It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
a reply to: Justoneman
And just because he's in the hospital doesn't mean he can't do the job.
I think they're protecting him.
And the lefties who can't wait to see him die can go F themselves. The sh*t will hit the fan if they pull any Pelosi crap.
And just because he's in the hospital doesn't mean he can't do the job.
I think they're protecting him.
And the lefties who can't wait to see him die can go F themselves. The sh*t will hit the fan if they pull any Pelosi crap.
a reply to: Creep Thumper
Reminds me of the Godfather's movie where the mob tried to get in the hospital to kill Michael's dad. I hope all the security people there are being vetted and re-vetted.
Reminds me of the Godfather's movie where the mob tried to get in the hospital to kill Michael's dad. I hope all the security people there are being vetted and re-vetted.
originally posted by: carewemust
a reply to: Creep Thumper
Reminds me of the Godfather's movie where the mob tried to get in the hospital to kill Michael's dad. I hope all the security people there are being vetted and re-vetted.
I hope so too. I've been worried about his safety and the safety of his family daily.
There are absolutely vile people out there who would kill him in a heartbeat.
Overall, I think the SS has done an amazing job protecting him.
originally posted by: 1010set
originally posted by: PokeyJoe
Check out what journalist Lara Logan just tweeted out, out of the blue:
10 U.S. Code § 894 - Art. 94. Mutiny or sedition | U.S. Code | US Law | LII / Legal Information Institute law.cornell.edu...
twitter.com...
Logan is one of the only honest, neutral, trustworthy investigative journalists left. Very interesting she would choose today to tweet this out.
10 U.S. Code § 894 - Art. 94. Mutiny or sedition | U.S. Code | US Law | LII / Legal Information Institute law.cornell.edu...
twitter.com...
Logan is one of the only honest, neutral, trustworthy investigative journalists left. Very interesting she would choose today to tweet this out.
Her attitude and personality have markedly shifted since the events in Egypt. I've come to rely on her reporting. She is not prone to hubris or hyperbole. Something to keep an eye on.
I noticed someone quoted the text where it says
"or anyone failing to suppress a mutiny or sedition or failing to report mutiny or sedition."
and
"is guilty of failure to suppress a mutiny or sedition"
That is what the Seattle and Portland Mayors appear guilty of doing. Failing to report or suppress sedition.
edit on 2-10-2020 by Justoneman because: (no reason given)
originally posted by: Vasa Croe
a reply to: EndtheMadnessNow
I did a boatload of research a number of years back on symbols looking into the Zodiac Killer case and I could swear I came across this zia like symbol. I want to say it is a "walking" symbol if you know what that means.
If I can dig up all my old stuff I will go through it.
Basically a walking symbol has a slant or kick to it to imply motion.
This one is really bugging me.
Heh, you and me both. I searched around for an hour and came up dry. Must be looking in all the wrong places. Hmm, "walking" symbol, ok I understand what you mean now. If I find anything noteworthy I'll post back.
originally posted by: ketsuko
a reply to: butcherguy
Since we know he's ostensibly being fed what to say, has anyone checked to see if any of his number gaffes are coded language in any way?
Since there is a NAZI Collabrator funding this mess, you bring up a fantastic question.
From: WIKI: The Enigma Machine
The Enigma machine is an encryption device developed and used in the early- to mid-20th century to protect commercial, diplomatic and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the German military.
Enigma has an electromechanical rotor mechanism that scrambles the 26 letters of the alphabet. In typical use, one person enters text on the Enigma's keyboard and another person writes down which of 26 lights above the keyboard lights up at each key press. If plain text is entered, the lit-up letters are the encoded ciphertext. Entering ciphertext transforms it back into readable plaintext. The rotor mechanism changes the electrical connections between the keys and the lights with each keypress. The security of the system depends on a set of machine settings that were generally changed daily during the war, based on secret key lists distributed in advance, and on other settings that were changed for each message. The receiving station has to know and use the exact settings employed by the transmitting station to successfully decrypt a message.
