It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
originally posted by: SplinterSequence
a reply to: PokeyJoe
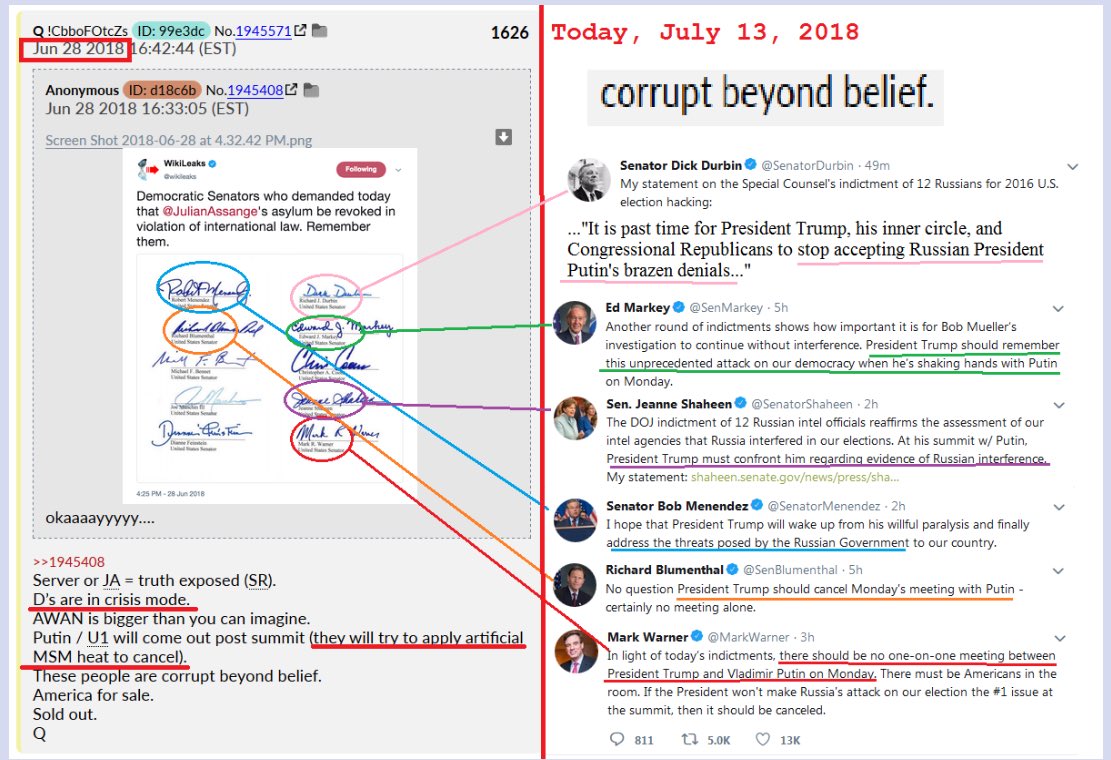
Keep in mind that the plan was hatched long before Trump became POTUS. Preventing the 16 year plan and reducing it to only 8 years is/was very dangerous and many patriots made the ultimate sacrifice to get us here. The true crimes of the past administration have not been made public yet. ⏲
You have to admit the Donald gave them fair notice, according to their own rules. That was a classic Simpsons episode. And he personally trademarked "Make America Great Again" in 2012. It isn't his fault they weren't paying attention.
originally posted by: Aallanon
a reply to: carewemust
It's for his own safety
So Paul Manafort is better connected than Michael Flynn..who's still free to roam?
originally posted by: SplinterSequence
originally posted by: carewemust
originally posted by: SplinterSequence
In case you did not noticed it. The new russian indictment allows all the "hacked" emails to be introduced as evidence in court. Podesta emails anyone? Enjoy the show. 🌊🌅
Can there be court proceedings with none of the defendants present? I don't see Putin sending them to our court, any more than we'd send our caught spies/hackers to court in any other country.
Remember what happened the last time Mueller indicted faceless russians? One of the accused actually showed up and proved Mueller wrong.
