It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
13
share:
Hi all,
Just wanting to discuss the tools I use for online privacy and anonymity on Mac OS Mavericks and iOS. Whether this is helpful for you, or you have some tips for me and others, please chip in
Note - please only discuss ways to legally be anonymous, so we don't have ATS T&C issues. Also note, that while these tools are legal, that may vary depending on your local laws and how you use them.
Also, all my options are FREE and easy to use, but many offer premium services also.
Browsers
Tor Browser (Also on Windows and iOS. iOS version is called 'Onion Browser' and costs money)
is widely regarded as the best browser for online anonymity, despite recently discovered flaws. Essentially a modded Firefox, it includes the extensions HTTPS Everywhere and No Script. The Tor Project generally recommends not to use other extensions, as their security is often unverified and can create a security hole in the browser. This is the primary reason why Flash is disabled by default in the browser; there are workarounds, but that ultimately defeats the purpose of using Tor. There is often discussion as to whether you should use Tor or VPN, but in my experience they are not mutually exclusive and can be used together.
Firefox is probably the favorite browser for most Mac users. Along with the aforementioned HTTPS Everywhere and No Script plugins available, there are also other great extensions. Do Not Track Me (in the process of becoming known as Blur) blocks trackers, provides the option to make a 'masked email' (a 'fake' email address which is setup to forward to your actual address) when giving your email to mailing lists for example and a similar option for passwords: giving a password recommendation for when you are creating passwords. Ghostery is also primarily about blocking tracking cookies, and may be even easier to setup. And no, I don't know why the logo looks similar to Snapchat's. Better Privacy blocks a different type of cookie, known as 'super cookies' or 'flash cookies' each time you finish your browser session. These cookies are not addressed by Ghostery or Do Not Track Me. Disconnect is an interesting tool, as it functions similar to a VPN. It offers secure browsing, location control and lets you visualize your trackers. I run all of these add-on (and more) simultaneously without any conflict.
(Disconnect is also available on iOS and so is Ghostery (as a browser app) and Blur (Do Not Track Me as primarily a browser app that can be synced with your Mac version).
Safari: Apples built-in browser is probably the last resort if you still want anonymity. Ghostery and Do Not Track Me are, however, still available for it.
And don't forget the built-in Private Browsing functions to protect your surfing history from loved ones (and vice versa)
VPNs
TunnelBear, SurfEasy and GoVPN are the VPNs I use on both my Mac and iOS device (the free options anyway). They are all quite simple and self explanatory to set up and have an amount of free data that resets each month. They mostly have options to increase that data by inviting friends to download, sharing the account over multiple devices or sharing via Twitter/Facebook. I may have had some trouble with the GoVPN profile on iOS (it was likely something else that was blocking my internet access), but simply uninstalling and reinstalling the profile over wifi solved it. Keep in mind, that when you meet your quota, you will not be able to connect to the internet, you will have to turn off the VPN first, and that is the main reason I use multiple VPNs - for more usage.
Tails
Tails is an anonymity and privacy based Linux operating system that sends its data over the Tor network. You can create an external HD, thumb drive or DVD and boot the operating system onto another PC and run it from there. It does absolutely nothing to the host PC apparently 'leaving no trace'. Unfortunately I couldn't get past the install menu on my Mac using refind, but there is a chance that I did something wrong (I'm only new at multi bootingy, BIOSy business). It did run smoothly using VirtualBox, but that does give a warning that any privacy of the virtualized OS would be useless if someone was able to penetrate the host OS.
What are your thoughts on these? Would you do things different? If so, let me know what options you guys take.
Cheers
Just wanting to discuss the tools I use for online privacy and anonymity on Mac OS Mavericks and iOS. Whether this is helpful for you, or you have some tips for me and others, please chip in
Note - please only discuss ways to legally be anonymous, so we don't have ATS T&C issues. Also note, that while these tools are legal, that may vary depending on your local laws and how you use them.
Also, all my options are FREE and easy to use, but many offer premium services also.
Browsers
Tor Browser (Also on Windows and iOS. iOS version is called 'Onion Browser' and costs money)
is widely regarded as the best browser for online anonymity, despite recently discovered flaws. Essentially a modded Firefox, it includes the extensions HTTPS Everywhere and No Script. The Tor Project generally recommends not to use other extensions, as their security is often unverified and can create a security hole in the browser. This is the primary reason why Flash is disabled by default in the browser; there are workarounds, but that ultimately defeats the purpose of using Tor. There is often discussion as to whether you should use Tor or VPN, but in my experience they are not mutually exclusive and can be used together.
