It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:

Concerned about the militarization of law enforcement, a source within the intelligence community has provided The Intercept with a secret, internal U.S. government catalogue of dozens of cellphone surveillance devices used by the military and by intelligence agencies. Some of the devices are already in use by federal law enforcement and local police forces domestically, and civil liberties advocates believe others will eventually find their way into use inside the U.S. This product catalogue provides rare insight into the current spy capabilities of local law enforcement and offers a preview of the future of mass surveillance of mobile communications.
Source
Most would consider their cellphone invaluable, especially during a crisis. All this equipment enables them to spy on you, prevent usage and assist in draining your battery. Your cellphone is helping them get to know you at all times.
Something to note:
The product descriptions contained in this catalogue were taken verbatim from the text of the original government documents and may include typos and other errors
Let paranoia spring from the ground and shower us in fear!! If you have nothing to hide, you're too boring and sheepish. Regardless, stay out of my ever-so-dwindling private life!
I'll post a few examples below. On to the main course...
Government Cellphone Surveillance Catalogue
Among the 53 items are the now-familiar Stingray I/II surveillance boxes. They're billed as the "dragnet surveillance workhorse [that] has been deployed for years by numerous local law enforcement agencies across the United States." It has a range of 200 meters and sells for $134,000. A chief selling point is the "ready-made non-disclosure agreements from the FBI and Harris Corp. [that] will provide a pretext for concealing these features from the public." The listing also touts Harris' "next-generation Hailstorm, a must-have for cracking the 4G LTE network."
Not surprisingly, the NSA is listed as the vendor of one device, while another was designed and used by the CIA. A third was built for the Special Forces.

The Intercept did a great breakdown...
A few of the devices can house a “target list” of as many as 10,000 unique phone identifiers. Most can be used to geolocate people, but the documents indicate that some have more advanced capabilities, like eavesdropping on calls and spying on SMS messages. Two systems, apparently designed for use on captured phones, are touted as having the ability to extract media files, address books, and notes, and one can retrieve deleted text messages.
Above all, the catalogue represents a trove of details on surveillance devices developed for military and intelligence purposes but increasingly used by law enforcement agencies to spy on people and convict them of crimes. The mass shooting earlier this month in San Bernardino, California, which President Barack Obama has called “an act of terrorism,” prompted calls for state and local police forces to beef up their counterterrorism capabilities, a process that has historically involved adapting military technologies to civilian use. Meanwhile, civil liberties advocates and others are increasingly alarmed about how cellphone surveillance devices are used domestically and have called for a more open and informed debate about the trade-off between security and privacy—despite a virtual blackout by the federal government on any information about the specific capabilities of the gear.
“We’ve seen a trend in the years since 9/11 to bring sophisticated surveillance technologies that were originally designed for military use—like Stingrays or drones or biometrics—back home to the United States,” said Jennifer Lynch, a senior staff attorney at the Electronic Frontier Foundation, which has waged a legal battle challenging the use of cellphone surveillance devices domestically. “But using these technologies for domestic law enforcement purposes raises a host of issues that are different from a military context.”
Even though some of us are aware of this technology, it doesn't hurt to spread the awareness. Our privacy is an illusion and their denial is a bold faced lie. A number of cities have been actively upgrading their spy gear to deal with newer 4G LTE phones. This train isn't slowing down anytime soon.
Cities scramble to upgrade “stingray” tracking as end of 2G network looms
The FBI is doesn’t want anyone sticking their nose where it doesn't belong, FYI.
If you’ve ever filed a public records request with your local police department to learn more about how cell-site simulators are used in your community—chances are good that the FBI knows about it. And the FBI will attempt to “prevent disclosure” of such information.
In 2012, a letter was furnished by the FBI and sent to the Minnesota Bureau of Criminal Apprehension. Definitely a quick way to get noticed if you ask me. The letter states,
In the event that the Minnesota Bureau of Criminal Apprehension receives a request pursuant to the Freedom of Information Act (5 USC 552) or an equivalent state or local law, the civil or criminal discovery process, or other judicial, legislative, or administrative process, to disclose information concerning the Harris Corporation [REDACTED] the Minnesota Bureau of Criminal Apprehension will immediately notify the FBI of any such request telephonically and in writing in order to allow sufficient time for the FBI to seek to prevent disclosure through appropriate channels.