I remember. At least one of them was a ghost as well. Didn't exist. There's a lot of evidence pointing to Mueller buying time with periodic indictments, while something REALLY important is being worked on behind the scenes. Hopefully with Sessions, and Huber's team of Federal Prosecutors.
originally posted by: savagediver
a reply to: IAMTAT
I really am interested in what must be on jar jar binks computer that the capital police held onto that jar jar wanted back so bad. Was a really funny video of her threatening the capital police in a meeting trying to get it back. I am hoping awan sings loudly and clearly.
That was amusing af! I had seen a shorter clip of that a few times already. But, it was only yesterday that I saw a much longer one, that was not just closeups, making it seem like it was just in an office or something.
Seeing the full context of it being at some kind of community meeting with at least dozens of people, explains her weird languaging...it just drops into place when you realize she was attempting to pressure him using his peers/constituents/whatever. Before, I just thought she sounded desperatarded, or something.
a reply to: crankyoldman
The simple answer is you can't. I've got 4 computer degrees including 2 masters. Computer networks can be very complicated, made up of several servers performing different functions to something as simple a single server performing several functions. From what I can tell and I'm just surmising here, they were using the latter. That's what's missing. You need that machine to get at the log files which will give you everything you need to know. We do know that at a minimum Platt River was the provider for back up and recovery services for Hilliary's server. I have no idea who the DNC was using, if anybody. If their backup server was maintained in house that would be revealing. That would say to me there's two missing. Without the log files you got nothing.
The simple answer is you can't. I've got 4 computer degrees including 2 masters. Computer networks can be very complicated, made up of several servers performing different functions to something as simple a single server performing several functions. From what I can tell and I'm just surmising here, they were using the latter. That's what's missing. You need that machine to get at the log files which will give you everything you need to know. We do know that at a minimum Platt River was the provider for back up and recovery services for Hilliary's server. I have no idea who the DNC was using, if anybody. If their backup server was maintained in house that would be revealing. That would say to me there's two missing. Without the log files you got nothing.
It is now believed that many of the Schumann resonances transients (Q bursts) are related to the transient luminous events (TLEs). In 1995 Boccippio et al. showed that sprites, the most common TLE, are produced by positive cloud-to-ground lightning occurring in the stratiform region of a thunderstorm system, and are accompanied by Q-burst in the Schumann resonances band. Recent observations reveal that occurrences of sprites and Q bursts are highly correlated and Schumann resonances data can possibly be used to estimate the global occurrence rate of sprites.
en.wikipedia.org...
Transient Luminous Events:
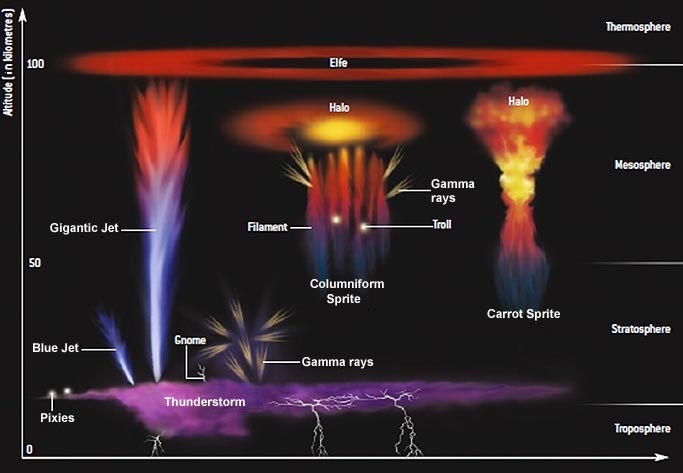
There are several types of TLEs, the most common being sprites. Sprites are flashes of bright red light that occur above storm systems. C-sprites (short for “columniform sprites”) is the name given to vertical columns of red light. C-sprites exhibiting tendrils are sometimes called “carrot sprites”. Other types of TLEs include sprite halos, blue jets, gigantic jets, blue starters, and ELVESs. The acronym ELVES (“Emission of Light and Very Low Frequency perturbations due to Electromagnetic Pulse Sources”) refers to a singular event which is commonly thought of as being plural. TLEs are secondary phenomena that occur in the upper atmosphere in association with underlying thunderstorm lightning.
en.wikipedia.org...