Firefox is probably the favorite browser for most Mac users. Along with the aforementioned HTTPS Everywhere and No Script plugins available, there are also other great extensions. Do Not Track Me (in the process of becoming known as Blur) blocks trackers, provides the option to make a 'masked email' (a 'fake' email address which is setup to forward to your actual address) when giving your email to mailing lists for example and a similar option for passwords: giving a password recommendation for when you are creating passwords. Ghostery is also primarily about blocking tracking cookies, and may be even easier to setup. And no, I don't know why the logo looks similar to Snapchat's. Better Privacy blocks a different type of cookie, known as 'super cookies' or 'flash cookies' each time you finish your browser session. These cookies are not addressed by Ghostery or Do Not Track Me. Disconnect is an interesting tool, as it functions similar to a VPN. It offers secure browsing, location control and lets you visualize your trackers. I run all of these add-on (and more) simultaneously without any conflict.
(Disconnect is also available on iOS and so is Ghostery (as a browser app) and Blur (Do Not Track Me as primarily a browser app that can be synced with your Mac version).
Safari: Apples built-in browser is probably the last resort if you still want anonymity. Ghostery and Do Not Track Me are, however, still available for it.
And don't forget the built-in Private Browsing functions to protect your surfing history from loved ones (and vice versa)
VPNs
TunnelBear, SurfEasy and GoVPN are the VPNs I use on both my Mac and iOS device (the free options anyway). They are all quite simple and self explanatory to set up and have an amount of free data that resets each month. They mostly have options to increase that data by inviting friends to download, sharing the account over multiple devices or sharing via Twitter/Facebook. I may have had some trouble with the GoVPN profile on iOS (it was likely something else that was blocking my internet access), but simply uninstalling and reinstalling the profile over wifi solved it. Keep in mind, that when you meet your quota, you will not be able to connect to the internet, you will have to turn off the VPN first, and that is the main reason I use multiple VPNs - for more usage.
Tails
Tails is an anonymity and privacy based Linux operating system that sends its data over the Tor network. You can create an external HD, thumb drive or DVD and boot the operating system onto another PC and run it from there. It does absolutely nothing to the host PC apparently 'leaving no trace'. Unfortunately I couldn't get past the install menu on my Mac using refind, but there is a chance that I did something wrong (I'm only new at multi bootingy, BIOSy business). It did run smoothly using VirtualBox, but that does give a warning that any privacy of the virtualized OS would be useless if someone was able to penetrate the host OS.
What are your thoughts on these? Would you do things different? If so, let me know what options you guys take.
Cheers
edit on 19/11/2014 by BombDefined because: (no reason given)
a reply to: BombDefined
None Really,
beyond common sense.
I mean, I wouldn't trust my personal
information to some "cloud".
Unless God and the Angels were gleaming
upon it.
None Really,
beyond common sense.
I mean, I wouldn't trust my personal
information to some "cloud".
Unless God and the Angels were gleaming
upon it.
I don't do anything online that anyone else would find of any real use.
If someone wants to waste their time spying on me or trying to steal anything of any use, let'em waste their time.
If someone wants to waste their time spying on me or trying to steal anything of any use, let'em waste their time.
a reply to: BombDefined
Subscribed - I'll have a reel of data for you in the morning. Apologies for being short.
Common sense is key though; to throw two cents before I depart
Subscribed - I'll have a reel of data for you in the morning. Apologies for being short.
Common sense is key though; to throw two cents before I depart
My computer as well as my Internet traffic are locked down. Posting on ATS is enough to get you "watched". I'm not saying any conspiracy about ATS
itself I am simply saying that if you were to express a lot of suspicion about things in the government or politics here on ATS its free for the whole
world to read. ATS itself may not collaborate with these entities but they don't require collaboration to watch you, your Internet traffic, your
email, keep going...
All of which came out in the news recently. A couple of years ago I decided I didn't really want to be on those lists. So I have since then taken steps to secure my data and my Internet traffic. I would recommend if you keep private data such as a journal (I do) on your PC to add Truecrypt to your list of programs. Its just like if you were a kid and your parents read your journal. You may not have done anything but its no ones business what you think about in your own head.