Previously, a privacy activist named Mike Katz submitted public records requests to the 100 largest local law enforcement agencies in the country. Only one responded and it was a record of Tacoma police notifying the FBI after requests were made by an Associated Press reporter.
Tacoma's response: Link
Oddly, Obama has made an effort to reduce the amount of military gear used by local law enforcement. This equipment is too easily abused and should only be used for extremely specific purposes. Some think otherwise...
Trott Leads Effort To Stand Against Obama Administration’s Weakening of Local Police Departments
In a letter, sent to President Obama from Rep. Dave Trott (MI-11), Rep. Candice Miller (MI-10), Rep. Mike Bishop (MI-08), Rep. John Moolenaar (MI-04), Bill Huizenga (MI-02), and Fred Upton (MI-06), the lawmakers urged the administration to rescind its plan to recall vehicles under the 1033 Program, which allows the transfer of excess military equipment to civilian law enforcement agencies.
Never let a tragedy go to waste! Militarizing our police force while systematically removing guns from law abiding citizens. See the irony people? The agenda is clear, total monitoring and tracking of a helpless society. They are fine tuning their predictive models for future engagement.
Smile...
They're watching you!
edit on 19-12-2015 by eisegesis because: (no reason given)
a reply to: eisegesis
The best are the reviews from these devices.
e.g. This one
Really gross stuff these devices!
S/F
Link
The best are the reviews from these devices.
e.g. This one
Review by Jennifer Lynch Senior Staff Attorney, Electronic Frontier Foundation Are you trying to monitor a huge political protest? Look no further than DRT. Nicknamed “dirt boxes,” these devices can locate up to 10,000 targets and can process multiple analog and digital wireless devices all at the same time. They’re even capable of intercepting and recording digital voice data. The best thing about the devices is the fact that no one may ever know you’ve used one. Just be careful — if your targets do figure out you’ve used a DRT box, and you haven’t gotten a warrant, they may be able to convince a judge to throw out all the evidence you’ve collected on them after you used the device. You can mount DRT models like this one in an aircraft to fly over the crowd.
Really gross stuff these devices!
S/F
Link
edit on 19/12/15 by D0MiNAT0R 1OOO because: (no reason given)
edit on 19/12/15 by D0MiNAT0R 1OOO because: (no reason
given)
edit on 19/12/15 by D0MiNAT0R 1OOO because: (no reason given)
Nicknamed “dirt boxes,” these devices can locate up to 10,000 targets and can process multiple analog and digital wireless devices all at the same time. They’re even capable of intercepting and recording digital voice data.
Yeah...and with all this technology they still can't catch the Isis murderers. Probably the devices are vulnerable to sand
edit on
20-12-2015 by WhiteHat because: (no reason given)
a reply to: D0MiNAT0R 1OOO
Yes, the reviews are very disheartening. They're so tongue-in-cheek about exploiting our privacy it makes me sick. The revelation about this leaked catalog is that a third of these devices have never been seen or heard of by the general public. Some devices and their usage have been previously discussed and scrutinized, but the limit to their capabilities is as expected, something we only have partial knowledge of.
Yes, the reviews are very disheartening. They're so tongue-in-cheek about exploiting our privacy it makes me sick. The revelation about this leaked catalog is that a third of these devices have never been seen or heard of by the general public. Some devices and their usage have been previously discussed and scrutinized, but the limit to their capabilities is as expected, something we only have partial knowledge of.
edit on 20-12-2015 by eisegesis because: (no reason given)
I looked through the entire catalog and thought we have
to audit these F'er's.
This outrageously priced garbage has one purpose
and that is to watch listen and locate US citizens.
One lousy black box and laptop is $365,000.
What a waste of money. What could the cost of one
Artemis do for our vets who have not been able to adjust to civilian life ?
