It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
originally posted by: freakjive
a reply to: chr0naut
Quick question. I do not know anything about the protocols but I'm curious why this LiteonTe is showing up? I've been worried about a lot of things inside my home.
I found something interesting on the internet; might be nothing, but check and see if any of your cables are branded Liteon.
This is happened to me as well. Im going to guess you have comcast/xfinity or a motorola router/cable box. Check all the cords plugged into your walls for a manufacturer. I bet one or more say LITEON. I believe this company has some kind of working chip inside the powercord. Either working alone to hack/track you or working with comcast, motorola or n s a Change out your liteon cords for motorala made one. It makes no sense comcast would supply a liteon cord for a motorola device. Comcast has motorola cords just ask. Everone should be aware of the following fact: Your cablebox/modem can send a signal through your house via your electricty. Like a netgear jumper. Nowadays these jumpers arent required. This could allow a direct connection to your computer, ipad (the charging plug on ipad works as usb port so when charging a signal can be sent). This works backward too so a hacker with access to your device can back into your router through your electricity. Its like having your computer connected directly to router with ethernet cord. This of course only works if power cords like liteon are used.
Source
edit on 5/3/2017 by trollz because: (no reason given)
originally posted by: trollz
originally posted by: freakjive
a reply to: chr0naut
Quick question. I do not know anything about the protocols but I'm curious why this LiteonTe is showing up? I've been worried about a lot of things inside my home.
I found something interesting on the internet; might be nothing, but check and see if any of your cables are branded Liteon.
This is happened to me as well. Im going to guess you have comcast/xfinity or a motorola router/cable box. Check all the cords plugged into your walls for a manufacturer. I bet one or more say LITEON. I believe this company has some kind of working chip inside the powercord. Either working alone to hack/track you or working with comcast, motorola or n s a Change out your liteon cords for motorala made one. It makes no sense comcast would supply a liteon cord for a motorola device. Comcast has motorola cords just ask. Everone should be aware of the following fact: Your cablebox/modem can send a signal through your house via your electricty. Like a netgear jumper. Nowadays these jumpers arent required. This could allow a direct connection to your computer, ipad (the charging plug on ipad works as usb port so when charging a signal can be sent). This works backward too so a hacker with access to your device can back into your router through your electricity. Its like having your computer connected directly to router with ethernet cord. This of course only works if power cords like liteon are used.
Source
When I searched, I found the same info. It's scary because in my previous research I found items for networking via electricity in web cache before searching for it. I haven't located the item yet.
originally posted by: freakjive
When I searched, I found the same info. It's scary because in my previous research I found items for networking via electricity in web cache before searching for it. I haven't located the item yet.
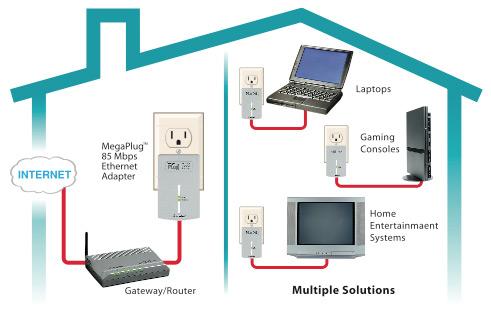
I actually use what's called powerline ethernet where my internet connection is sent and received through the electrical outlet... So networking via electricity is possible since that's literally what I do. HERE is some information about it. I'm really curious if there isn't something to that person's theory that the cables themselves are capturing data. It sounds crazy, but there's way crazier things out there.
I do freelance work in the computer industry so here's my suggestion. Remove your HDD, *Don't Backup your data", so but you will have to consider it
lost and irretrievable. Once the HDD is removed smash it with a heavy hammer, consider the problems you are having, the should be one less
headache.
Have a friend download a clean copy of Ubuntu which can be found at
www.ubuntu.com...
and have him download a copy of Malwarebytes Chameleon, this should work with Ubuntu.
and have your friend download for the firewall issue try ClearOS
which can be found at:
www.clearos.com/clearfoundation/software/clearos-7-community
Next buy a brand new USB Flash Drive...and on when you back up from your friend's download, got into the properties for the executable and make it read only.
For your drive, get yourself a brand new SATA drive and install it into your computer.
Before you start installing anything on your drive such as ubuntu, disconnect the computer in question form the internet. I mean go there physically and disconnect your computer from your cable modem.
You have to be aware that most internet vendors keep their modems without password protection, so they can examine your throughput and signal if you are having problems. So it could be hacked if you new what you were doing.
Install Ubuntu on your system, then install Chamleon, then examine your firewall settings. Once everything is setup for your firewall and Ubuntu is installed.
You should go to Port Forward:
portforward.com...
The site is chuck full of information how to set up your router and cable modem.
Once your router is setup...reconnect the router to you cable modem and you be good to go.
Unless you have done so very naughty things...and the NSA is using there brand spanking new Quantum Computer with a AI they have developed just for it.
Have a friend download a clean copy of Ubuntu which can be found at
www.ubuntu.com...
and have him download a copy of Malwarebytes Chameleon, this should work with Ubuntu.
and have your friend download for the firewall issue try ClearOS
which can be found at:
www.clearos.com/clearfoundation/software/clearos-7-community
Next buy a brand new USB Flash Drive...and on when you back up from your friend's download, got into the properties for the executable and make it read only.
For your drive, get yourself a brand new SATA drive and install it into your computer.
Before you start installing anything on your drive such as ubuntu, disconnect the computer in question form the internet. I mean go there physically and disconnect your computer from your cable modem.
