It looks like you're using an Ad Blocker.
Please white-list or disable AboveTopSecret.com in your ad-blocking tool.
Thank you.
Some features of ATS will be disabled while you continue to use an ad-blocker.
share:
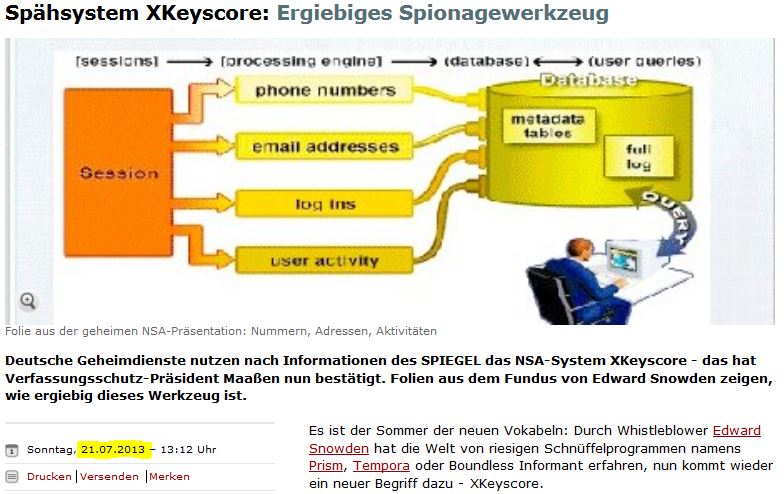
As per the slides the program identifies targets as "someone who uses encryption" and "someone who searches for suspicious stuff."
That's pretty much my job.
That's pretty much my job.
Originally posted by miniatus
They still can't crack https unless they do a man in the middle attack and forge the certificates.. I recommend people use the https anywhere extension.. it enables https on sites that support it even if you don't know they do.. google for example..
Facebook has https capabilities as well.. with that enabled, they'd only be able to get your chat history by requesting it from facebook.. ( who will gladly hand it over )
They don't need to crack it, they ask the companies for the SSL master keys.
The companies denied giving the keys to authorities. But they also denied all the other prism-related stuff.
With the corresponding SSL keys it's easy to decrypt all HTTPS communication.
CNet: Feds put heat on Web firms for master encryption keys
I would like to point something out that may shine a bit of light into why these programs are in existence.
Which leads me to 2 things, one, would be necessity, two would be fear.
Amazingly there are very few (considering how many people have internet) that know the intricacies of how it truly works. So we can scratch out the "regular" user, like someone who watches cats video all day or is looking for the latest news on TMZ.
IMHO there is a looming fear among the internet users/makers/breakers, we have to ask, what?
This isnt a way to see what we do right now, as I am sure who ever this is truly for they already knows, but this is the same actions that survivalists take when building a shelter, sure people know something may happen, but there are still very few that are willing to take heed.
I am sure that those that are aware of how this is working, know what they are looking for, or what they are trying to prevent. So I will keep up my usual internet activities, as I hear more and more about this, I am beginning to be aware that I am far from what they are looking for.
Peace, NRE.
Which leads me to 2 things, one, would be necessity, two would be fear.
Amazingly there are very few (considering how many people have internet) that know the intricacies of how it truly works. So we can scratch out the "regular" user, like someone who watches cats video all day or is looking for the latest news on TMZ.
IMHO there is a looming fear among the internet users/makers/breakers, we have to ask, what?
This isnt a way to see what we do right now, as I am sure who ever this is truly for they already knows, but this is the same actions that survivalists take when building a shelter, sure people know something may happen, but there are still very few that are willing to take heed.
I am sure that those that are aware of how this is working, know what they are looking for, or what they are trying to prevent. So I will keep up my usual internet activities, as I hear more and more about this, I am beginning to be aware that I am far from what they are looking for.
Peace, NRE.
Well according to NSA head General Keith Alexander when he addressed the Black Hat security conference in Las Vegas on Wednesday we don't have to
worry about analysts abusing this power because their people have to take courses and pass exams.
NSA Headman: Don't Worry, Our Watchful Analysts Take Exams
The sheer ignorance and stupidity of that statement stands by itself.