Where are their funds ? Fellow soldiers who are homeless lost hungry drug dependent and
receiving ZERO help. I for one have had it with the MIC
and it's contractors. It's OUR money.
to audit these F'er's.
This outrageously priced garbage has one purpose
and that is to watch listen and locate US citizens.
One lousy black box and laptop is $365,000.
What a waste of money. What could the cost of one
Artemis do for our vets who have not been able to adjust to civilian life ?
Where are their funds ? Fellow soldiers who are homeless lost hungry drug dependent and
receiving ZERO help. I for one have had it with the MIC
and it's contractors. It's OUR money.
What bothers me is that if *I* got my hands on/built something like this and used it to tear down a small bit of institutionalized crime (police
force, judicial system, banking system, religion, any given branch of gooberment) not only would the evidence be destroyed, but I'd be made out to be
a terrorist and spend life in prison, or worse.
They use it on me to see what my plans for lunch today are, and nobody bats an eye.
People are so busy looking at the double standards between various classes of citizen these days, nobody even notices what's going on. It wont be long before they have a running list of exactly which citizens will or will not put up with a given level of their bull#, and be able to identify them in a crowd by the devices we all carry.
They probably already have a running list of which citizens are likely to leave the country for each one of our insane presidential "choices"- Honestly they're all such terrible options I have to wonder if they were picked out of a hat and this is just some sick gameshow for those up top.
Every day they pass new laws aimed at selectively weeding out members of society that are less likely to condone their plans for the following year. Every year the actions of disgruntled citizens and power hungry law enforcement gets a little more out of hand- Every year the government gets just a little bit more insane.
They're squeezing us in their hands, like sand- but doing it slowly so only those they don't want to hold onto slip through their fingers... but they're accelerating their pace, and it's causing problems.
Should be a good show watching it all come falling down. Such a bummer- we had so much potential.
They use it on me to see what my plans for lunch today are, and nobody bats an eye.
People are so busy looking at the double standards between various classes of citizen these days, nobody even notices what's going on. It wont be long before they have a running list of exactly which citizens will or will not put up with a given level of their bull#, and be able to identify them in a crowd by the devices we all carry.
They probably already have a running list of which citizens are likely to leave the country for each one of our insane presidential "choices"- Honestly they're all such terrible options I have to wonder if they were picked out of a hat and this is just some sick gameshow for those up top.
Every day they pass new laws aimed at selectively weeding out members of society that are less likely to condone their plans for the following year. Every year the actions of disgruntled citizens and power hungry law enforcement gets a little more out of hand- Every year the government gets just a little bit more insane.
They're squeezing us in their hands, like sand- but doing it slowly so only those they don't want to hold onto slip through their fingers... but they're accelerating their pace, and it's causing problems.
Should be a good show watching it all come falling down. Such a bummer- we had so much potential.
Yipe! We need a NSFW-MIC/MIL label. I'd hate to have pulled this up at work and it been noticed you had a S/NF screenshot on there.
I don't think you have a grasp of engineering economics. Or design. Or SDR.
The design of this stuff requires a huge amount of engineering labor, which is expensive. You also don't have a lot of sales. It's not like PC motherboards or something. You're amortizing a huge number of design hours over a very small production run. The total production count for any one model is probably an hour's run of a single motherboard model by Foxconn.
There's also hell's own support issues. Remember, you're talking about giving a cop a receiver that you'd normally have, say, an Echo running in an Army environment. The cop has not only got cursory training, most of them aren't, let's say, chosen for field law enforcement due to their technical aptitude.
On top of which, you've got a huge product liability coverage and an entire legal team dedicated to stomping fires on it in court.
I'm not surprised at the price at all. The bigger brother (technology wise) of this stuff, in terms of design principles, is still classified. Although it's one of those things that's "obvious to one skilled in the art". It's just damned hard to do.
eta: eisegesis, I actually knew Scotty back when he first got started. Like his second week in the biz. One big MF.
I looked through the entire catalog and thought we have
to audit these F'er's.