While Germany introduced a series of improvements to Enigma over the years, and these hampered decryption efforts to varying degrees, they did not ultimately prevent Britain and its allies from exploiting Enigma-encoded messages as a major source of intelligence during the war. Many commentators say the flow of communications intelligence from Ultra's decryption of Enigma, Lorenz and other ciphers shortened the war significantly and may even have altered its outcome.
From: scienceabc.com
What Did the Enigma Machine Do?
Essentially, the Enigma Machine did the same work as any other cipher machine; it facilitated the encryption of classified communication. In other words, it coded and decoded messages that were then transmitted over thousands of miles. Although the machine was originally meant to be used to transmit confidential business-related information, but in the late 1930s, its unmatched potential as a transmission device in the theater of warfare was realized.
How Did the Enigma Machine Work?
As mentioned earlier, the Enigma Machine is an electromechanical device, which works through mechanical parts as an electric current passes through it.
The machine consists of four main components: the keyboard, plugboard, lampboard and rotors. When you press a key on the keyboard (L, for example), an electric signal is generated, which subsequently moves through all of these components to encrypt an alphabet.
The first stopping point of the electric signal (generated from the ‘L’) is the plugboard. Some of the letters on the plugboard might be connected to another letter (let’s say M). Now, the signal is diverted through ‘M’. The next stop is the static rotor, which doesn’t do anything to the signal, but it does turn the wires into contacts, since the signal can only pass when the contacts touch. The output of the static rotor acts as the input to the moving rotors. This is where most of the scrambling takes place.
From: worldcryptoindex.com
Enigma is an off-chain decentralized network that enables blockchains to store and run private computations on data. The public nature of the blockchain guarantees transparency by creating an unchangeable record of activities, but this level of transparency limits the potential use cases of its technology. Private data will be fully exposed when it flows through nodes on the blockchain. Sensitive information would have to stored and processed in centralized manner for security, which defeats the purpose of using the blockchain in the first place.
Enigma is creating a decentralized computation platform that guarantees two core functions for blockchain networks:
1. Privacy – Enigma uses multiparty computation (MPC) and a distributed hash table to store and compute data queries without relying on third parties. Every node on the network handles a random piece of the data and no single node can access the data in its entirety.
2. Scalability – Computations and data storage on Enigma are not replicated by every node in the network. Each node performs computation over different parts of the data. The decreased redundancy enables more demanding computations and allows blockchains to scale.
So what if these numbers are like like wheel locks on the original Enigma Machine, and they are then used for decoding certain messages that are sent. By using Blockchain encryption it should in theory make it nearly impossible to decipher what is being said, but if you know the code then all the doors are opened for you. Could they be using a system similar to the original Enigma Machine to create the blockchain encryption code. Like how Assange has that deadman's switch encodement, do we need the use a physical working Enigma Machine to get their code to decrypt them?
Does anyone know of an Enigma Machine simulator that can be found on-line? I was going to look for a replica of one to see how much they cost, but strangely even though they seem to be popular amongst hobbyist to make, I couldn't find any for sale. They seem to have been all sold out?
originally posted by: thesaint
New tweet (video) from POTUS
twitter.com...
Maybe President Trump made that secret trip to Walter Reed last year in order to approve set up of his Deep State takedown Command Center.
Mayor of Rochester New York just arrested for election fraud.
mobile.twitter.com...
Maybe congresswoman ilhan Omar's days Freedom are numbered.
mobile.twitter.com...
Maybe congresswoman ilhan Omar's days Freedom are numbered.