As he was finishing his talk:
NSA Headman: Don't Worry, Our Watchful Analysts Take Exams
He attempted to reassure a skeptical audience by saying "our people have to take courses and pass exams to use this data."
The sheer ignorance and stupidity of that statement stands by itself.
As he was finishing his talk:
Near the close of his speech Alexander said "We stand for freedom." A member of the black-clad, security-aware audience, however, took issue with that assertion. "Bull#!" he shouted
If we don't spy on everybody, HOW WILL WE EVER STOP THE RADICAL MUSLIM TERRORISTS!!!!!!!
reply to post by xavi1000
An interesting detail is that the XKeyscore story broke already ten days ago in the geman version of Spiegel.
link
Also Jimmy Carter's NSA leaks comment was first published in the german Spiegel:
Jimmy Carter: US "has no functioning democracy"
I think this is part of an interesting strategy having to do with this:
German federal election will be held on 22 September 2013
But it also gives us a nearly unprecedented opportunity to observe which of the media are actually still doing any real journalism and reporting and which are just part of the propaganda machine. To stay with the Jimmy Carter story:
This is from another article published the same day! Obviously it is about the submarine USS Jimmy Carter. IMO this article was written on purpose to distract from Jimmy Carter's extremely important statement: “America does not at the moment have a functioning democracy,” Carter's message was not reported in english language MSM and first appeared only in german Der Spiegel. The article about the USS Jimmy Carter has all the necessary keywords to confuse and distract people searching in english for a confirmation of Carter's statement or keep them from discovering it by "accident"! Keywords like: Carter, Snowden, NSA, Spiegel...
The article: The Navy’s underwater eavesdropper
An interesting detail is that the XKeyscore story broke already ten days ago in the geman version of Spiegel.

link
Also Jimmy Carter's NSA leaks comment was first published in the german Spiegel:
Jimmy Carter: US "has no functioning democracy"
I think this is part of an interesting strategy having to do with this:
German federal election will be held on 22 September 2013
But it also gives us a nearly unprecedented opportunity to observe which of the media are actually still doing any real journalism and reporting and which are just part of the propaganda machine. To stay with the Jimmy Carter story:
following Snowden’s disclosures last month, several publications including the Huffington Post and the German Der Spiegel speculated that the Jimmy Carter was aiding the NSA’s surveillance of citizens’ communications in the U.S. and Europe.
This is from another article published the same day! Obviously it is about the submarine USS Jimmy Carter. IMO this article was written on purpose to distract from Jimmy Carter's extremely important statement: “America does not at the moment have a functioning democracy,” Carter's message was not reported in english language MSM and first appeared only in german Der Spiegel. The article about the USS Jimmy Carter has all the necessary keywords to confuse and distract people searching in english for a confirmation of Carter's statement or keep them from discovering it by "accident"! Keywords like: Carter, Snowden, NSA, Spiegel...
The article: The Navy’s underwater eavesdropper
I have a theory.
Everything that has been presented so far as evidence that the NSA is monitoring everything that we are doing on the internet is actually a false front for the establishment of a new internet structure and the ultimate integration of advancing technology into a virtual control system that will allow the government to drop daily 'commands' into the average american's brain and control their most basic human interactions.
Bra in to Brain Interface (BBI)
Hackers backdoor to the human brain
Thought and Emotion Influencing Technology
Everything that has been presented so far as evidence that the NSA is monitoring everything that we are doing on the internet is actually a false front for the establishment of a new internet structure and the ultimate integration of advancing technology into a virtual control system that will allow the government to drop daily 'commands' into the average american's brain and control their most basic human interactions.
Bra in to Brain Interface (BBI)
Hackers backdoor to the human brain
Thought and Emotion Influencing Technology
Someone should just sneak in there and then do a global search on pr0n for all users.
Their servers would be a burning pile of junk after that.
Their servers would be a burning pile of junk after that.
Just dropped these on another thread but some may be useful to this one as well as they deal with cohort and prediction and some of them are way off
the net utilizing some of the most unexpected of things. The point of all these patents as it applies to here is if they can use olfactory, visual,
or audio data to generate a predictable cohort, then it's very feasible that they could easily do the same thing using the internet.