Remember the above acronym.
Lightning crashes a new mother cries
Her placenta falls to the floor
The angel opens her eyes
The confusion sets in
Before the doctor can even close the door
Lightning crashes an old mother dies
Her intentions fall to the floor
The angel closes her eyes
The confusion that was hers
Belongs now to the baby down the hall
Oh now feel it, comin' back again
Like a rollin', thunder chasing the wind
Forces pullin' from
The center of the earth again
I can feel it.
www.youtube.com...
“The singing Tesla coil, sometimes called a zeusaphone, thoramin or musical lightning, is a form of plasma speaker. It is a variation of a solid state Tesla coil that has been modified to produce musical tones by modulating its spark output. The resulting pitch is a low fidelity square wave like sound reminiscent of an analog synthesizer. The high-frequency signal acts in effect as a carrier wave; its frequency is significantly above human-audible sound frequencies, so that digital modulation can reproduce a recognizable pitch. The musical tone results directly from the passage of the spark through the air. The flexibility of the sound is limited by the fact that the solid-state coil produces square rather than sinusoidal waves; but simple chords are possible.”
A parallel exists between our brains and the "atmosphere."
More to come!!
edit on 13-7-2018 by eisegesis because: The Great Awakening
a reply to: Bill1960
Is the DNC server hardware needed in order to reach this determination?
Is the DNC server hardware needed in order to reach this determination?
Source: www.thegatewaypundit.com...
Deputy Attorney General Rod Rosenstein confirmed that the DNC server was never actually hacked.
Rather, the emails were obtained through a “spear phishing” email scam which THOUSANDS of others, including Republicans fell for.
BREAKING: Rosenstein just confirmed emails obtained through “spearfishing” email scam, which thousands of people including Republicans fell for. No wonder the DNC server was never examined by FBI. It was never actually hacked. This was a monumental lie by the Clinton campaign
Probably breaking ATS rules since I don’t know the source citing etiquette yet but thread number NINE!! *Dash* you are fantastic!*
Q has taken a break and it’s been a busy news week but I thought it important to share the way the Bible views the number (thread in this case) ‘9’
Maybe thread 9 symbolizes Qs Divine completeness and we will get some resolution and answers once this thread comes to the end.
Source:
www.biblestudy.org...
Q has taken a break and it’s been a busy news week but I thought it important to share the way the Bible views the number (thread in this case) ‘9’
...the number 9 symbolizes divine completeness or conveys the meaning of finality. Christ died at the 9th hour of the day, or 3 p.m., to make the way of salvation open to everyone.
Maybe thread 9 symbolizes Qs Divine completeness and we will get some resolution and answers once this thread comes to the end.
Source:
www.biblestudy.org...
Here's my opinion on our Russian "hackers" who were indicted today, One word sums it up BOLDERDASH. Real hackers leave signatures to prove it was
them, intelligence services don't. They don't want people to know they've been there. Yes in the news conference they did say they posing as hackers.
Why would you do that if you wanted to influence a country's election, you wouldn't. Cyber hacking by intelligence services by countries, including
our own is nothing new. Its done by teams of faceless technicians, If it's a government operation, NO WAY you're going to identify the specific
individuals involved. My guess the guys outed were the equivalent of our CIA station chiefs, every one of them who are known on both sides. They are
the public face of intelligence services.
originally posted by: carewemust
originally posted by: Pyle
originally posted by: carewemust
a reply to: Skyfloating
I'm still on the fence about Bob Mueller. Several lives have been ruined financially due to his investigation. And hopefully Paul manafort is not really in solitary confinement for cheating on his taxes 10 years ago.
He was on monitored release for tax crimes. He was put in jail for witness tampering. I know you know this because I have told you this before.
I understand JAIL...but Solitary Confinement is a BRUTAL OVERKILL! By that measure, Hillary, Comey, et al, should be burned at the stake.