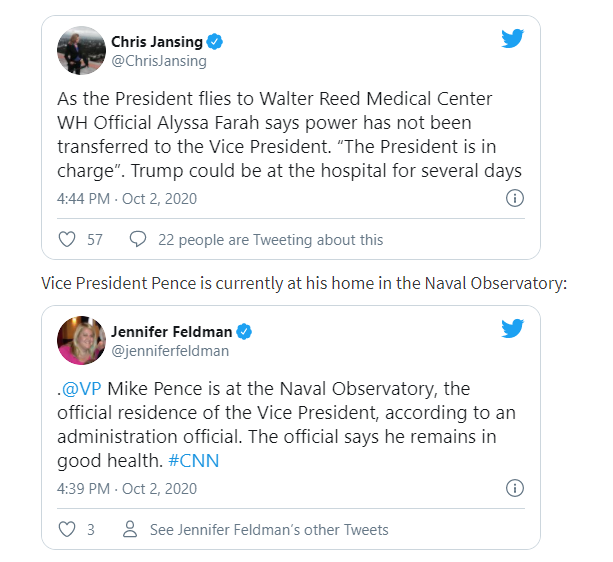
Being reported
that the move to Walter Reed is Trump's idea. Sources say the president's germophobia is getting the better of him now that he has started
displaying symptoms.
So while he is showing symptoms, the move to Walter Reed is possibly more related to hypochondria than any actual medical distress at the moment.
So while he is showing symptoms, the move to Walter Reed is possibly more related to hypochondria than any actual medical distress at the moment.
originally posted by: CanadianMason
Too good not to share!
Nobody bid on Trudeau's contract to confiscate our firearms 😆
I'd like to see them try to take Trillium's hefty collection, haha!
LOL thank CM
Guess I will be the first one taken out
And no I did not suicide myself
originally posted by: LanceCorvette
originally posted by: brewtiger
a reply to: RelSciHistItSufi
Hi Onehuman and Rel,
Considering "10 days of darkness" like that makes sense.
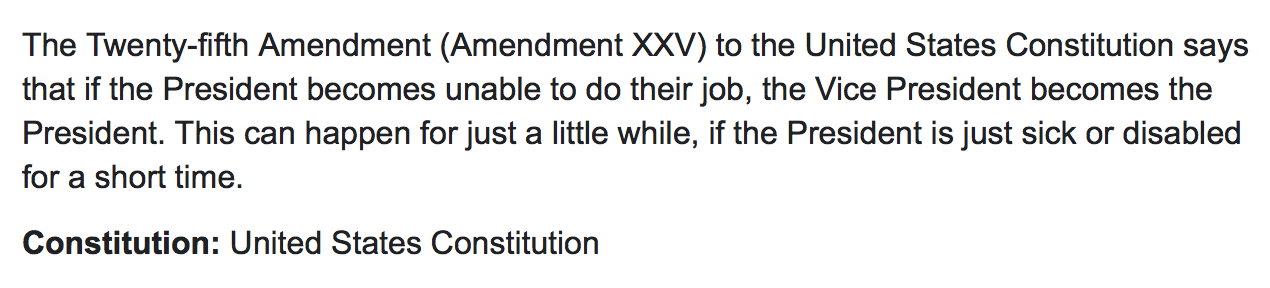
His illness/isolation opens the door to the 25th Amendment.
10 days of darkness = POTUS temporarily hands over power
Presidential Succession Act of 1947 says VP then SOTH
States completed ratification of 25th Amendment on Feb 10,1967
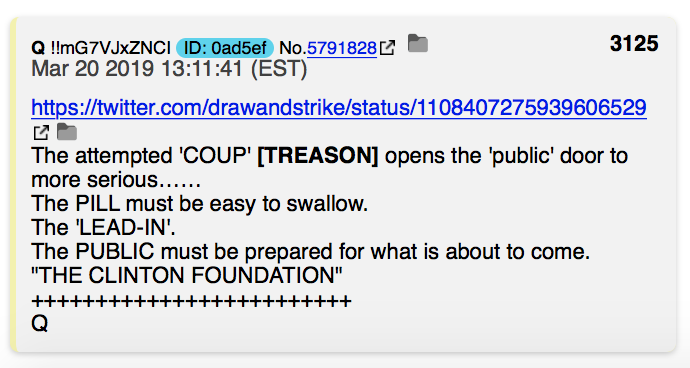
Feb 10 = 2/10 mirrors 10/2 = Oct 2
Q3125 has 25 "+" = plus sign = addition
- Merriam-Webster lists "addition" as a related word to amendment
- Opens the door = gives an opportunity for 25th Amendment
Q1947
How do you set a trap?
Open the door and we shall always walk though and take control.