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.informationweek.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.google.com...
www.informationweek.com...
Originally posted by Wrabbit2000
oooo... You beat me by seconds... I actually have my whole article typed and formatted to hit submit. Good job on the fast catch for the NSA's latest program to screw us to the wall and smile while they do it.
Yours would have been better
reply to post by sulaw
i'm with ya on that one I sure do have lots of ....err....information i look thru but honestly.....I only read the articles....on a different side of this coin.....they sure are getting .....pesky....drones....spying.... whats next....mandatory cameras in your house to "protect" you in case of a break in honestly....i'm starting to get very off with their
i'm with ya on that one I sure do have lots of ....err....information i look thru but honestly.....I only read the articles....on a different side of this coin.....they sure are getting .....pesky....drones....spying.... whats next....mandatory cameras in your house to "protect" you in case of a break in honestly....i'm starting to get very off with their
reply to post by merka
:lolh ....they can just look at mine for that but seriously i only read the articles "did you catch that N.S.A operatives.....only the articles "
:lolh ....they can just look at mine for that but seriously i only read the articles "did you catch that N.S.A operatives.....only the articles "
edit on 31-7-2013 by Cogliostro because: can't spell.......sue me..
Originally posted by burntheships
Originally posted by muzzleflash
What I want to know is if we have this really powerful spy system...
Why do we still have terrorist attacks that seem like a surprise?
How did those mass jail breaks happen without them being prepared for it?
What's the point of all this surveillance if it doesn't prevent anything?
Here is one to add onto that list.
If all of what you ask is true, and it is, this started with 9/11.
So if the goal was to surveill us 24/7 and it started with 9/11 then
it seems that the ones surveilling us are responsible for the cause...
You called a spade a spade and I think most people on this thread agree with your analogy I for one was thinking that from the OP to now.
Regards, Iwinder
On slide 15 they give 3 criteria to find a likely terrorist. Speech that's different from the local speech patterns, uses encryption, and searches
suspicious things. I fit all three of those, good to know the NSA considers me a likely terrorist. Atleast I won't be surprised when they show up
at my door.
i see a lot of posts joking around and making fun of this information (i.e. i, uh, hope they don't know about those sites i , oh snap....) but i
havent seen any serious attempts at solving the problem....that is if anyone here actually feels that this is a problem at all. Is anyone here not ok
with this enough to want to make some serious suggestions as to how one can shield themselves from what i think more than a few ppl think is forbidden
by the constitution (the right of a person to be secure in their person and effects) ? I noticed on one of the slides that VPN and PGP are at least
two of the obfuscation techniques people can employ, but little detail was offered as to what variety or strength was sniffable or easily eavesdropped
on.
i tend to oppose things like this on the principle that before being the target of an investigation people should be left alone. This kind of technology is pre-emptive in the way the US pre-emptively goes around the world bombing places before they can bomb us. I know precrime is a wetdream to many in gov and this seems to be a step in that evolution. Anyone here worried about being 'haloed' before you actually do something? Additionally, technology like this begs the question 'whos watching the watchers' and how do you keep someone with a personal vendetta or axe to grind from misusing the ability of this tech?
thoughts? solutions?
i tend to oppose things like this on the principle that before being the target of an investigation people should be left alone. This kind of technology is pre-emptive in the way the US pre-emptively goes around the world bombing places before they can bomb us. I know precrime is a wetdream to many in gov and this seems to be a step in that evolution. Anyone here worried about being 'haloed' before you actually do something? Additionally, technology like this begs the question 'whos watching the watchers' and how do you keep someone with a personal vendetta or axe to grind from misusing the ability of this tech?
thoughts? solutions?
Nice article.
I did a google search for curriculum vitaae xkeyscore.
Come up with this.
jobs.saic.com...
SKIDROW E are they affiliated with the hacking group SKIDROW or past members?
Could this be a clue who was on the project?
Also (site:mil search)
msepjobs.militaryonesource.mil...
There's code names for other similar projects on there.
Can even find the companies afiliiated witht he NSA here.
For example
msepjobs.militaryonesource.mil...
