -
Female is Not a Feeling
Rant • 87 • : BrucellaOrchitis -
Nano bots in the vaccine
Science & Technology • 66 • : Oldcarpy2 -
Embalmers clots analysed
Science & Technology • 33 • : chr0naut -
What's on your mind today?
General Chit Chat • 5 • : SteamyAmerican -
Father of teen suspect in Georgia school shooting charged with 2nd-degree murder
Mainstream News • 119 • : LollieK3 -
Elderly British Couple Use Double Suicide Pod in Switzerland
Social Issues and Civil Unrest • 23 • : BrucellaOrchitis