It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
Former Obama legal counsel Greg Craig expected to be indicted in Mueller case
www.washingtonexaminer.com... kneDSjN-PMDCVd260KxOoGstX-i5BrcM40
www.washingtonexaminer.com... kneDSjN-PMDCVd260KxOoGstX-i5BrcM40
a reply to: carewemust
I think the IG's FISA is more likely to exonerate him if they got all the 302's. If not then testimony from Peintka (sp).
I would prefer Muller exonerate him of any and all wrong doing by dropping charges. He shouldn't require a pardon.
I don't see him suing the gov, but I could be wrong.
Then POTUS needs to get him back in the administration asap.
I may be too ideological.
I think the IG's FISA is more likely to exonerate him if they got all the 302's. If not then testimony from Peintka (sp).
I would prefer Muller exonerate him of any and all wrong doing by dropping charges. He shouldn't require a pardon.
I don't see him suing the gov, but I could be wrong.
Then POTUS needs to get him back in the administration asap.
I may be too ideological.
originally posted by: cherokeetroy
Former Obama legal counsel Greg Craig expected to be indicted in Mueller case
www.washingtonexaminer.com... kneDSjN-PMDCVd260KxOoGstX-i5BrcM40
I thought no more indictments were forthcoming?
a reply to: liveandlearn
I'm sure Flynn will be exonerated, but with Mueller leaving government (again) in a few days, he can't drop the charge(s) against anyone can he?
General Flynn lost his house, savings, and I don't know what else. Maybe President Trump will sign an executive order to financially compensate all the people damaged by the ILLEGAL Mueller investigation.
I'm sure Flynn will be exonerated, but with Mueller leaving government (again) in a few days, he can't drop the charge(s) against anyone can he?
General Flynn lost his house, savings, and I don't know what else. Maybe President Trump will sign an executive order to financially compensate all the people damaged by the ILLEGAL Mueller investigation.
a reply to: carewemust
I think they still have the investigation Flynn is cooperating on, unless it has been completed and we don't know.
Could be why he is posting now.
Since Flynn's case hasn't been completed yet, someone will have to be there for the supposed sentencing.
That is my best guess.
And yes, he lost everything. Would love to see him compensated.
His biggest loss is his reputation amongst those who have no clue and will forever remember him for this charge only.
I think they still have the investigation Flynn is cooperating on, unless it has been completed and we don't know.
Could be why he is posting now.
Since Flynn's case hasn't been completed yet, someone will have to be there for the supposed sentencing.
That is my best guess.
And yes, he lost everything. Would love to see him compensated.
His biggest loss is his reputation amongst those who have no clue and will forever remember him for this charge only.
Remember this? Note the dates.
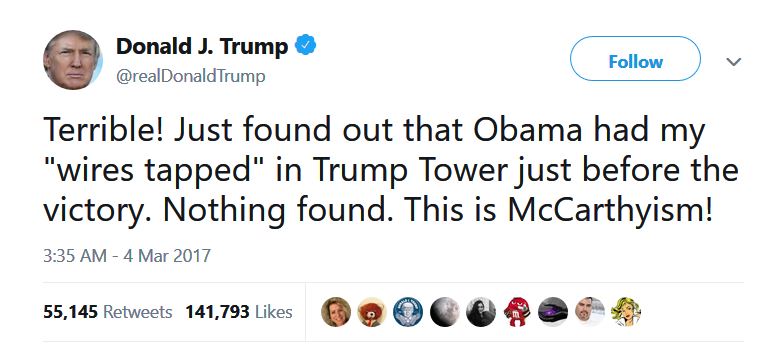
twitter.com...
Q2959

twitter.com...
Q2959
Mar 4 2019 15:39:34 (EST)
Hussein gave the order to start the spy campaign.
It was logged officially 2x.
1x - Domestic.
1x - Foreign.
FISC judge WH meeting?
WH visitor logs are important.
Hussein library CLAS doc move?
Attempt to shelter/protect?
Who has AUTH to obtain?
The More You Know.
Q
Is Amazon Spying on You with the Ring (DoorBot) Acquisition?
Q3305
Yes, yes they are.
the video feeds from its customers' homes in unencrypted format and allows staff around the world to have essentially unfettered access to these videos.
link
Also they are listening to everything you say:
Amazon Workers Are Listening to What You Tell Alexa
bloomburg
a reply to: pianopraze
My state is a "2-party" state where it's illegal to electronically intercept communications without all or "2" parties having knowledge.