Limbo
I did a google search for curriculum vitaae xkeyscore.
Come up with this.
jobs.saic.com...
The Systems Engineer will provide support for the compartment systems that encompass the SKIDROWE systems
SKIDROW E are they affiliated with the hacking group SKIDROW or past members?
Could this be a clue who was on the project?
Also (site:mil search)
msepjobs.militaryonesource.mil...
There's code names for other similar projects on there.
Configure and understand and fine-tune the data flow of signals through processing systems such as DARKQUEST, WEALTHYCLUSTER, and XKEYSCORE
Can even find the companies afiliiated witht he NSA here.
For example
msepjobs.militaryonesource.mil...
msepjobs.militaryonesource.mil...
Limbo
edit on 31-7-2013 by Limbo because: (no reason given)
Can anyone answer the question... why all the dots along the coast of antartica?
reply to post by instigatah
I can name ways around the technology, but I don't know how to stop it, and no method of circumventing it is perfect (and in many cases requires lots of additional effort). Like was mentioned in the slides (and already assumed by many) they track by MAC address, which means you not only need a network card that's not tied to your name, but you need a way to spoof the address. You can buy a network card for cash in a computer store and install it (it's a bit more involved for laptops). It's 5 minutes on google to learn how to spoof it. At that point it becomes a bit more of a community effort. My preferred method is to use other peoples wifi (and have my own wifi for others to freely use as well). This has the benefit of removing the ability to trace IP's to people. They can still trace to a general area, though (about 700 feet if you're using a router to bridge a weak wifi signal).
Using encryption seems good, but as we've learned NSA policy is to save anything that's encrypted precisely because it's encrypted. Your mundane data is less likely to be searched if it's unencrypted and looks like everything else in the giant haypile. If it's something that needs encrypting, then use it but be aware the NSA will hang onto it until they crack it and determine if it's a threat. Even if it takes 20 years for decryption technology to catch up. It's trading privacy now for a guarantee they will check that data specifically in the future.
If you have something that absolutely must be encrypted and you need to be certain no one will ever break it, look into a Vernam Cipher with your random number string not coming from a seed (which can be reverse engineered) but rather coming from measured radioactive decay which is actually random. That's a lot of effort to make an uncrackable message that's not hugely important though.
As for your final question, there's not really an answer. The existence of these types of programs is a massive violation of civil liberties. There's no real effective protection from it, you just have to accept that it's going to happen until the day the program is shut down by one method or another.
I can name ways around the technology, but I don't know how to stop it, and no method of circumventing it is perfect (and in many cases requires lots of additional effort). Like was mentioned in the slides (and already assumed by many) they track by MAC address, which means you not only need a network card that's not tied to your name, but you need a way to spoof the address. You can buy a network card for cash in a computer store and install it (it's a bit more involved for laptops). It's 5 minutes on google to learn how to spoof it. At that point it becomes a bit more of a community effort. My preferred method is to use other peoples wifi (and have my own wifi for others to freely use as well). This has the benefit of removing the ability to trace IP's to people. They can still trace to a general area, though (about 700 feet if you're using a router to bridge a weak wifi signal).
Using encryption seems good, but as we've learned NSA policy is to save anything that's encrypted precisely because it's encrypted. Your mundane data is less likely to be searched if it's unencrypted and looks like everything else in the giant haypile. If it's something that needs encrypting, then use it but be aware the NSA will hang onto it until they crack it and determine if it's a threat. Even if it takes 20 years for decryption technology to catch up. It's trading privacy now for a guarantee they will check that data specifically in the future.
If you have something that absolutely must be encrypted and you need to be certain no one will ever break it, look into a Vernam Cipher with your random number string not coming from a seed (which can be reverse engineered) but rather coming from measured radioactive decay which is actually random. That's a lot of effort to make an uncrackable message that's not hugely important though.
As for your final question, there's not really an answer. The existence of these types of programs is a massive violation of civil liberties. There's no real effective protection from it, you just have to accept that it's going to happen until the day the program is shut down by one method or another.
