It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
a reply to: rickymouse
The Russians could easily have political operatives in the DNC. It is also very possible they have assets in the GOP. We have assets in theirs as well. Such action is a common part of intelligence gathering, as political intelligence is important to decision makers up the chain. Given the nature of intelligence missions, this information would not be leaked because it was certain to trigger tightened security/reprisals (therefore cutting off the flow of info - opposite of what intelligence agencies desire/spend lots of money on).
For this reason, even if the Russians had standard intelligence personnel in place (turned employee, mole, whatever the means) they wouldn't blow their cover over some potentially damaging data. It is far more likely a disgruntled insider wanted to deliver a blow against the DNC over a perceived sleight/personal vendetta of some kind, and conclusions from experts like Binney appear to support that assessment.
Just my take on it though rickymouse
The Russians could easily have political operatives in the DNC. It is also very possible they have assets in the GOP. We have assets in theirs as well. Such action is a common part of intelligence gathering, as political intelligence is important to decision makers up the chain. Given the nature of intelligence missions, this information would not be leaked because it was certain to trigger tightened security/reprisals (therefore cutting off the flow of info - opposite of what intelligence agencies desire/spend lots of money on).
For this reason, even if the Russians had standard intelligence personnel in place (turned employee, mole, whatever the means) they wouldn't blow their cover over some potentially damaging data. It is far more likely a disgruntled insider wanted to deliver a blow against the DNC over a perceived sleight/personal vendetta of some kind, and conclusions from experts like Binney appear to support that assessment.
Just my take on it though rickymouse
I'd like to know how the "Forensicator" knew the file meta-data he used in his analysis was representative of what would have been found if the files
had been examined on the confirmed disk of the original destination device.. you know, since he never had access to that. He had access to a zip file
uploaded to the internet, assembled in God knows what manner or in how many steps, across how many machines.
I'd also like to know where Binny got his numbers, if not from the same place.
Unless he knows who the hacker is and actually has THAT GUY's machine/device at his disposal.
I'd also like to know where Binny got his numbers, if not from the same place.
Unless he knows who the hacker is and actually has THAT GUY's machine/device at his disposal.
Does this sort of nonsense really keep the base from tuning out?
You guys might want to pace yourselves.
You guys might want to pace yourselves.
originally posted by: JBurns
a reply to: rickymouse
The Russians could easily have political operatives in the DNC. It is also very possible they have assets in the GOP. We have assets in theirs as well. Such action is a common part of intelligence gathering, as political intelligence is important to decision makers up the chain. Given the nature of intelligence missions, this information would not be leaked because it was certain to trigger tightened security/reprisals (therefore cutting off the flow of info - opposite of what intelligence agencies desire/spend lots of money on).
For this reason, even if the Russians had standard intelligence personnel in place (turned employee, mole, whatever the means) they wouldn't blow their cover over some potentially damaging data. It is far more likely a disgruntled insider wanted to deliver a blow against the DNC over a perceived sleight/personal vendetta of some kind, and conclusions from experts like Binney appear to support that assessment.
Just my take on it though rickymouse
A disgruntled insider(s) like the Aswan family?
a reply to: JBurns
Yes, they did. Dug up here:
Cyber Firm Rewrites Part of Disputed Russian Hacking Report
Did they? I will see if I can dig that up from anywhere!
Yes, they did. Dug up here:
On Thursday, CrowdStrike walked back key parts of its Ukraine report.
The company removed language that said Ukraine's artillery lost 80 percent of the Soviet-era D-30 howitzers, which used aiming software that purportedly was hacked. Instead, the revised report cites figures of 15 to 20 percent losses in combat operations, attributing the figures to IISS.
The original CrowdStrike report was dated Dec. 22, 2016, and the updated report was dated March 23, 2017.
Cyber Firm Rewrites Part of Disputed Russian Hacking Report
a reply to: jadedANDcynical
This thread is filled with disinformation. That has nothing to do with the CrowdStrike work for the DNC, it's about an app that was being used by Ukrainian artillery units.
This thread is filled with disinformation. That has nothing to do with the CrowdStrike work for the DNC, it's about an app that was being used by Ukrainian artillery units.
a reply to: theantediluvian
Did the above emphasized excerpt not occur?
