It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
IT'S...........................Montey Python's Flying Ciiiiir--cuuus! the lost episodes, i betchya.
Do you want to know EU spooks' latest claim of a backdoor in IBM ClearMake?
a reply to: theultimatebelgianjoke
You really need to start a new thread for these. I had missed the new additions.
Thank you for bringing these forward!
You really need to start a new thread for these. I had missed the new additions.
Thank you for bringing these forward!
After Vault 7 ... Vault 8 !
Source : WIKILEAKS /Vault8
Just a mention about the alphabet agencies obsession of Russian-framing in their first publication 'Hive' :
Source : WIKILEAKS /Vault8
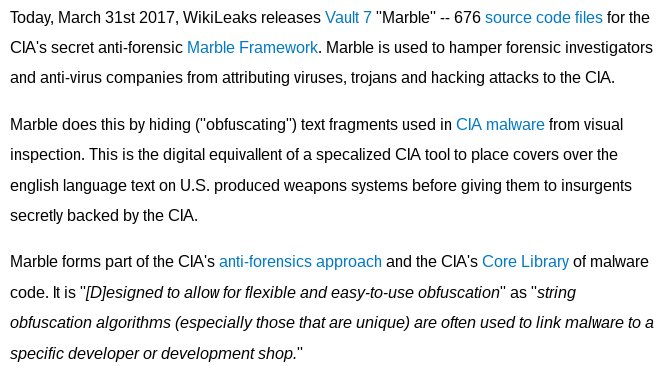
A collection of source code repositories from CIA software projects described in the Vault7 series.
WikiLeaks is publishing only source code that does not contain 0-days or any other form of exploits, so it can not be weaponized by others to inflict harm - it only details the software development of the CIA regarding its middle-ware and back-end systems.
The publication of this source code will enable security analysts and forensic experts to better identify, analyze and counter-measure covert CIA infrastructure components.
Just a mention about the alphabet agencies obsession of Russian-framing in their first publication 'Hive' :
But Hive uses the uncommon Optional Client Authentication so that the user browsing the website is not required to authenticate - it is optional. But implants talking to Hive do authenticate themselves and can therefore be detected by the Blot server. Traffic from implants is send to an implant operator management gateway called Honeycomb while all other traffic go to a cover server that delivers the unsuspicious content for all other users.
Certificates for the authentication of implants are generated by a the CIA with fake names. The examples included in the source code builds a certificate for Kaspersky Laboratory, Moscow signed by Thawte Premium Server CA, Cape Town.
new topics
-
Paramilitary Leaks - John Williams
Whistle Blowers and Leaked Documents: 6 hours ago -
Some sausage, some chicken, some sauce, some onions and some garlic...and some peppers!
Food and Cooking: 7 hours ago -
Hearing more ambulances lately
Medical Issues & Conspiracies: 8 hours ago -
Los Angeles brush fires latest: 2 blazes threaten structures, prompt evacuations
Mainstream News: 8 hours ago -
House Passes Laken Riley Act
Mainstream News: 8 hours ago -
The more I think about it
General Chit Chat: 9 hours ago -
What Comes After January 20th
Mainstream News: 11 hours ago -
Canada as a state .. how would it work?
General Chit Chat: 11 hours ago
top topics
-
House Passes Laken Riley Act
Mainstream News: 8 hours ago, 23 flags -
What Comes After January 20th
Mainstream News: 11 hours ago, 18 flags -
Claim: General Mark Milley Approved Heat and Sound Directed Energy Weapons During 2020 Riots
Whistle Blowers and Leaked Documents: 17 hours ago, 12 flags -
Planned Civil War In Britain May Be Triggered Soon
Social Issues and Civil Unrest: 16 hours ago, 7 flags -
Let's Buy Greenland
General Chit Chat: 13 hours ago, 6 flags -
Los Angeles brush fires latest: 2 blazes threaten structures, prompt evacuations
Mainstream News: 8 hours ago, 6 flags -
Those stupid GRAVITE commercials
Rant: 12 hours ago, 5 flags -
Hearing more ambulances lately
Medical Issues & Conspiracies: 8 hours ago, 5 flags -
The more I think about it
General Chit Chat: 9 hours ago, 4 flags -
Canada as a state .. how would it work?
General Chit Chat: 11 hours ago, 4 flags
active topics
-
Planned Civil War In Britain May Be Triggered Soon
Social Issues and Civil Unrest • 16 • : Freeborn -
Los Angeles brush fires latest: 2 blazes threaten structures, prompt evacuations
Mainstream News • 12 • : Mantiss2021 -
Judge rules president-elect Donald Trump must be sentenced in 'hush money' trial
US Political Madness • 60 • : WeMustCare -
Inca stone masonry at Sacsayhuaman, Ollantaytambo and the Sun Temple
Ancient & Lost Civilizations • 23 • : Hansllune -
Paradox of Progress
Ancient & Lost Civilizations • 14 • : Hansllune -
Let's talk planes.
General Chit Chat • 10 • : Dalamax -
Paramilitary Leaks - John Williams
Whistle Blowers and Leaked Documents • 8 • : caterpillage -
Claim: General Mark Milley Approved Heat and Sound Directed Energy Weapons During 2020 Riots
Whistle Blowers and Leaked Documents • 25 • : NoCorruptionAllowed -
Meta Llama local AI system is scary good
Science & Technology • 47 • : glend -
House Passes Laken Riley Act
Mainstream News • 15 • : KrustyKrab