This outrageously priced garbage has one purpose
and that is to watch listen and locate US citizens.
One lousy black box and laptop is $365,000.
What a waste of money.
I don't think you have a grasp of engineering economics. Or design. Or SDR.
The design of this stuff requires a huge amount of engineering labor, which is expensive. You also don't have a lot of sales. It's not like PC motherboards or something. You're amortizing a huge number of design hours over a very small production run. The total production count for any one model is probably an hour's run of a single motherboard model by Foxconn.
There's also hell's own support issues. Remember, you're talking about giving a cop a receiver that you'd normally have, say, an Echo running in an Army environment. The cop has not only got cursory training, most of them aren't, let's say, chosen for field law enforcement due to their technical aptitude.
On top of which, you've got a huge product liability coverage and an entire legal team dedicated to stomping fires on it in court.
I'm not surprised at the price at all. The bigger brother (technology wise) of this stuff, in terms of design principles, is still classified. Although it's one of those things that's "obvious to one skilled in the art". It's just damned hard to do.
eta: eisegesis, I actually knew Scotty back when he first got started. Like his second week in the biz. One big MF.
edit on 20-12-2015 by
Bedlam because: (no reason given)
originally posted by: eisegesis
This bad dude is not cheap with around 700k to 800k, so have fun buying it hehe... This is pretty much useless in the states but is priceless in places with few cel towers to locate the bad guy.
Edits due to oops of wrong pic
edit on 20-12-2015 by Xtrozero because: (no reason given)
originally posted by: Xtrozero
originally posted by: eisegesis
This bad dude is not cheap with around 700k to 800k, so have fun buying it hehe... This is pretty much useless in the states but is priceless in places with few cel towers to locate the bad guy.
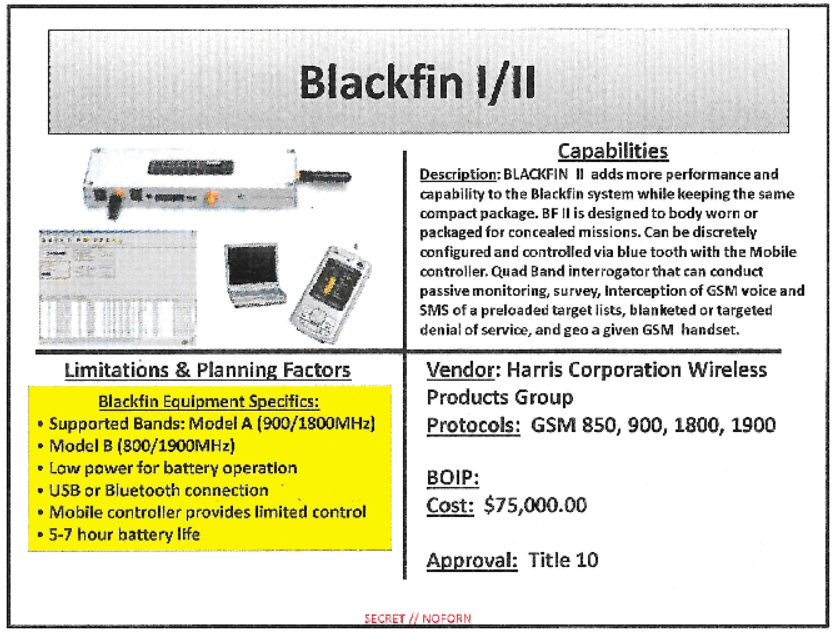
BF2 is relatively cheap...only $75k! What a bargain!
Of course, you could cobble one together, but you're going to have to learn SDR (a LOT of calculus, hold onto yor ass!), radio design, RF layout, and the entire technical data collection for cell phone communication, top to bottom. I'd say if you have a science degree of some sort, it ought not take you more than 5 years of backbreaking labor.
originally posted by: Bedlam
BF2 is relatively cheap...only $75k! What a bargain!
Of course, you could cobble one together, but you're going to have to learn SDR (a LOT of calculus, hold onto yor ass!), radio design, RF layout, and the entire technical data collection for cell phone communication, top to bottom. I'd say if you have a science degree of some sort, it ought not take you more than 5 years of backbreaking labor.