However they are taking steps to find that out too. Anyhow good topic.
All of which came out in the news recently. A couple of years ago I decided I didn't really want to be on those lists. So I have since then taken steps to secure my data and my Internet traffic. I would recommend if you keep private data such as a journal (I do) on your PC to add Truecrypt to your list of programs. Its just like if you were a kid and your parents read your journal. You may not have done anything but its no ones business what you think about in your own head.
However they are taking steps to find that out too. Anyhow good topic.
edit on 20-11-2014 by Pimpintology because: of fluoride!
I usually go here www.grc.com... and see what vulnerabilities I have, then take steps to fix it. I use Disconnect,
AdblockPlus, BHODemon and Advanced System Care Ultimate. On the web page, go to Freeware, pick what you want from the drop down menu and go from
there.
originally posted by: BombDefined
Note - please only discuss ways to legally be anonymous, so we don't have ATS T&C issues ... No Script ... Ghostery ...
If you read the T&Cs of this forum, (20b), I think you'll find that posts which tell readers about anything which blocks adverts will be removed from this forum.
edit on 20-11-2014 by engvbany because: (no reason given)
originally posted by: skunkape23
I don't do anything online that anyone else would find of any real use ...
Really ? , have a look at this ... donttrack.us...
a reply to: engvbany
Good point.
20b does say that you can't use ad-blocking on ATS as part of the usage agreement. NoScript lets you whitelist trusted sites, so not against T&C is you don't use it here.
Also, my understanding of things like Ghostery, was that it stopped trackers from providing targeted advertisements, rather than simply blocking them.
Good point.
20b does say that you can't use ad-blocking on ATS as part of the usage agreement. NoScript lets you whitelist trusted sites, so not against T&C is you don't use it here.
Also, my understanding of things like Ghostery, was that it stopped trackers from providing targeted advertisements, rather than simply blocking them.
An easy way to get rid of Flash cookies (Local Shared Objects, or LS0's) on a Windows computer is to create a batch file that deletes them whenever
you execute it. The batch file & a short discussion of LSO's are here.
Once the file is saved to your HD, place a shortcut to it on your desktop; when you're done surfing, all you need to do is to double-click the
shortcut icon, and all LSO's from that surfing session go bye-bye.
This works on WINXP & WIN7; it will probably work on WIN8 if the locations of the LSO's haven't been changed (they're stored in 2 directories - see the text of the batch file for names/parent directories). I would think that if you can search out the location of LSO's on other OS's, the batch file should be able to be modified to work on them as well.
This works on WINXP & WIN7; it will probably work on WIN8 if the locations of the LSO's haven't been changed (they're stored in 2 directories - see the text of the batch file for names/parent directories). I would think that if you can search out the location of LSO's on other OS's, the batch file should be able to be modified to work on them as well.
a reply to: BombDefined
I have been trying ixquick.com for a search engine. I was going to do the email with them but honestly I am not paying people for something others offer for free. I am not entirely happy with the search engine part of it. I am a little nervous that it is itself a data collection scam.
I liked the Samaru search engine that ATS endorsed, but to be fair, google does it SOOO much better.
as far as VPNs I just rotate them every month if I am in need. I dont really bother anymore. What ever I find that day.
I download TONS of music and film. I just choose wisely when choosing a torrent. I can smell the ones that are being tracked fairly well.
I bank on common sense with technology. I dont even use anti virus. That really says it all. I just choose wisely what I search, how I word it, where I go, even what links I click. I wont even click on links in threads if I smell something fishy. So far so good.
I have been trying ixquick.com for a search engine. I was going to do the email with them but honestly I am not paying people for something others offer for free. I am not entirely happy with the search engine part of it. I am a little nervous that it is itself a data collection scam.
I liked the Samaru search engine that ATS endorsed, but to be fair, google does it SOOO much better.
as far as VPNs I just rotate them every month if I am in need. I dont really bother anymore. What ever I find that day.
I download TONS of music and film. I just choose wisely when choosing a torrent. I can smell the ones that are being tracked fairly well.
I bank on common sense with technology. I dont even use anti virus. That really says it all. I just choose wisely what I search, how I word it, where I go, even what links I click. I wont even click on links in threads if I smell something fishy. So far so good.
edit on 11 20 2014 by tadaman because: (no reason given)
originally posted by: tadaman
I have been trying ixquick.com for a search engine. I was going to do the email with them ...
ixquick don't do email ... ixquick.com... you must confusing them with someone else.
originally posted by: tadaman
... I can smell the ones that are being tracked fairly well ...