I am intimately familiar with the mechanisms and case law regarding it, and I struggle to understand how it's legal for GOOG to intercept my conversations where I am unaware and expect privacy....?
en.wikipedia.org/wiki/Telephone_call_recording_laws#Two-party_consent_states
en.wikipedia.org...-party_consent_states
Wikipedia conflates and confuses the issue of "consent" as the standard for legally recording someone. That standard is the person simply having knowledge. Continuing to speak after you know you are recorded is a form of consent. (this saved my bacon more than once)
Also, Wiki mashing up the notions of eavesdropping with your own ears, which is legal, with illegal electronic interception....like Alexa.
en.wikipedia.org/wiki/Eavesdropping
en.wikipedia.org...
It's good to know the local laws. Generally 100% fine to video record anything in public, where there's no expectation of privacy. At the same time, the audio portion of the same recording can be criminal in a 2-party state.
My state is a "2-party" state where it's illegal to electronically intercept communications without all or "2" parties having knowledge.
I am intimately familiar with the mechanisms and case law regarding it, and I struggle to understand how it's legal for GOOG to intercept my conversations where I am unaware and expect privacy....?
en.wikipedia.org/wiki/Telephone_call_recording_laws#Two-party_consent_states
en.wikipedia.org...-party_consent_states
Wikipedia conflates and confuses the issue of "consent" as the standard for legally recording someone. That standard is the person simply having knowledge. Continuing to speak after you know you are recorded is a form of consent. (this saved my bacon more than once)
Also, Wiki mashing up the notions of eavesdropping with your own ears, which is legal, with illegal electronic interception....like Alexa.
en.wikipedia.org/wiki/Eavesdropping
en.wikipedia.org...
It's good to know the local laws. Generally 100% fine to video record anything in public, where there's no expectation of privacy. At the same time, the audio portion of the same recording can be criminal in a 2-party state.
edit on 11-4-2019 by FlyingFox because: "Round Her Up!"
a reply to: EndtheMadnessNow
Thankyou for showing the connection between those two communications. Q was exactly 2 years later.
Not coincidental.
Thankyou for showing the connection between those two communications. Q was exactly 2 years later.
Not coincidental.
FYI: "Pencil (neck) Act" filed by Congressman Matt Gaetz on Wednesday, to Remove Adam Schiff from the House Intel Committee and Revoke his Security
Clearance.
Source - Gaetz Tweet: twitter.com...
Source - Gaetz Tweet: twitter.com...
