It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
5
share:
Back to Stuxnet: the missing link
www.securelist.com
(visit the link for the full news article)
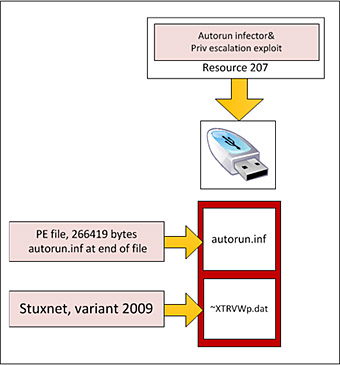
This particular code, which exactly matches the code in resource 207, is currently used by Flame, where it is executed by the “Autorun_infector” module.
The exploit code in the file atmpsvcn.ocx is similar to that which we, Kaspersky Lab, found in the 2010 versions of Stuxnet and which was subsequently addressed by the MS10-073 patch. The code’s style, logic and details of its implementation were the same in the 2009 and 2010 code. Clearly, these two pieces of
Related News Links:
www.abovetopsecret.com
news.cnet.com
news.cnet.com
All i need to say is that this obviously isn't a basement beer drinking nerdy piece of code. Obviously and how ever limited one's computer
comprehension is, it screams government all over.
The interesting part of all this cyber terror and conspiracy is a thread that openly points to who is responsible but for some reason no-one is actually naming them. Could this actually be what all these new cyber terror bills being pushed throughout the world regarding the internet censorship are whats driving and keeping them from being unmasked.
My question is, since the u.s. and israel have been fingered as the main contributors to this recent cyber war/virus, then why isn't anyone actually going head to head with them. As we have seen the recent malware that exploded via twitter links is more or less putting the final piece of the puzzle into play, add to this development the recent introduction of facebook into the big leagues has more or less sealed the deal for current and future cyber wars. Sadly as in real life, there will be casualties and during the recent war's they were referred to as " friendly fire ".
www.securelist.com
(visit the link for the full news article)
The interesting part of all this cyber terror and conspiracy is a thread that openly points to who is responsible but for some reason no-one is actually naming them. Could this actually be what all these new cyber terror bills being pushed throughout the world regarding the internet censorship are whats driving and keeping them from being unmasked.
My question is, since the u.s. and israel have been fingered as the main contributors to this recent cyber war/virus, then why isn't anyone actually going head to head with them. As we have seen the recent malware that exploded via twitter links is more or less putting the final piece of the puzzle into play, add to this development the recent introduction of facebook into the big leagues has more or less sealed the deal for current and future cyber wars. Sadly as in real life, there will be casualties and during the recent war's they were referred to as " friendly fire ".
www.securelist.com
(visit the link for the full news article)
edit on 11-6-2012 by cerebralassassins because: (no reason given)
The deeper you dig, the less light is able to come through.
news.cnet.com...
In a recent thread within ATS it was already said that
The espionage malware has already been updated on some infected machines -- after command-and-control domains were shut down last week, researchers say.
The mysterious Flame malware used domain names registered with fake names to communicate with infected computers in the Middle East for at least four years, researchers said today.
Someone began creating the 86 domains and more than 24 IP addresses that host the command-and-control (C&C) servers as early as 2008, using fake identities and addresses in Austria and Germany to register them with GoDaddy and others, Roel Schouwenberg, senior researcher at Kaspersky Lab, said in a Web conference with reporters this morning. He speculated that stolen credit cards were used for the transactions.
news.cnet.com...
In a recent thread within ATS it was already said that
Google said it planned to issue the warning anytime it picks up malicious–possibly state-sponsored–activity on a user’s account or computer. How does Google know whether an attack is state-sponsored? It won’t say.
www.abovetopsecret.com...
edit on 11-6-2012 by cerebralassassins because: (no reason given)
reply to post by cerebralassassins
The more I read about this, the more I get the feeling the US/Israel contracted Kapersky lab to design the bugger. It makes no sense that Kapersky's reason for even knowing about Flame was due to a call from the UN asking them to take a look at it.
The more I read about this, the more I get the feeling the US/Israel contracted Kapersky lab to design the bugger. It makes no sense that Kapersky's reason for even knowing about Flame was due to a call from the UN asking them to take a look at it.
new topics
-
The daily fail trying to imply “it’s aliens”
The Gray Area: 1 hours ago -
Swarms of tiny 'ant-like' robots lift heavy objects and navigate obstacles
Science & Technology: 2 hours ago -
NYPD Chief Jeffrey Maddrey Resigns - Forced Officers to Give Sex for Overtime Pay and Favors.
Posse Comitatus: 4 hours ago -
The Carpet Coating that Attacked the Environment
Medical Issues & Conspiracies: 8 hours ago -
Microplastics in your drinks
Medical Issues & Conspiracies: 9 hours ago
top topics
-
The Carpet Coating that Attacked the Environment
Medical Issues & Conspiracies: 8 hours ago, 11 flags -
China Working on 'Drone Mothership' Plane
Military Projects: 14 hours ago, 10 flags -
Microplastics in your drinks
Medical Issues & Conspiracies: 9 hours ago, 5 flags -
Happy Rush Day 2024 - 2112
Music: 14 hours ago, 4 flags -
NYPD Chief Jeffrey Maddrey Resigns - Forced Officers to Give Sex for Overtime Pay and Favors.
Posse Comitatus: 4 hours ago, 2 flags -
12-21-24 Usyk-Fury II
World Sports: 17 hours ago, 1 flags -
Swarms of tiny 'ant-like' robots lift heavy objects and navigate obstacles
Science & Technology: 2 hours ago, 1 flags -
The daily fail trying to imply “it’s aliens”
The Gray Area: 1 hours ago, 1 flags
5