Wouldn't you prefer to see the trackers ... www.youtube.com...
e.g.
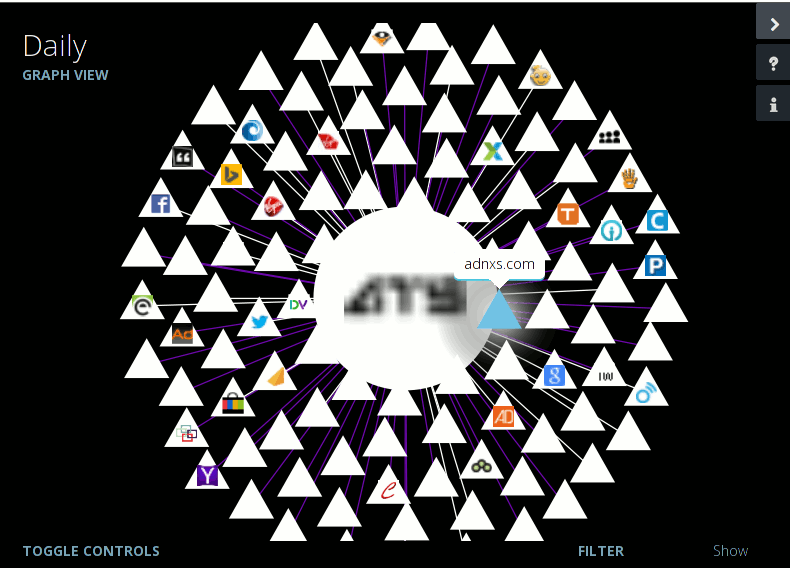
edit on 20-11-2014 by engvbany because: (no reason given)
a reply to: engvbany
Yeah you are right they do not do email. I think it was "start mail". My bad, its been a while. Its one of those new "secure and private" email companies. I was not impressed when they asked for money. Email has been free since, like forever...so no. Enjoy ad revenue and dont ask me for money unless you will come by to pick up cash from me.
I LOVE firefox. Its cool as hell and has so many options. I am not actually using it now. I havent installed it since my last yearly wipe. LOL
Its pretty sad that we have so many different entities tracking our activity...I agree there as well. Seeing who is tracking you isnt really going to change that fact until people start to change their habits. Its best to avoid TOO commercial sites IMO. If you find something useful you have to decide if its worth sharing or if its better kept a secret....I tend to share and move on when things get flooded.
Have a good one.
Yeah you are right they do not do email. I think it was "start mail". My bad, its been a while. Its one of those new "secure and private" email companies. I was not impressed when they asked for money. Email has been free since, like forever...so no. Enjoy ad revenue and dont ask me for money unless you will come by to pick up cash from me.
I LOVE firefox. Its cool as hell and has so many options. I am not actually using it now. I havent installed it since my last yearly wipe. LOL
Its pretty sad that we have so many different entities tracking our activity...I agree there as well. Seeing who is tracking you isnt really going to change that fact until people start to change their habits. Its best to avoid TOO commercial sites IMO. If you find something useful you have to decide if its worth sharing or if its better kept a secret....I tend to share and move on when things get flooded.
Have a good one.
duckduck go search:
DETEKT
-an antigov spyware scanner. It scans for a large list of known gov spyware.It can by no means catch everything,
I just tried it, it didn't find anything though.It is designed by civil rights groups
from the site:
"Amnesty International is partnering with Privacy International, Digitale Gesellschaft and the Electronic Frontier Foundation to release Detekt to the public for the first time."
The problem with viruses/spyware is the software only knows what it is supposed to look for.
If it has a bad known file like Worm1, and others have identified it, it knows to look for it. Worm2 will do the damage if it is on your computer before someone else identifies it as a problem and alerts the software, whom will in turn download the new virus name to your computer.
You are better off changing your pc to strict settings vs relying on software alone imo.
uac in win can be set to inform you of any changes, just move the cursor all the way up. This will stop most of nonsense.
I use spybot s&d for scanning and shredding purposes, Vipre for av/sw, and strict permissions to change anything.
Use caution with anything you download, especially torrents. Most free stuff is for a reason, and it usually is not to benefit you. And scanners are only as good as the updates "bad" lists they use.