Thread by gortex
Julian Assange arrested at the Ecuadorian embassy in London.
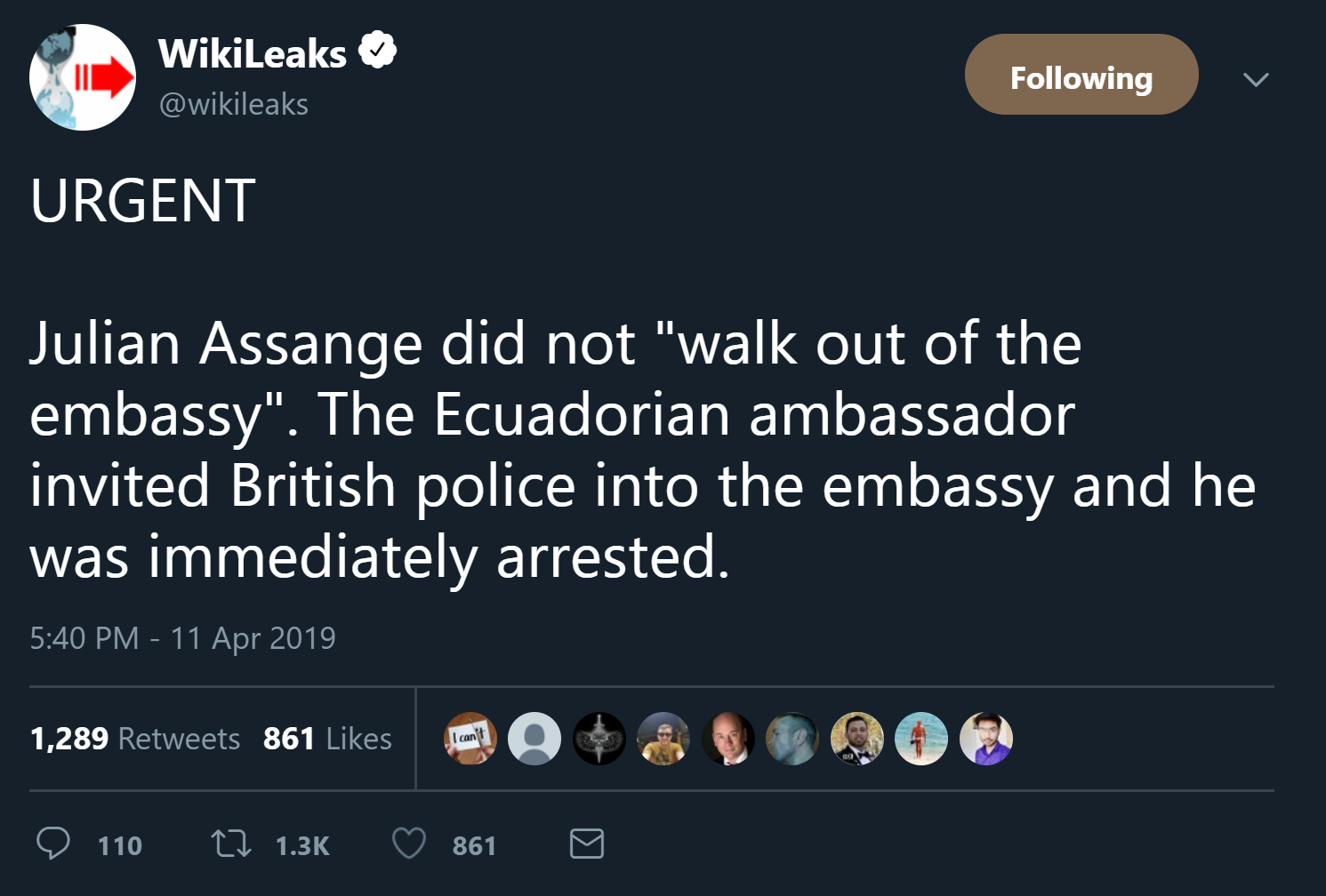
Live Updates (Guardian)
edit on 11-4-2019 by MindBodySpiritComplex because: (no reason given)
This is such bullschnip! Friggin Juggernauts treating him like he is an international terrorist! This makes me sick!
What is JA signalling?



Gore Vidal History of The National Security State: Includes Vidal on America



Gore Vidal History of The National Security State: Includes Vidal on America
published January 2014
In Gore Vidal: History of the National Security State & Vidal on America, TRNN Senior Editor Paul Jay and the acclaimed essayist, screenwriter and novelist Gore Vidal discuss the historical events that led to the establishment of the massive military-industrial-security complex and the political culture that gave us the “Imperial Presidency
edit on 11-4-2019 by MindBodySpiritComplex because: (no reason
given)
a reply to: pianopraze
Everything is listening, watching you, me and anyone participating in today's Tech society. It is almost as if Earth/civilization is being studied for reasons unknown or perhaps for full control of our lives.
Your car is watching you. Who owns the data?
Trading privacy for convenience, and then expecting others to protect you isn't working.
ETA - isn't all this interconnectivity just peachy ?
Mysterious safety-tampering malware infects a second critical infrastructure site
Everything is listening, watching you, me and anyone participating in today's Tech society. It is almost as if Earth/civilization is being studied for reasons unknown or perhaps for full control of our lives.
Your car is watching you. Who owns the data?
If you’re driving a late model car or truck, chances are that the vehicle is mostly computers on wheels, collecting and wirelessly transmitting vast quantities of data to the car manufacturer not just on vehicle performance but personal information, too, such as your weight, the restaurants you visit, your music tastes and places you go.
A car can generate about 25 gigabytes of data every hour and as much as 4,000 gigabytes a day, according to some estimates. The data trove in the hands of car makers could be worth as much as $750 billion by 2030, the consulting firm McKinsey has estimated. But consumer groups, aftermarket repair shops and privacy advocates say the data belongs to the car’s owners and the information should be subject to data privacy laws.
Yet Congress has yet to pass comprehensive federal data privacy legislation.
Trading privacy for convenience, and then expecting others to protect you isn't working.
ETA - isn't all this interconnectivity just peachy ?