Besides, as I've said before, there's no proof that Manafort "tampered" with any witnesses. Not one ATS member or so-called news organization has posted a legal document showing that Manafort tampered with a witness.
I agree that solitary confinment seems a bit extreme. I'm guessing that the solitary confinement is for his own protection. He'd be a sitting duck in general population.
I've noticed that you've taken a very active roll in trying to defend Manafort, and I'm having a hard time understanding why. I think the guy is as dirty as they come. There are certainly businessmen out there who operatin that ethical gray area, but are still in-bounds where the law is concerned. I don't think that's where Manifort played, though.
The witness tampering happened when he tried to make contact with witnesses in the case.
Warning: Link Below Opens a >PDF in Your Browser
UNITED STATES OF AMERICA
v.
PAUL J. MANAFORT, JR.,
Defendant.
Crim. No. 17-201-1 (ABJ)
The accusations of witness tampering are detailed starting on page 5-6. After page 6, it's a bunch of citations of case law justifying the actions taken by the prosecutor. They have all their bases covered.
The day after the Superseding Indictment was made public, Manafort also sent Person D1 a text message on an encrypted application, stating “This is paul.” Domin Decl. ¶ 14. 3 Two days later, on February 26, 2018, Manafort used the same encrypted application to send Person D1 a news article describing the Superseding Indictment’s allegations concerning the Hapsburg group, which included the statement that “two European politicians were secretly paid around €2 million by Manafort in order to ‘take positions favorable to Ukraine, including by lobbying in the United States.’”4One minute after sending the news article, Manafort wrote: “We should talk. I have made clear that they worked in Europe.” Domin Decl. ¶ 15. Toll records for one of Manafort’s phones indicate that Manafort had a short call with Person D1 on February 24, 2018, and that Manafort attempted to call Person D1 again on February 25 and 27, 2018. Id. ¶ 14. As noted in Special Agent Domin’s declaration, Person D1 has told the government that he understood Manafort’s outreach to be an effort to “suborn perjury,” because Person D1 knew that the Hapsburg group worked in the United States—not just Europe. Domin Decl. ¶ 19. In an effort to connect Manafort with Person D1, Person A reached out to Person D2, a longtime partner of Person D1. On February 28, five days after the Superseding Indictment, Person A attempted to contact Person D2 via an encrypted messaging application. Person A wrote: “My friend P is trying to reach [Person D1] to brief him on what’s going on.” Domin Decl. ¶ 17. Two minutes later, Person A added: “Basically P wants to give him a quick summary that he says to everybody (which is true) that our friends never lobbied in the US, and the purpose of the program was EU.” Id. Approximately five hours later, Person A switched to another encrypted application and sent a similar series of messages to Person D2, including a message relaying Manafort’s “summary” that the Hapsburg group never lobbied in the United States. Id.
If I recall correctly, the app used was the Signal app and all the witnesses were forced to hand over their phones as evidence.
edit on 13-7-2018 by CoramDeo because: Copy and paste from pdf mess hoefully better
Redacted.
Same post, two down.
Same post, two down.
edit on 13-7-2018 by CoramDeo because: (no reason given)
a reply to: carewemust
You certainly do. RR is talking out his keester. The networks you and I are most familiar with are Verizon, Comcast, Time-Warner etc. These are wide open networks. The DNC was supposed to be a closed network, safeguards would be in place to stop the little blue pill, Nigerian prince emails from ever getting there. If they didn't then their IT guys were morons. But lets assume they were and our targets clicked on it. If the idea was to suck down all the emails, and again that's ludacris a hacker is after BANK information when spear phishing. But lets assume they were targeting the emails and got access to that you still need the server logs to show the trail
You certainly do. RR is talking out his keester. The networks you and I are most familiar with are Verizon, Comcast, Time-Warner etc. These are wide open networks. The DNC was supposed to be a closed network, safeguards would be in place to stop the little blue pill, Nigerian prince emails from ever getting there. If they didn't then their IT guys were morons. But lets assume they were and our targets clicked on it. If the idea was to suck down all the emails, and again that's ludacris a hacker is after BANK information when spear phishing. But lets assume they were targeting the emails and got access to that you still need the server logs to show the trail
Can somebody correct me if this is wrong...