Originally posted by Aazadan
On slide 15 they give 3 criteria to find a likely terrorist. Speech that's different from the local speech patterns, uses encryption, and searches suspicious things. I fit all three of those, good to know the NSA considers me a likely terrorist. Atleast I won't be surprised when they show up at my door.
I don't use encryption but that's not because I was unaware of the possibility of this kind of surveillance. On the contrary, I was very aware of the potential and chose to not use any sort of method to cloak my identity because I've always been a little * ever since grade school. According to the school officials that is. That said, I've been speckling out stuff publicly for the last couple years. Was expecting the knock on the door but it hasn't happened yet. Maybe I'm off the mark at what I'm seeing or finding. The worst thing that has occurred so far has been links and access or even previews to documents disappearing and often times, that could've just been simply a private entity not liking a particular source of unwanted attention.
Somebody knocking on the door and promptly disappearing happens a lot in movies but really, unless we're in some position of power where we can actually get a whole lot of people listening to us, I don't think they'd view it as being a risk worth taking. Loved ones would complain and loudly. A lot easier to close those open windows when what you're dealing with is basically just a whisper. Could be wrong though. The little * in me doesn't care though.
reply to post by WhiteAlice
The knocks at the door don't happen yet (and really, will never be a knock at the door, it will be no knock raids). We're becoming a police state, but people don't disappear off the streets... yet. At the rate we're going though that's in our future.
The knocks at the door don't happen yet (and really, will never be a knock at the door, it will be no knock raids). We're becoming a police state, but people don't disappear off the streets... yet. At the rate we're going though that's in our future.
new topics
-
MH370 Again....
Disaster Conspiracies: 22 minutes ago -
Are you ready for the return of Jesus Christ? Have you been cleansed by His blood?
Religion, Faith, And Theology: 2 hours ago -
Chronological time line of open source information
History: 3 hours ago -
A man of the people
Diseases and Pandemics: 5 hours ago -
Ramblings on DNA, blood, and Spirit.
Philosophy and Metaphysics: 5 hours ago -
4 plans of US elites to defeat Russia
New World Order: 7 hours ago -
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events: 10 hours ago
top topics
-
Israeli Missile Strikes in Iran, Explosions in Syria + Iraq
World War Three: 13 hours ago, 17 flags -
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events: 10 hours ago, 7 flags -
Iran launches Retalliation Strike 4.18.24
World War Three: 13 hours ago, 6 flags -
12 jurors selected in Trump criminal trial
US Political Madness: 13 hours ago, 4 flags -
4 plans of US elites to defeat Russia
New World Order: 7 hours ago, 4 flags -
A man of the people
Diseases and Pandemics: 5 hours ago, 3 flags -
Chronological time line of open source information
History: 3 hours ago, 2 flags -
Are you ready for the return of Jesus Christ? Have you been cleansed by His blood?
Religion, Faith, And Theology: 2 hours ago, 1 flags -
Ramblings on DNA, blood, and Spirit.
Philosophy and Metaphysics: 5 hours ago, 1 flags -
MH370 Again....
Disaster Conspiracies: 22 minutes ago, 0 flags
active topics
-
Israeli Missile Strikes in Iran, Explosions in Syria + Iraq
World War Three • 72 • : DBCowboy -
Fossils in Greece Suggest Human Ancestors Evolved in Europe, Not Africa
Origins and Creationism • 67 • : strongfp -
Thousands Of Young Ukrainian Men Trying To Flee The Country To Avoid Conscription And The War
Other Current Events • 16 • : Cvastar -
Are you ready for the return of Jesus Christ? Have you been cleansed by His blood?
Religion, Faith, And Theology • 10 • : TruthJava -
Not Aliens but a Nazi Occult Inspired and then Science Rendered Design.
Aliens and UFOs • 13 • : Ophiuchus1 -
12 jurors selected in Trump criminal trial
US Political Madness • 36 • : Cvastar -
MH370 Again....
Disaster Conspiracies • 0 • : Cvastar -
So I saw about 30 UFOs in formation last night.
Aliens and UFOs • 34 • : Arbitrageur -
4 plans of US elites to defeat Russia
New World Order • 27 • : andy06shake -
ChatGPT Beatles songs about covid and masks
Science & Technology • 22 • : iaylyan