That is the point..when there are only 8 in the world then crappy cheap components wrapped around TS stuff it can cost a hell of a lot.
originally posted by: Xtrozero
That is the point..when there are only 8 in the world then crappy cheap components wrapped around TS stuff it can cost a hell of a lot.
We've sold many a PMC form factor card for $10k or so, they're about the size of a dollar bill, and they're a plug in card. Not even a case.
Because the military wanted a particular function, and it had some really tight specs, and we had to do part tracking, and on a short time frame.
Not to mention, even if you only sell a dozen, you've still got to do FCC testing, emission testing, HALT/HASS testing, RF susceptibility testing and so on, and all that costs huge amounts of money, not only for the test lab, but also for dedicated engineering resources and equipment.
Then you build 20. And you have to amortize ALL that crap over 20 boards.
a reply to: Bedlam
I've just notified your employer and instructed them to blacklist ATS, shame on you.
Let's see...
I have two questions if you've got answers.
How much of this technology do you think is or becoming obsolete? Different regions of the globe are advancing at different paces, I'm sure they could find a use for what the US considers "old", in other parts of the world.
In your opinion, what is the scariest thing in this catalog and have any vendors surprised you as the makers of any of these devices?
PS - I'm actually taller than Scotty, certainly not as big. That guy could pick his teeth with a chair leg.
This is for you. It starts at :20...
"This man is so mean his own mother hates him, I don't even like to look at him!...but I'm not in this for what I like, I'm in it for bucks." LOL
I've just notified your employer and instructed them to blacklist ATS, shame on you.
Let's see...
I have two questions if you've got answers.
How much of this technology do you think is or becoming obsolete? Different regions of the globe are advancing at different paces, I'm sure they could find a use for what the US considers "old", in other parts of the world.
In your opinion, what is the scariest thing in this catalog and have any vendors surprised you as the makers of any of these devices?
PS - I'm actually taller than Scotty, certainly not as big. That guy could pick his teeth with a chair leg.
This is for you. It starts at :20...
"This man is so mean his own mother hates him, I don't even like to look at him!...but I'm not in this for what I like, I'm in it for bucks." LOL
originally posted by: eisegesis
a reply to: Bedlam
How much of this technology do you think is or becoming obsolete? Different regions of the globe are advancing at different paces, I'm sure they could find a use for what the US considers "old", in other parts of the world.
In your opinion, what is the scariest thing in this catalog and have any vendors surprised you as the makers of any of these devices?
Most of the world uses GSM exclusively. So, "old" boxes for US use aren't likely to be usable elsewhere. Here, you'd want a box that could do CDMA, LTE and GSM. It's sort of more hodge-podgey here.
I've actually posted here peripherally and in sort of a dodgy way about this stuff for years. I'm familiar with the boxes used by Special Forces and the agency. The cop-only ones I haven't had any experience with. Harris is typical for making this sort of thing. There are a few other vendors who can pull the trick off for other comm systems. Like military comm systems. You can do the same sort of deal with other folks' versions of VINSON, SINCGARS et al. And the SF has quite similar boxes to these that can do it. I'm sure the agency has some that are nearly identical.
Even if you can't break the encryption in real-time, you can use some of the SDR tricks to locate boxes that are doing spread spectrum and whose users think they are being all cagey and secretive.
PS - I'm actually taller than Scotty, certainly not as big. That guy could pick his teeth with a chair leg.
"This man is so mean his own mother hates him, I don't even like to look at him!...but I'm not in this for what I like, I'm in it for bucks." LOL
Oddly enough, his debut wasn't in Memphis as they say. I came home on leave for a big stretch, visited a brother in Jackson, MS. And they were doing a practice show in the Mississippi Coliseum for a MidSouth show, which was Grizzly Smith's promotion.