Mysterious safety-tampering malware infects a second critical infrastructure site
Sixteen months ago, researchers reported an unsettling escalation in hacks targeting power plants, gas refineries, and other types of critical infrastructure. Attackers who may have been working on behalf of a nation caused an operational outage at a critical-infrastructure site after deliberately targeting a system that prevented health- and life-threatening accidents.
edit on 4112019 by MetalThunder because: (no reason
given)
a reply to: MindBodySpiritComplex
It is a code, but only a few know its meaning.
It could be stand down or it could be release the Kraken.
The next few days will tell.
Remember that a great many people have the file on their hard drive, only waiting for the crypto keys.
If this is the work of the Deep State then watch for return fire.
Q should have something to say in due time.
Thrusts and counter thrusts.
It would be really interesting if Q releases the keys, wouldn't it now.
Q will no doubt be monitoring the situation so waiting for the keys and then posting them would reach everybody.
Who's move is it next.
P
It is a code, but only a few know its meaning.
It could be stand down or it could be release the Kraken.
The next few days will tell.
Remember that a great many people have the file on their hard drive, only waiting for the crypto keys.
If this is the work of the Deep State then watch for return fire.
Q should have something to say in due time.
Thrusts and counter thrusts.
It would be really interesting if Q releases the keys, wouldn't it now.
Q will no doubt be monitoring the situation so waiting for the keys and then posting them would reach everybody.
Who's move is it next.
P
a reply to: carewemust
His charges are against the United States of America. I don’t think Mueller himself has to drop them.
His charges are against the United States of America. I don’t think Mueller himself has to drop them.
a reply to: RelSciHistItSufi
Over night the Q noi-se has moved to the arrest of Julian Assange from the Ecuadorian embassy in London..
I was resaerching South Korea tach stone coated steel roof tiles last night and missed it.
What are you hearing if anything in the UK about Assange?
Over night the Q noi-se has moved to the arrest of Julian Assange from the Ecuadorian embassy in London..
I was resaerching South Korea tach stone coated steel roof tiles last night and missed it.
What are you hearing if anything in the UK about Assange?
a reply to: pheonix358
I was thinking the same including the exact phrasing of "release the Kraken". The recent outage of FB and other social media, etc. followed by the NZ shooting, followed by the purge of the shooting video now definitely looks like it was a test run to intercept the kind of vids and other data Q has been teasing. I dare say the stage is #ing set!
It could be stand down or it could be release the Kraken.
I was thinking the same including the exact phrasing of "release the Kraken". The recent outage of FB and other social media, etc. followed by the NZ shooting, followed by the purge of the shooting video now definitely looks like it was a test run to intercept the kind of vids and other data Q has been teasing. I dare say the stage is #ing set!
new topics
-
12-21-24 Usyk-Fury II
World Sports: 1 hours ago -
Driving home for Christmas… fast!
General Entertainment: 5 hours ago -
My Retirement
General Chit Chat: 6 hours ago -
‘Something horrible’: Somerset pit reveals bronze age cannibalism
Ancient & Lost Civilizations: 7 hours ago -
Spiritual Solstice
Short Stories: 9 hours ago
top topics
-
My Retirement
General Chit Chat: 6 hours ago, 12 flags -
Spiritual Solstice
Short Stories: 9 hours ago, 5 flags -
‘Something horrible’: Somerset pit reveals bronze age cannibalism
Ancient & Lost Civilizations: 7 hours ago, 4 flags -
Driving home for Christmas… fast!
General Entertainment: 5 hours ago, 3 flags -
12-21-24 Usyk-Fury II
World Sports: 1 hours ago, 1 flags
active topics
-
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 7939 • : baddmove -
Have you noticed?? Post Election news coverage...
World War Three • 12 • : marg6043 -
'Mass Casualty event' - Attack at Christmas market in Germany
Mainstream News • 119 • : marg6043 -
12-21-24 Usyk-Fury II
World Sports • 1 • : onestonemonkey -
Spiritual Solstice
Short Stories • 5 • : JJproductions -
US Federal Funding set to Expire December 20th. Massive CR on the way.
Mainstream News • 72 • : marg6043 -
Salvatore Pais confirms science in MH370 videos are real during live stream
General Conspiracies • 247 • : Lazy88 -
My Retirement
General Chit Chat • 12 • : network dude -
Squirrels becoming predators
Fragile Earth • 37 • : Oldcarpy2 -
Mood Music Part VI
Music • 3754 • : SLAYER69