The "hacked" guccifer material discussed in these indictments is different and separate from material Wikileaks released just before the election?
Or is Wikileaks the "unnamed company" briefly mentioned that released some material sep 2016?
Dcleaks and guccifer are mentioned...not Wikileaks.
Pdf download of indictments:
www.justice.gov...
The "hacked" guccifer material discussed in these indictments is different and separate from material Wikileaks released just before the election?
Or is Wikileaks the "unnamed company" briefly mentioned that released some material sep 2016?
Dcleaks and guccifer are mentioned...not Wikileaks.
Pdf download of indictments:
www.justice.gov...
RR might as well be indicting telemarketers.
Also, in effect, there are multiple ways to validate email chains and custody of evidence. I assume there's an over abundance of evidence.
en.wikipedia.org...
en.wikipedia.org/wiki/Metadata
Also
Validating digital evidence for legal argument
ro.ecu.edu.au...
Also, in effect, there are multiple ways to validate email chains and custody of evidence. I assume there's an over abundance of evidence.
en.wikipedia.org...
en.wikipedia.org/wiki/Metadata
Metadata is "data [information] that provides information about other data".
[3] Descriptive metadata describes a resource for purposes such as discovery and identification. It can include elements such as title, abstract, author, and keywords.
[4]Structural metadata is metadata about containers of data and indicates how compound objects are put together, for example, how pages are ordered to form chapters. It describes the types, versions, relationships and other characteristics of digital materials.
[5] Administrative metadata provides information to help manage a resource, such as when and how it was created, file type and other technical information, and who can access it.
[6] Reference metadata describes the contents and quality of statistical data Statistical metadata may also describe processes that collect, process, or produce statistical data; such metadata are also called process data.
Also
Validating digital evidence for legal argument
ro.ecu.edu.au...
edit on 13-7-2018 by FlyingFox because: try again
a reply to: tiredoflooking
I believe Guccifer and Guccifer 2.0 are two different individuals.
The indictment specifically says the the conspiritors named in the indictment were collectively Guccifer 2.0 and that they set up layers of servers and fronts to funnel the information gathered out as if it was obtined by a single person, Guccifer 2.0.
My reading comprehension is sort of terrible, so anyone can correct me if they want.
No harm, no foul.
I believe Guccifer and Guccifer 2.0 are two different individuals.
The indictment specifically says the the conspiritors named in the indictment were collectively Guccifer 2.0 and that they set up layers of servers and fronts to funnel the information gathered out as if it was obtined by a single person, Guccifer 2.0.
43. Between in or around June 2016 and October 2016, the Conspirators used Guccifer 2.0 to release documents through WordPress that they had stolen from the DCCC and DNC. The Conspirators, posing as Guccifer 2.0, also shared stolen documents with certain individuals.
My reading comprehension is sort of terrible, so anyone can correct me if they want.
No harm, no foul.
edit on 13-7-2018 by CoramDeo because: Added Linky, added quote.
(Random thought of the Day)
Trump keeps using the term "Witch Hunt". Everyone thinks he is referring to the Russian Collusion case against him being a "witch hunt".
But maybe he is referring literally to his White House hunting witches.
Trump keeps using the term "Witch Hunt". Everyone thinks he is referring to the Russian Collusion case against him being a "witch hunt".
But maybe he is referring literally to his White House hunting witches.
originally posted by: tiredoflooking
a reply to: CoramDeo
I think that's right.
Why would Russia set up this elaborate network to get information...
Then leak it via an anon account?
Wouldn't they want to keep gathering information?
I think they got outed by the security team hired by the DNC, and shut down.
at least that is what is sounds like, happened.