They had a habit of doing a live run on the Saturday show on Wednesday. It was the last practice, I'd suppose, of that week's performance. They ran it mid afternoon on Wednesday, so they didn't get a big crowd. And oddly enough, the Saturday show would be EXACTLY like the Wednesday one, with room for the occasional improv and the bugs removed. I had run into a couple of the guys who also worked Georgia Championship at the time, since there's jack all to do in Columbus GA when you're stuck at Benning and we had got into the habit of dropping into the shows there and stirring up the crowd for fun, and had ended up meeting a few of the guys.
So we were bored, dropped into the Wednesday live practice session, said hi to the two guys and started chumming the crowd, which was maybe 100 or so. I didn't watch the matches all that much, it's a lot more fun getting the rednecks stirred, and if you do it right, the show promoter likes it. So Terry told the promotion guys we were ok, and off we went.
I can't tell you who was even there other than Terry, with two exceptions, there was a shoot in the middle of one match that was about half a minute long that was brutal, when Jim Duggan, who is as blind as a bat, punched George Gray square in the mouth instead of missing. George pulled up, wiped a bunch of blood off his mouth where he had a few nice lacs from his teeth, looked at Jim, then walked over, picked him up, looked outside and found a sawhorse, then dropped Duggan about six feet onto the sawhorse. Ow.
The other one was "Sam Houston" which was Grizzly's kid who was useless as a performer, and he was in the ring with this guy I'd never seen. And man, was he good. At first I thought it was just going to be a big oaf character, but holy crap could he move. It was sort of parkour. I'd never seen a guy that big do the crap he was doing. And he was improvising a lot of it on the fly. It was obvious he was supposed to be the heel, so of course we started cheering for him to pop the crowd. Instead of ignoring us, it threw him off. He couldn't see us because the house lights were down and the ring spot was on, but he kept breaking off and coming to the side and looking for us. Being the practice run, he had more leeway to drop character I suppose. By the end he was screaming back "Why da # are you cheering ME? I'm the damned BAD GUY! Are you makin' fun a ME?" which was just a hoot.
This guy could even sell Mike Smith, which is just amazing considering how bad he was. Eventually "Sam" beat the new guy.
That's when the fun started. Scotty had seen us with Terry during the harassment phase, so after he went to the showers and got back in street clothes, he asked Terry what the deal was, then went to the end of the bleacher, up to the top, over to where we were, then came down from behind us and plopped his 375 pound butt down right in the middle of us. THUMP. "Ok, which ones a yas are the smartasses cheering the bad guy?"
Alas, he wouldn't KEEP selling Mike, so Griz cut him loose. And that's the rest of the story.
edit on 20-12-2015 by Bedlam because: (no reason
given)
originally posted by: Xtrozero
originally posted by: Bedlam
Then you build 20. And you have to amortize ALL that crap over 20 boards.
A lot of engineers in places like China Lake that all gets bundled into the final cost.
A lot of purchases, they can't include engineering as a line item. So you roll it all in and divide by number of boards as purchase cost.
Another fun thing is, the aerospace guys have to get quotes on it and rebid your stuff to the purchaser, so we get an off-record call to set the specification from the purchaser, who then informs NG, Boeing and LM that there is a sole vendor for the item. They all call us and find out the price, then they all bid it with whatever markups they can get. But all the bids are us.
originally posted by: Bedlam
originally posted by: Xtrozero
originally posted by: Bedlam
Then you build 20. And you have to amortize ALL that crap over 20 boards.
A lot of engineers in places like China Lake that all gets bundled into the final cost.
A lot of purchases, they can't include engineering as a line item. So you roll it all in and divide by number of boards as purchase cost.
Another fun thing is, the aerospace guys have to get quotes on it and rebid your stuff to the purchaser, so we get an off-record call to set the specification from the purchaser, who then informs NG, Boeing and LM that there is a sole vendor for the item. They all call us and find out the price, then they all bid it with whatever markups they can get. But all the bids are us.
Yep Yep
a reply to: Bedlam
Thanks for the reply and cool story.
From a civilian standpoint, is there anyway to know if you're connecting to a fake carrier signal before breaking any encryption? Is there any identifier or I dare even ask, an app (rooted or not), that can tell me if I'm getting ciphered?