After CrowdStrike released its Ukraine report, company co-founder Dmitri Alperovitch claimed it provided added evidence of Russian election interference. In both hacks, he said, the company found malware used by "Fancy Bear," a group with ties to Russian intelligence agencies.
Did the above emphasized excerpt not occur?
a reply to: theantediluvian
Since you skipped over the OP and zeroed in on replies instead, would you mind debunking Binney's analysis since you're clearly convinced otherwise?
I'm assuming you've seen evidence proving this Russian connection right?
Since you skipped over the OP and zeroed in on replies instead, would you mind debunking Binney's analysis since you're clearly convinced otherwise?
I'm assuming you've seen evidence proving this Russian connection right?
originally posted by: jadedANDcynical
a reply to: Dudemo5
What you're not getting is the analysis done by the Forensicator is confirmed by Binny's statements.
There are two separate and unconnected entities (the Forensicator and Binny) that have come to the same conclusion.
The analysis by "The Forensicator" is bunk. First off, it has nothing to do with the DNC, a point that keeps being missed by people running around talking about it like it's the holy grail.
The files in the archive he looked at was released via torrent on or about Sept 13. They were files from the DCCC — from the DCCC hack. If you look at it again real quick, you'll notice that the mod times are all 2016-07-05 (6-7 weeks after the CrowdStrike announcement).
Most importantly, the theoretical transfer, assuming that's what is evidenced, could have happened anywhere:
* it could have occurred between two computers at the DCCC prior to the final archive being exfiltrated.
* it could have occurred between two computers on the hacker's own network.
* it could also have occurred between two interim boxes in between or even between the DCCC box and an interim destination.
You see this?
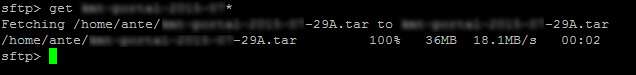
That's a transfer I did earlier today between a VPS in Houston, TX and another in Windsor, Ontario at a different ISP. I regularly get ~20MB/s between them.
a reply to: jadedANDcynical
That's not what was claimed though was it? What was claimed was that CrowdStrike walked back attribution in the DNC hack. That did not occur.
That's not what was claimed though was it? What was claimed was that CrowdStrike walked back attribution in the DNC hack. That did not occur.
a reply to: theantediluvian
No one is doubting the transfer speeds can be done over a reasonably fast WAN connection. The problem is that such activity would throw up major red flags to IPDS systems and security guys keeping an eye on those systems. There is a good likelihood that would've caused them to lose their access, which is a primary goal of an alleged APT: "persistence"
Why not break into smaller chunks and transmit more slowly to avoid detection? Wouldn't you want to maintain access?
Binney is no quack - he is widely respected in his field, and should be taken seriously.
Why is the conclusion of an insider job so difficult for you to consider? It appears to challenge some deeply held world view or something. If it were me, I wouldn't put too many chips on the table if you're betting for this Russia stuff to ever be actually proven.
All we have so far is innuendo, suggestion, accusation and summary judgment supporting that belief.
One piece of substantial evidence is all it would take.... ?
No one is doubting the transfer speeds can be done over a reasonably fast WAN connection. The problem is that such activity would throw up major red flags to IPDS systems and security guys keeping an eye on those systems. There is a good likelihood that would've caused them to lose their access, which is a primary goal of an alleged APT: "persistence"
Why not break into smaller chunks and transmit more slowly to avoid detection? Wouldn't you want to maintain access?
Binney is no quack - he is widely respected in his field, and should be taken seriously.
Why is the conclusion of an insider job so difficult for you to consider? It appears to challenge some deeply held world view or something. If it were me, I wouldn't put too many chips on the table if you're betting for this Russia stuff to ever be actually proven.
All we have so far is innuendo, suggestion, accusation and summary judgment supporting that belief.
One piece of substantial evidence is all it would take.... ?
originally posted by: JBurns
a reply to: theantediluvian
No one is doubting the transfer speeds can be done over a reasonably fast WAN connection. The problem is that such activity would throw up major red flags to IPDS systems and security guys keeping an eye on those systems. There is a good likelihood that would've caused them to lose their access, which is a primary goal of an alleged APT: "persistence"
Why not break into smaller chunks and transmit more slowly to avoid detection? Wouldn't you want to maintain access?
Binney is no quack - he is widely respected in his field, and should be taken seriously.