So by design, anti virus is always a step behind viruses and there is a large amount of people who create viruses to sell you a solution.
Peace
DETEKT
-an antigov spyware scanner. It scans for a large list of known gov spyware.It can by no means catch everything,
I just tried it, it didn't find anything though.It is designed by civil rights groups
from the site:
"Amnesty International is partnering with Privacy International, Digitale Gesellschaft and the Electronic Frontier Foundation to release Detekt to the public for the first time."
The problem with viruses/spyware is the software only knows what it is supposed to look for.
If it has a bad known file like Worm1, and others have identified it, it knows to look for it. Worm2 will do the damage if it is on your computer before someone else identifies it as a problem and alerts the software, whom will in turn download the new virus name to your computer.
You are better off changing your pc to strict settings vs relying on software alone imo.
uac in win can be set to inform you of any changes, just move the cursor all the way up. This will stop most of nonsense.
I use spybot s&d for scanning and shredding purposes, Vipre for av/sw, and strict permissions to change anything.
Use caution with anything you download, especially torrents. Most free stuff is for a reason, and it usually is not to benefit you. And scanners are only as good as the updates "bad" lists they use.
So by design, anti virus is always a step behind viruses and there is a large amount of people who create viruses to sell you a solution.
Peace
edit on 11 by Mandroid7 because: format/spelling
originally posted by: BuzzCory
An easy way to get rid of Flash cookies (Local Shared Objects, or LS0's) on a Windows computer is to create a batch file that deletes them whenever you execute it ...
Alternatively install "Better Privacy" in FireFox.
edit on
21-11-2014 by engvbany because: (no reason given)
I will use this info because I'm tired of advertising tailored by my previous searches. I miss the old internet, when everything was available and
propaganda and advertising were not on every click. Even the ads on ATS are out of control, sheesh. Suggestions for this issue?
new topics
-
Mass Extinctions May Hold the Key to Life in the Universe
Education and Media: 1 hours ago -
Can we be certain that Jesus Christ was born on December 25th?
Religion, Faith, And Theology: 3 hours ago -
RIP Merrily Harpur British Big Cat Realist
Cryptozoology: 5 hours ago -
Australian mercenary caught and crying as he is a prisoner of war.
Other Current Events: 11 hours ago
top topics
-
Panamanian President-“every square meter” of the Panama Canal belongs to Panama.
New World Order: 12 hours ago, 12 flags -
Australian mercenary caught and crying as he is a prisoner of war.
Other Current Events: 11 hours ago, 10 flags -
NYPD arrests migrant who allegedly set woman on fire on subway train, watched her burn to death
Breaking Alternative News: 15 hours ago, 9 flags -
JILL BIDEN Wants JOE to Punish Democrats Who Forced Him to Leave Office in Disgrace on 1.20.2025.
2024 Elections: 12 hours ago, 9 flags -
RIP Merrily Harpur British Big Cat Realist
Cryptozoology: 5 hours ago, 6 flags -
Mass Extinctions May Hold the Key to Life in the Universe
Education and Media: 1 hours ago, 3 flags -
Can we be certain that Jesus Christ was born on December 25th?
Religion, Faith, And Theology: 3 hours ago, 1 flags
active topics
-
Panamanian President-“every square meter” of the Panama Canal belongs to Panama.
New World Order • 19 • : FullHeathen -
Mass Extinctions May Hold the Key to Life in the Universe
Education and Media • 1 • : BeyondKnowledge3 -
NYPD arrests migrant who allegedly set woman on fire on subway train, watched her burn to death
Breaking Alternative News • 22 • : Solvedit -
Can we be certain that Jesus Christ was born on December 25th?
Religion, Faith, And Theology • 17 • : schuyler2 -
Australian mercenary caught and crying as he is a prisoner of war.
Other Current Events • 32 • : BedevereTheWise -
‘Something horrible’: Somerset pit reveals bronze age cannibalism
Ancient & Lost Civilizations • 19 • : Scratchpost -
RIP Merrily Harpur British Big Cat Realist
Cryptozoology • 2 • : angelchemuel -
The Daily Mail trying to imply “it’s aliens”
Dissecting Disinformation • 15 • : crayzeed -
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 7947 • : underpass61 -
Why isn't Psychiatry involved?
Social Issues and Civil Unrest • 33 • : Xtrozero
13