Are they mostly successful in remaining undetected when stealing our data because of our ignorance to the subject or because the systems are designed to be spoofed? How does the actual signal provider company not notice?
U.S., Israeli companies supply spy gear to repressive regimes, report says
The unstoppable rise of the global surveillance profiteers
Link
In my opinion, these devices are being pushed and purposefully go unregulated until someone blows the whistle. We are sitting ducks. I thought you might enjoy this part of the article as well. Sorry for the wall-o-text.
These devices are never going away. Now what can we as civilians do to fight back? I know...how about sit in a box all day!
This signal-blocking Faraday cage might drive you crazy

Thanks for the reply and cool story.
Even if you can't break the encryption in real-time, you can use some of the SDR tricks to locate boxes that are doing spread spectrum and whose users think they are being all cagey and secretive.
From a civilian standpoint, is there anyway to know if you're connecting to a fake carrier signal before breaking any encryption? Is there any identifier or I dare even ask, an app (rooted or not), that can tell me if I'm getting ciphered?
Are they mostly successful in remaining undetected when stealing our data because of our ignorance to the subject or because the systems are designed to be spoofed? How does the actual signal provider company not notice?
U.S., Israeli companies supply spy gear to repressive regimes, report says
U.S. and Israeli companies are supplying sophisticated surveillance technology to Central Asian nations with records of widespread human rights abuses, giving state security services virtually unchecked power to monitor the communications of ordinary citizens, according to a new report by Privacy International.
Researchers for the watchdog group, based in London, allege that the spy gear sold by these companies is key to the functioning of police states that smother the exercise of free speech, political dissent and other basic rights, while helping authoritarian governments maintain their grip on power.
The unstoppable rise of the global surveillance profiteers
“The systems we are talking about are getting smaller, faster and cheaper every day,” Schaake told the Kernel. “Technologies that are sold as law enforcement tools can easily be abused in countries where the rule of law is not upheld, and where journalists, human rights defenders, opposition politicians, and ordinary citizens are attacked by their governments through these tools.”
Link
In my opinion, these devices are being pushed and purposefully go unregulated until someone blows the whistle. We are sitting ducks. I thought you might enjoy this part of the article as well. Sorry for the wall-o-text.
The Wiretapper’s Ball
Like any major industry, the companies in the business of selling surveillance technology have conferences. Those trade shows, which are held a few times a years in locations like Mexico and Dubai are called ISS World, more commonly known as the “Wiretapper’s Ball.”
ISS World gives everyone involved in the government surveillance business, from the vendors of surveillance technology to the government intelligence agents themselves, the chance to talk shop. The list of talks the conference held in Kuala Lumpur, Malaysia, earlier this year include:
How to intercept wireless communications on 3G, 4G and LTE networks mobile networks
How to carry out remote stealth surveillance on encrypted traffic networks
How to use encryption to avoid remote stealth surveillance
How to use facial recognition technology and gathering metadata on images posted on Facebook
How to defend your networks against zero-day attacks—meaning, ones exploiting previously unknown holes in digital security systems
From what public accounts do exist, the events themselves seem like profoundly weird experiences.
A Bloomberg News report about an ISS World conference in Kuala Lumpur in 2011 noted that, unlike almost every other business conference in existence, there are no cocktail parties. Attendees try to avoid even being seen talking congregating with each other in public. That kind of socialization isn’t encouraged when the stated profession of nearly everyone in attendance is stealing secrets and the events are potential recruiting grounds for double agents.
At a previous iteration of the conference in Prague, one telecom regulator from an African government looked up from his tablet to see the action being displayed on his monitor also being projected on a screen at the front of the room in real time. He had logged the hotel’s wireless Internet and someone had quickly hacked his system to teach him an important lesson about what happens when one is insufficiently paranoid in a room packed with spies.
ISS World’s organizer, a Virginia-based company called TeleStrategies, is notoriously secretive. It doesn’t allow journalists into its conventions and, when contacted by the Kernel, a representative said the company has a policy of not granting interviews with the press.