Why is the conclusion of an insider job so difficult for you to consider? It appears to challenge some deeply held world view or something. If it were me, I wouldn't put too many chips on the table if you're betting for this Russia stuff to ever be actually proven.
All we have so far is innuendo, suggestion, accusation and summary judgment supporting that belief.
One piece of substantial evidence is all it would take.... ?
Can't rule out inter-system transfer on the same network (would not trip IPDS), then transfer to a USB stick. Manually walked out by an insider (i.e. Aswan).
a reply to: Krakatoa
That is an extremely valid and good point Krakatoa
I wholly believe it was an inside job, exfil'd via USB. My suspicion is that Seth Rich may have been part of that effort, although I admit I have no evidence to prove that. It is just a belief, based on timing. However, I believe an analysis of the timeline regarding both matters could shed some light on a few questions. Aswan or really anyone else could have been responsible though as far as I know
That is an extremely valid and good point Krakatoa
I wholly believe it was an inside job, exfil'd via USB. My suspicion is that Seth Rich may have been part of that effort, although I admit I have no evidence to prove that. It is just a belief, based on timing. However, I believe an analysis of the timeline regarding both matters could shed some light on a few questions. Aswan or really anyone else could have been responsible though as far as I know
edit on 11/9/2017 by JBurns because:
(no reason given)
new topics
-
tweeting nasty words worse than child porn according to judges and the Labour party
Mainstream News: 20 minutes ago -
The Why Files does Alien Implants
Aliens and UFOs: 1 hours ago -
Democrats Oversee Big Surge In Cop Murder
Social Issues and Civil Unrest: 2 hours ago -
The "Hundredth Monkey" Effect and the Modern Western "Agenda"
New World Order: 2 hours ago -
Sen. Johnson Asks the CDC How Many Americans Were Killed by COVID Shots
Science & Technology: 4 hours ago -
I just looked around and he's gone
Music: 7 hours ago -
1 and 2 Kings
Religion, Faith, And Theology: 11 hours ago -
Gender identity
Rant: 11 hours ago
top topics
-
Suspect in attempted assassination of Trump traveled to Ukraine in Apr 22 called for bombing Moscow
US Political Madness: 12 hours ago, 13 flags -
Sen. Johnson Asks the CDC How Many Americans Were Killed by COVID Shots
Science & Technology: 4 hours ago, 12 flags -
Democrat Leader Hakeem Jeffries Promotes HATE After 2nd Attempt to Murder Trump in 2024.
US Political Madness: 12 hours ago, 10 flags -
Gender identity
Rant: 11 hours ago, 9 flags -
tweeting nasty words worse than child porn according to judges and the Labour party
Mainstream News: 20 minutes ago, 8 flags -
Democrats Oversee Big Surge In Cop Murder
Social Issues and Civil Unrest: 2 hours ago, 7 flags -
The Why Files does Alien Implants
Aliens and UFOs: 1 hours ago, 6 flags -
I just looked around and he's gone
Music: 7 hours ago, 4 flags -
The "Hundredth Monkey" Effect and the Modern Western "Agenda"
New World Order: 2 hours ago, 1 flags -
1 and 2 Kings
Religion, Faith, And Theology: 11 hours ago, 0 flags
active topics
-
They are setting up the steal y’all
2024 Elections • 41 • : Justoneman -
tweeting nasty words worse than child porn according to judges and the Labour party
Mainstream News • 10 • : SecretKnowledge2 -
The "Hundredth Monkey" Effect and the Modern Western "Agenda"
New World Order • 11 • : onestonemonkey -
Springfield Ohio Preacher "It's Worse than the media says" Haitian was allowed to buy a gun
General Conspiracies • 28 • : bluesman023 -
Another attempt on Trump?
2024 Elections • 295 • : wAnchorofCarp -
Sen. Johnson Asks the CDC How Many Americans Were Killed by COVID Shots
Science & Technology • 7 • : Tolkien -
I just looked around and he's gone
Music • 1 • : baddmove -
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 7544 • : baddmove -
Democrat Leader Hakeem Jeffries Promotes HATE After 2nd Attempt to Murder Trump in 2024.
US Political Madness • 18 • : xuenchen -
The Why Files does Alien Implants
Aliens and UFOs • 2 • : SprocketUK