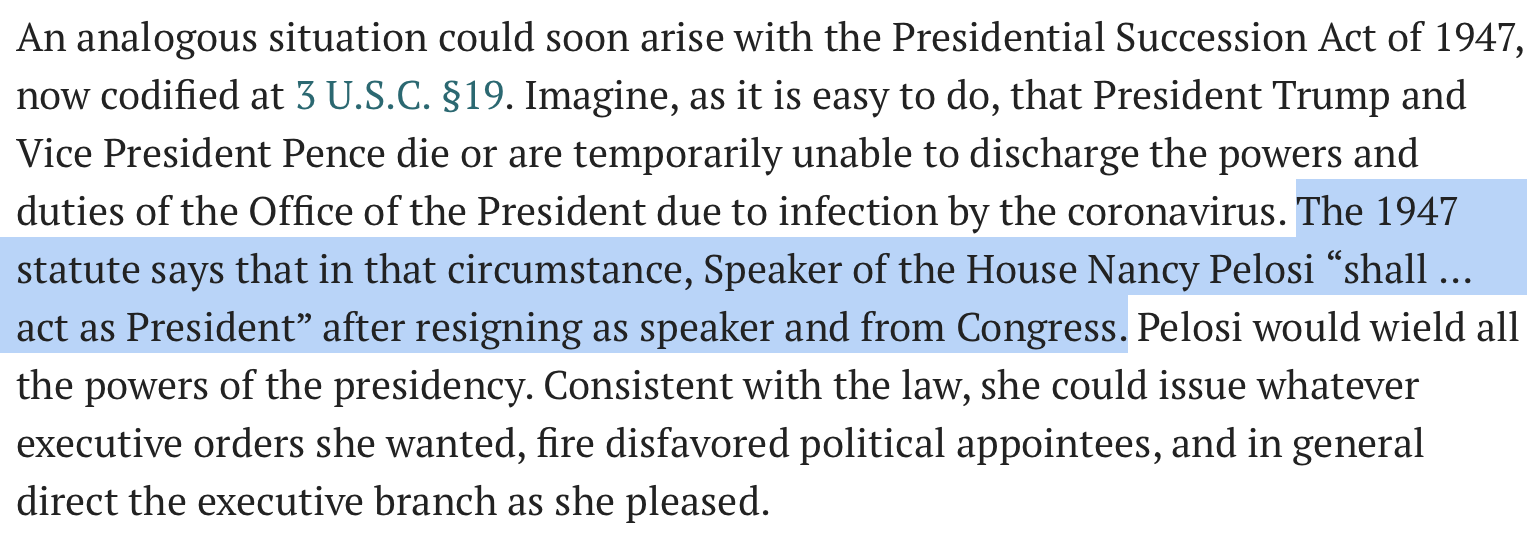
A Presidential Succession Nightmare
- VP is clearly the 1st in line
- There is open debate about 2nd in line: SOTH or Sec of State
- Presidential Succession Act of 1947 states SOTH is 2nd
- Others see "Officials" as non-Congress / Executive Branch
- Nightmare where 2 people try to claim power/sworn in
- They would wield all the powers of the presidency (EO, firings, pardons).
- Any potential disputes would be settled by the Supreme Court.
- If SOTH assumes power, Pelosi would have to resign as Speaker/Congress.
- Trust Kansas.
Taken 2 Ending Scene
A situation where peace terms offered for the good of mankind?
Stand down, accept consequences & live with it... or destroy yourselves?
GAME OVER
Continue to pray.
We have words, words have meaning, let's use them.
The Vice President becomes "Acting President", not "President".