32. Despite the Conspirators’ efforts to hide their activity, beginning in or around May 2016, both the DCCC and DNC became aware that they had been hacked and hired a security company (“Company 1”) to identify the extent of the intrusions. By in or around June 2016, Company 1 took steps to exclude intruders from the networks. Despite these efforts, a Linux-based version of X-Agent, programmed to communicate with the GRU-registered domain linuxkrnl.net, remained on the DNC network until in or around October 2016.
>>>
a. On or about June 20, 2016, after Company 1 had disabled X-Agent on the DCCC network, the Conspirators spent over seven hours unsuccessfully trying to connect to X-Agent. The Conspirators also tried to access the DCCC network using previously stolen credentials.
It seems like there is a missing piece of information, the payoff.
Payment for the efforts could be from money extorted to keep the information under wraps, or it could be at a goverment level where the political aims (no Hillary) are achieved.
The problem with this whole thing is the level of influence for the amount of effort.
To me, it seems that the release of the information had little to no effect on the outcome.
First, who in the course of the daily news cycle would even care about the interna machinations of a political campaign.
Second, very few would ever know the information as it wasn't really covered by the MSM.
Even if true, the whole thing is nothing more than a dog an pony show to justify the highly paid potted plants in the DOJ.
These guys will be convicted in absentia, and never be extradited, so who cares.
If anything, this seems like a distraction to point the finger away from SR being the source of the leaks.
I'm still not buying it.
There's nothing saying that there weren't two similar, parallel, independent security breaches with different politiacl motivations. The first being Guccifer 2.0 (russian hacking group) and the second being Bernie fan, SR.
new topics
-
House Passes Laken Riley Act
Mainstream News: 37 minutes ago -
The more I think about it
General Chit Chat: 1 hours ago -
What Comes After January 20th
Mainstream News: 3 hours ago -
Canada as a state .. how would it work?
General Chit Chat: 3 hours ago -
Those stupid GRAVITE commercials
Rant: 3 hours ago -
Let's Buy Greenland
General Chit Chat: 4 hours ago -
Planned Civil War In Britain May Be Triggered Soon
Social Issues and Civil Unrest: 7 hours ago -
Claim: General Mark Milley Approved Heat and Sound Directed Energy Weapons During 2020 Riots
Whistle Blowers and Leaked Documents: 9 hours ago
top topics
-
What Comes After January 20th
Mainstream News: 3 hours ago, 14 flags -
Claim: General Mark Milley Approved Heat and Sound Directed Energy Weapons During 2020 Riots
Whistle Blowers and Leaked Documents: 9 hours ago, 12 flags -
House Passes Laken Riley Act
Mainstream News: 37 minutes ago, 12 flags -
Planned Civil War In Britain May Be Triggered Soon
Social Issues and Civil Unrest: 7 hours ago, 6 flags -
Let's Buy Greenland
General Chit Chat: 4 hours ago, 5 flags -
Those stupid GRAVITE commercials
Rant: 3 hours ago, 4 flags -
Canada as a state .. how would it work?
General Chit Chat: 3 hours ago, 3 flags -
The more I think about it
General Chit Chat: 1 hours ago, 2 flags
active topics
-
House Passes Laken Riley Act
Mainstream News • 4 • : AdultMaleHumanUK -
What Comes After January 20th
Mainstream News • 18 • : lilzazz -
Greatest thing you ever got, or bought?
General Chit Chat • 26 • : Flyingclaydisk -
The more I think about it
General Chit Chat • 3 • : lilzazz -
ILLUMINATION: Dimensions / Degrees – Da Vincis Last Supper And The Philosophers Stone
Secret Societies • 14 • : CarlLaFong -
Canada as a state .. how would it work?
General Chit Chat • 10 • : YouSir -
The hunter has become the hunted
Politicians & People • 16 • : xuenchen -
Democrats Introduce Bill That Will Take Away Donald Trumps Secret Service Protection
2024 Elections • 78 • : fringeofthefringe -
-@TH3WH17ERABB17- -Q- ---TIME TO SHOW THE WORLD--- -Part- --44--
Dissecting Disinformation • 3959 • : Thoughtful3 -
Sorry to disappoint you but...
US Political Madness • 42 • : matafuchs