You have to be aware that most internet vendors keep their modems without password protection, so they can examine your throughput and signal if you are having problems. So it could be hacked if you new what you were doing.
Install Ubuntu on your system, then install Chamleon, then examine your firewall settings. Once everything is setup for your firewall and Ubuntu is installed.
You should go to Port Forward:
portforward.com...
The site is chuck full of information how to set up your router and cable modem.
Once your router is setup...reconnect the router to you cable modem and you be good to go.
Unless you have done so very naughty things...and the NSA is using there brand spanking new Quantum Computer with a AI they have developed just for it.
Does your computer have an Intel chip? They have tiny little mini-computers (management engines) built in to the CPU that are untouchable by your OS,
are highly encrypted, and have full network access.
If your computer is compromised at the firmware level - and remember that the CIA were caught intercepting Apple products between distribution centres and sales points - then no amount of installing and re-installing an OS is going to save you, whether you're running Windows (lol), MacOS, or Linux.
If you are being specifically targeted by government agencies or something, you can try to stay one step ahead, but you'll most likely fail. Somebody actually came to my house and connected my computer to the router with an ethernet cable and almost certainly keylogged this laptop. Always assume that any bit of information you send online is public.
If your computer is compromised at the firmware level - and remember that the CIA were caught intercepting Apple products between distribution centres and sales points - then no amount of installing and re-installing an OS is going to save you, whether you're running Windows (lol), MacOS, or Linux.
If you are being specifically targeted by government agencies or something, you can try to stay one step ahead, but you'll most likely fail. Somebody actually came to my house and connected my computer to the router with an ethernet cable and almost certainly keylogged this laptop. Always assume that any bit of information you send online is public.
a reply to: DeepThoughtCriminal
It does in-fact have an intel chip.
Thanks for all the excellent replies. I'm working to complete a lot of the suggestions offered to me today. You guys have been a lot of help.
I really want to figure out who is responsible for this, as it has to be someone close to me. However, I will take the peace of mind knowing it's just stopped over anything else.
It does in-fact have an intel chip.
Thanks for all the excellent replies. I'm working to complete a lot of the suggestions offered to me today. You guys have been a lot of help.
I really want to figure out who is responsible for this, as it has to be someone close to me. However, I will take the peace of mind knowing it's just stopped over anything else.
a reply to: mysterioustranger
I've been trying my hardest to collect as much evidence as possible, as to send them the proper amount to actually have them look into it.
I've been trying my hardest to collect as much evidence as possible, as to send them the proper amount to actually have them look into it.
a reply to: freakjive
Id start by contacting them and asking what TYPE of evidence is needed. Go from there. Ive found them.. when you are sincere(never thought of using FBI and SINCERE in the same sentence)...to be helpful if they understand youre truly concerned and affected by what been happening to you.
Good Luck
Id start by contacting them and asking what TYPE of evidence is needed. Go from there. Ive found them.. when you are sincere(never thought of using FBI and SINCERE in the same sentence)...to be helpful if they understand youre truly concerned and affected by what been happening to you.
Good Luck
new topics
-
My personal experiences and understanding of orbs
Aliens and UFOs: 4 hours ago -
Matt Gaetz ready to go global thermonuclear
US Political Madness: 5 hours ago -
Research paper about plasmoids specifically calls out missing MH370 flight
General Conspiracies: 5 hours ago -
NJ Drones just another Psy-Op
Dissecting Disinformation: 7 hours ago -
Smartest Man in the World Tells His Theory About What Happens At Death
Philosophy and Metaphysics: 10 hours ago
top topics
-
Matt Gaetz ready to go global thermonuclear
US Political Madness: 5 hours ago, 12 flags -
Covid....... Again.
Diseases and Pandemics: 12 hours ago, 11 flags -
Smartest Man in the World Tells His Theory About What Happens At Death
Philosophy and Metaphysics: 10 hours ago, 11 flags -
US Federal Funding set to Expire December 20th. Massive CR on the way.
Mainstream News: 12 hours ago, 8 flags -
NJ Drones just another Psy-Op
Dissecting Disinformation: 7 hours ago, 4 flags -
My personal experiences and understanding of orbs
Aliens and UFOs: 4 hours ago, 3 flags -
and14263 New Account Not the Same Old Me
Introductions: 13 hours ago, 2 flags -
Research paper about plasmoids specifically calls out missing MH370 flight
General Conspiracies: 5 hours ago, 2 flags
active topics
-
Smartest Man in the World Tells His Theory About What Happens At Death
Philosophy and Metaphysics • 23 • : GotterDameron23 -
Trump Cancel trip to New Jersey because of drones
Aliens and UFOs • 77 • : WeMustCare -
Post A Funny (T&C Friendly) Pic Part IV: The LOL awakens!
General Chit Chat • 7923 • : KrustyKrab -
Matt Gaetz ready to go global thermonuclear
US Political Madness • 10 • : WeMustCare -
The truth lets admit it
Aliens and UFOs • 66 • : TowmasterLG -
My personal experiences and understanding of orbs
Aliens and UFOs • 6 • : Arbitrageur -
Covid....... Again.
Diseases and Pandemics • 25 • : Dalamax -
Mood Music Part VI
Music • 3743 • : MRTrismegistus -
Remember These Attacks When President Trump 2.0 Retribution-Justice Commences.
2024 Elections • 117 • : Connector -
Covid Jab and the Alien Invasion
ATS Skunk Works • 20 • : FableGhost2