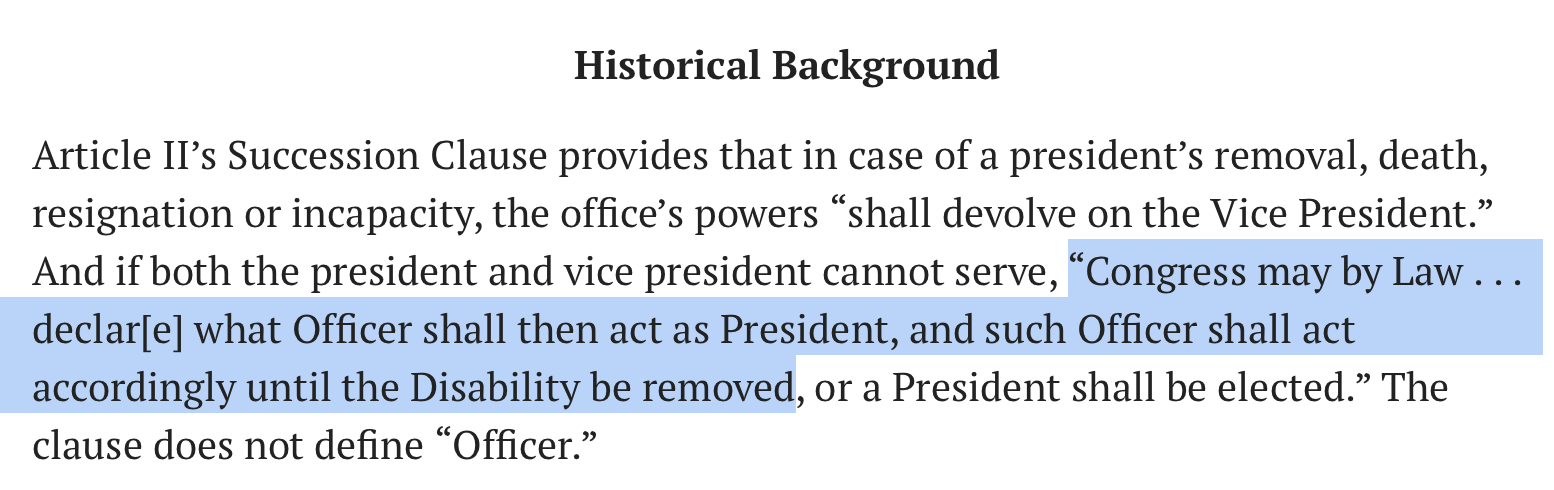
In multiple discussions about the 25th Amendment today, I have yet to see anyone quote it or link to it. Allow me:
www.usconstitution.net...
4. Whenever the Vice President and a majority of either the principal officers of the executive departments or of such other body as Congress may by law provide, transmit to the President pro tempore of the Senate and the Speaker of the House of Representatives their written declaration that the President is unable to discharge the powers and duties of his office, the Vice President shall immediately assume the powers and duties of the office as Acting President.
Thereafter, when the President transmits to the President pro tempore of the Senate and the Speaker of the House of Representatives his written declaration that no inability exists, he shall resume the powers and duties of his office unless the Vice President and a majority of either the principal officers of the executive department or of such other body as Congress may by law provide, transmit within four days to the President pro tempore of the Senate and the Speaker of the House of Representatives their written declaration that the President is unable to discharge the powers and duties of his office. Thereupon Congress shall decide the issue, assembling within forty eight hours for that purpose if not in session. If the Congress, within twenty one days after receipt of the latter written declaration, or, if Congress is not in session, within twenty one days after Congress is required to assemble, determines by two thirds vote of both Houses that the President is unable to discharge the powers and duties of his office, the Vice President shall continue to discharge the same as Acting President; otherwise, the President shall resume the powers and duties of his office.
So a whopping 66.66% of the Senate AND Congress have to vote to replace the POTUS with the "Acting POTUS" if the POTUS is not capable of discharging his duties.
Well we know, Pelosi will say he is incapable from day one to do that and will always lie to gain more power. Who decides that a POTUS is incapable when their is no honor among the Political thieves? This is sure shaping up to be like Rome in a lot of ways. I pray we all get past this with a laugh at the pub throwing down some beers.
a reply to: SouthernGift
We’re tapped into the freaking source, man. Nothing is random. No coincidences. We are all here right now, in this very moment because we’re supposed to be.
Trust the plan.
We’re tapped into the freaking source, man. Nothing is random. No coincidences. We are all here right now, in this very moment because we’re supposed to be.