The software is constantly updated to avoid firewalls and antivirus programs because what’s untraceable today may be easily defended against tomorrow.
However, the organization has apparently let in representatives from Sudan, Iran, and Syria—nations whose repressive governments have earned them a place on the list of countries sanctioned by the U.S. government. According to a report by independent researcher Colin Anderson, TeleStratagies requires that attendees register under the umbrella of larger, pre-screened organizations.
“In the case of Sudan, TeleStrategies has indicated knowledge of the participant’s nationality through its disclosed attendance records,” Anderson wrote. “Six of the listings are entities of the Government of Sudan, and three of which, recorded as ‘Governmental LEA,’ ‘Sudan Ministry of Interior,’ and ‘Sudan National Telecommunication Authority’, are directly cited within the State Department’s Human Rights Reports as parties in the country’s online and offline human rights abuses.”
For their part, the conference’s organizers say they do what they can to block representatives from some of the world’s most notorious governments from attending. Other than that, as TeleStratagies President Jerry Lucas charges, ethical concerns are “not our responsibility.”
It’s a sentiment echoed by Hacking Team spokesman Eric Rabe. He insists that, outside of building and helping set up the technology, his company plays no part in whatever investigations its governmental customers decide to carry out. “I don’t think you want Hacking Team to be the universal arbiter of what countries are good and what countries are bad,” he noted. “That’s why we rely on blacklists; that’s why we rely on governments to help us.”
In one sense, that shirking of moral responsibility is a dodge. But in another, it’s hard logic to argue with. If governments don’t set up clear rules about the sale of these technologies, there’s going to be nothing stopping companies from selling whatever they want to the highest bidder—even if the intentions of that highest bidder are less than honorable.
These devices are never going away. Now what can we as civilians do to fight back? I know...how about sit in a box all day!
This signal-blocking Faraday cage might drive you crazy

edit on 20-12-2015 by eisegesis because: (no reason given)
new topics
-
To become president, Zelensky had to learn Ukrainian
Political Conspiracies: 1 hours ago -
Green Grapes
General Chit Chat: 5 hours ago -
Those Great Fresh Pet Commercials
Television: 10 hours ago
top topics
-
Joe meant what he said about Hunter's pardon....
US Political Madness: 14 hours ago, 12 flags -
S.C. Jack Smith's Final Report Says Trump Leads a Major Conspiratorial Criminal Organization!.
Political Conspiracies: 12 hours ago, 11 flags -
Advice for any young Adult .
General Chit Chat: 13 hours ago, 10 flags -
Green Grapes
General Chit Chat: 5 hours ago, 5 flags -
It’s Falling…
Philosophy and Metaphysics: 16 hours ago, 4 flags -
Regent Street in #London has been evacuated due to a “bomb threat.”
Other Current Events: 14 hours ago, 3 flags -
Those Great Fresh Pet Commercials
Television: 10 hours ago, 3 flags -
To become president, Zelensky had to learn Ukrainian
Political Conspiracies: 1 hours ago, 3 flags
active topics
-
To become president, Zelensky had to learn Ukrainian
Political Conspiracies • 1 • : berbofthegreen -
Los Angeles brush fires latest: 2 blazes threaten structures, prompt evacuations
Mainstream News • 115 • : WeMustCare -
What Comes After January 20th
Mainstream News • 34 • : charlest2 -
Some sausage, some chicken, some sauce, some onions and some garlic...and some peppers!
Food and Cooking • 4 • : putnam6 -
S.C. Jack Smith's Final Report Says Trump Leads a Major Conspiratorial Criminal Organization!.
Political Conspiracies • 42 • : WeMustCare -
House Passes Laken Riley Act
Mainstream News • 22 • : KrustyKrab -
Russia Ukraine Update Thread - part 3
World War Three • 6904 • : Imhere -
Steering the Titantic from the Drydock.
Rant • 43 • : charlest2 -
President Carter has passed
Mainstream News • 44 • : WeMustCare -
Those stupid GRAVITE commercials
Rant • 13 • : GENERAL EYES