Trust the plan.
a reply to: carewemust
It's all over the net that he's a germophobe, so hypochondria goes hand in hand with that. It wouldn't take much for a person getting symptoms with this thing to get worried.
I know I would even though I rationally know there ought to be very little for me to worry about. The press has thoroughly done its job.
It's all over the net that he's a germophobe, so hypochondria goes hand in hand with that. It wouldn't take much for a person getting symptoms with this thing to get worried.
I know I would even though I rationally know there ought to be very little for me to worry about. The press has thoroughly done its job.
My favorite comment so far,
“ Hillary Clinton has tested negative for being president“
“ Hillary Clinton has tested negative for being president“
originally posted by: Aallanon
My favorite comment so far,
“ Hillary Clinton has tested negative for being president“
Babylon Bee had a good observation too, but I'm not sure it's even satire:
Party that wants to run your health care roots for political opponent to die!
a reply to: Guyfriday
Yes I'm replying to myself.
I found an Enigma Machine Emulator: 101computing.net
I didn't realize that it uses; Roman numbers, Letter substations, and colors.
I wonder if this would be any good poking a stick at?
Yes I'm replying to myself.
I found an Enigma Machine Emulator: 101computing.net
I didn't realize that it uses; Roman numbers, Letter substations, and colors.
To gain a better understanding of the encryption techniques used by the enigma machine we have decided to recreate a virtual Enigma machine/emulator.
You will be able to use this machine to both encrypt or decrypt enigma messages (Enigma encryption is symmetric, which means that the same settings can be used to both encrypt or decrypt a message).
Our Enigma machine emulator is replicating the encryption process of the Enigma M3 series that was used by the German Navy (Kriegsmarine). It is fitted with a UKW-B reflector. Later on through the war, it was replaced by the M4 series which included a 4throtor.
Before pressing any keys on the keyboard section of the machine you will need to apply the required settings. To do so you will need to click on the rotors to adjust the wheels initial settings and then make the required connections by clicking on the different plugs (bottom section of the machine) to connect letters from the plugboard. Actual enigma settings are defined in the code book provided (see link on the left).
I wonder if this would be any good poking a stick at?
new topics
-
Alien warfare predicted for December 3 2024
Aliens and UFOs: 1 hours ago -
Statements of Intent from Incoming Trump Administration Members - 2025 to 2029.
2024 Elections: 10 hours ago
top topics
-
Statements of Intent from Incoming Trump Administration Members - 2025 to 2029.
2024 Elections: 10 hours ago, 8 flags -
Could Biden pardon every illegal alien
Social Issues and Civil Unrest: 12 hours ago, 7 flags -
Alien warfare predicted for December 3 2024
Aliens and UFOs: 1 hours ago, 6 flags -
Stop the Presses! Turkey Soup.
Food and Cooking: 12 hours ago, 5 flags -
'Proud Prophet' 12 Day Exercise Predicted Global Nuclear Catastrophe
World War Three: 17 hours ago, 4 flags
active topics
-
Alien warfare predicted for December 3 2024
Aliens and UFOs • 7 • : gortex -
Never say Never?
Science & Technology • 36 • : Oldcarpy2 -
Biden pardons his son Hunter despite previous pledges not to
Mainstream News • 114 • : fringeofthefringe -
Lies lies lies, green energy is black.
The Gray Area • 31 • : KrustyKrab -
Unidentified Flying Objects Over U.S. Military Bases in Northeast UK, as of roughly 11 a.m. CST.
Aliens and UFOs • 41 • : Skinnerbot -
Statements of Intent from Incoming Trump Administration Members - 2025 to 2029.
2024 Elections • 13 • : nugget1 -
Assad flees to moscow
World War Three • 47 • : ufoorbhunter -
Australia passes social media ban for children under 16
Social Issues and Civil Unrest • 24 • : PorkChop96 -
The Reactionary Conspiracy 13. The plot’s theology.
General Conspiracies • 321 • : andy06shake -
Jaguar Rebrand Video Causes "WTF?" Moment - Seriously Weird
Automotive Discussion • 41 • : Encia22